DDOS-attack-based prevention method and device
A DDOS, detection method technology, applied in the field of communication, can solve problems such as low efficiency and insufficient resource utilization, and achieve the effect of solving security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
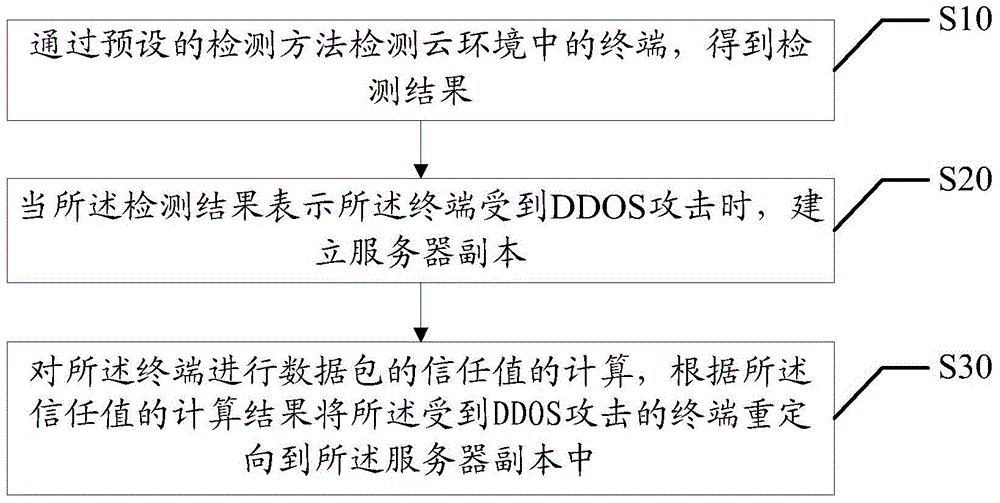
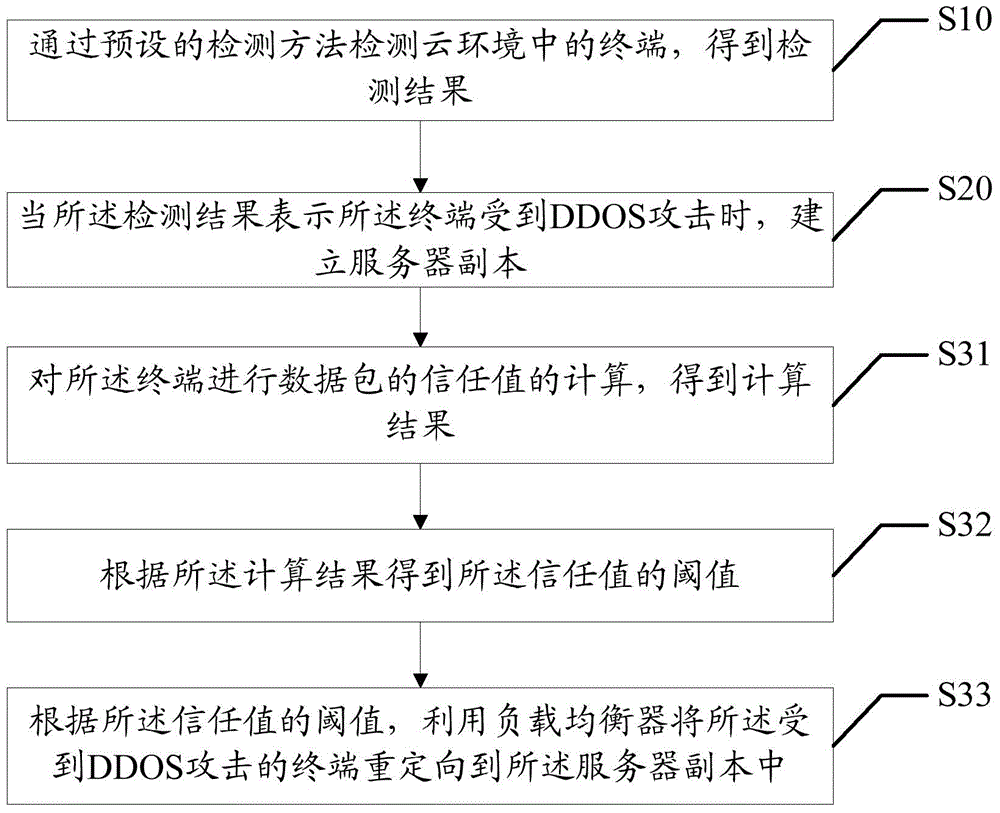
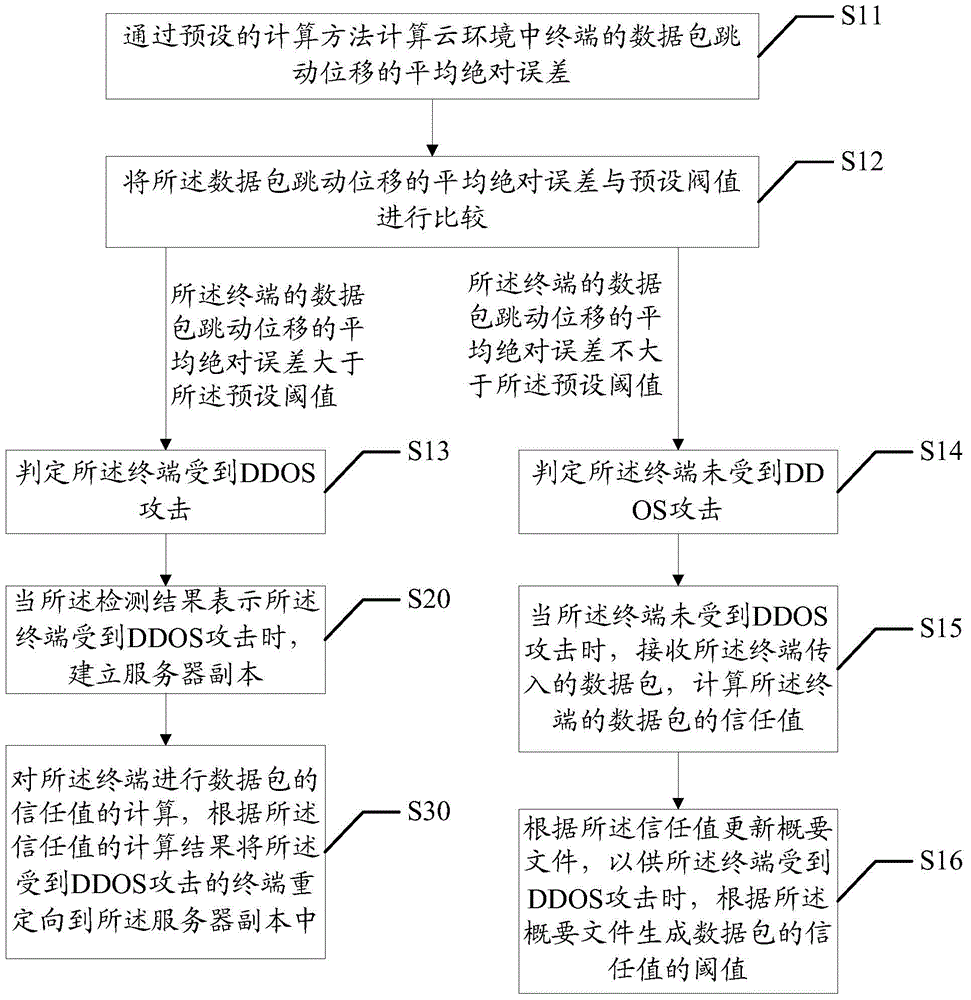
[0049] The main solution of the embodiment of the present invention is: detect the terminal in the cloud environment by a preset detection method, and obtain the detection result; when the detection result indicates that the terminal is attacked by DDOS, establish a server copy; calculating the trust value of the data packet, and redirecting the terminal under DDOS attack to the server copy according to the calculation result of the trust value. By detecting that a terminal in the cloud environment is attacked by a DDOS, a server copy is established, the trust value of the data packet is calculated for the terminal, and the terminal subjected to the DDOS attack is redirected to the server copy according to the calculated trust value, Separate benign endpoints from attackers. Solve the security threat of DDOS attack t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com