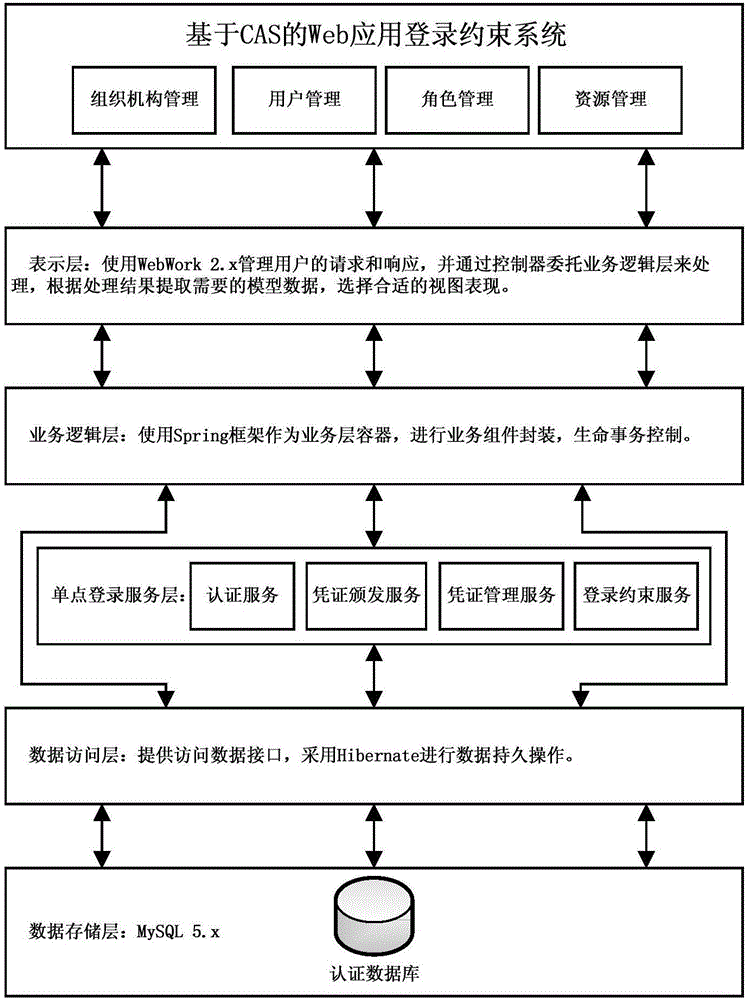
Web system log in constraint method based on single sign-on
A single sign-on, web application technology, applied in transmission systems, electrical components, etc., can solve problems such as flexible configuration of different application systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
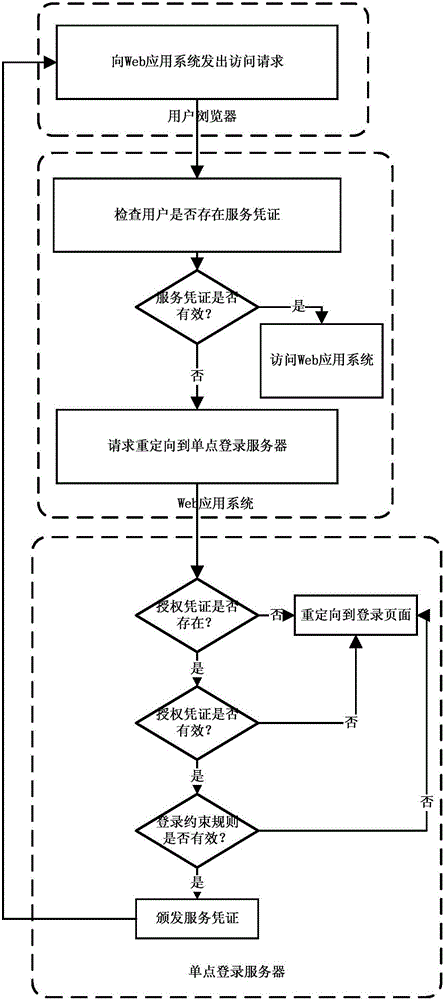
[0029] Such as figure 1 Shown, method of the present invention comprises the steps:
[0030] Step 1: The user browser sends an access request to the Web application system;
[0031] Step 2: The web application system checks whether the service certificate exists in the user's browser, if it exists, then go to step 9, otherwise, go to step 3;
[0032] Step 3: Redirect the access request to the single sign-on server;
[0033] Step 4: The single sign-on server checks whether the authorization certificate exists in the user's browser, if it exists, then go to step 5, otherwise, go to step 8;
[0034] Step 5: The single sign-on server verifies the validity of the authorization credential, if valid, go to step 6, otherwise, go to step 8;
[0035] Step 6: The single sign-on server verifies whether the user's login constraint rules for the web application system are valid, if valid, go to step 7, otherwise, go to step 8;
[0036] Step 7: The single sign-on server will issue a serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com