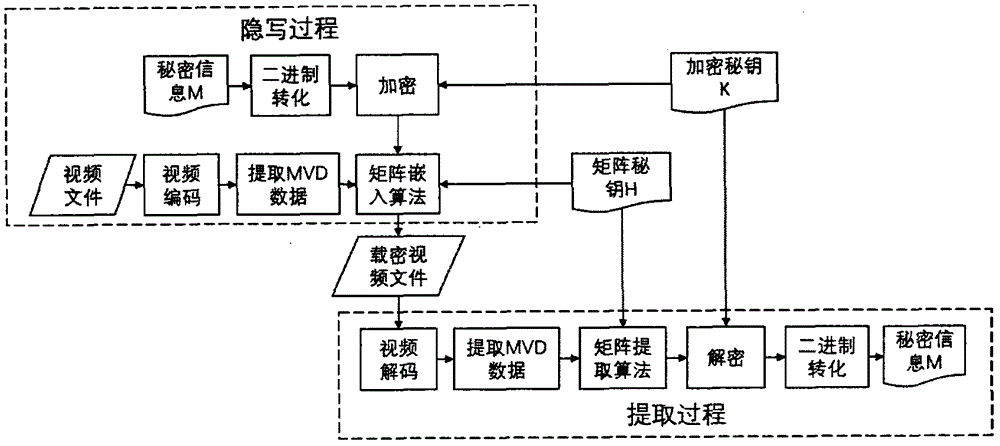
Video steganography algorithm based on motion vector difference
A technology of motion vector and video steganography, which is applied in digital video signal modification, electrical components, image communication, etc., can solve the problems that the statistical histogram of video motion information has a great influence, and the temporal-spatial correlation of motion vectors is easy to be destroyed, so as to maintain the temporal-spatial Correlation Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
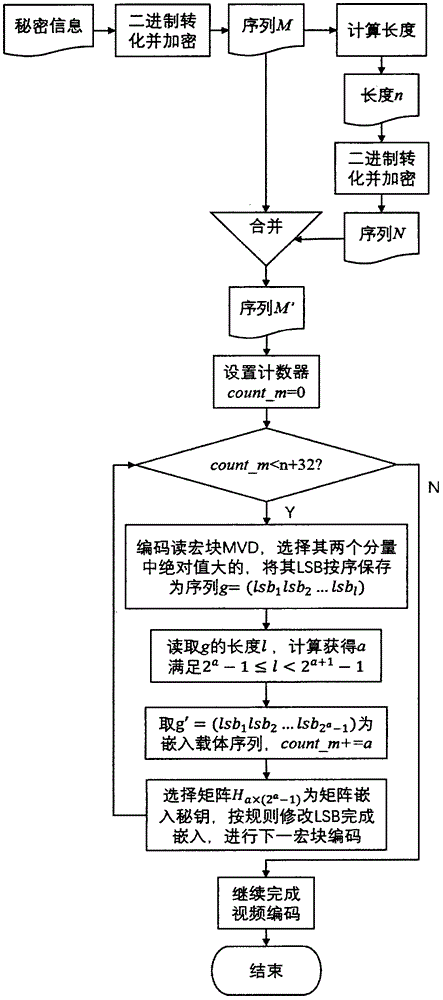
[0057] Embodiment 1 of the present invention introduces the steganographic embedding process of matrix coding based on the motion vector residual, and the process of selecting the secret key for matrix embedding. The specific steps are as follows: figure 2 shown, including:
[0058] (1) Convert the secret information to be embedded into binary form and encrypt to obtain the sequence M=(m 1 m 2 ...m n ), n is the length of secret information M. Convert n into binary form and encrypt to get sequence N=(n 1 no 2 ...n 32 ). Get the sequence to be embedded M'=N+M=(n 1 no 2 ...n 32 m 1 m 2 ...m n ).
[0059] (2) Setting the counter count_m=0 indicates the number of embedded information bits.
[0060] (3) Read and judge count_m, if count_m
[0061] (4) Read the MVD sequence of the current coded macroblock in order, select the one with the larger absolute value in the horizontal and vertical components of the MVD as the embeddin...
Embodiment 2
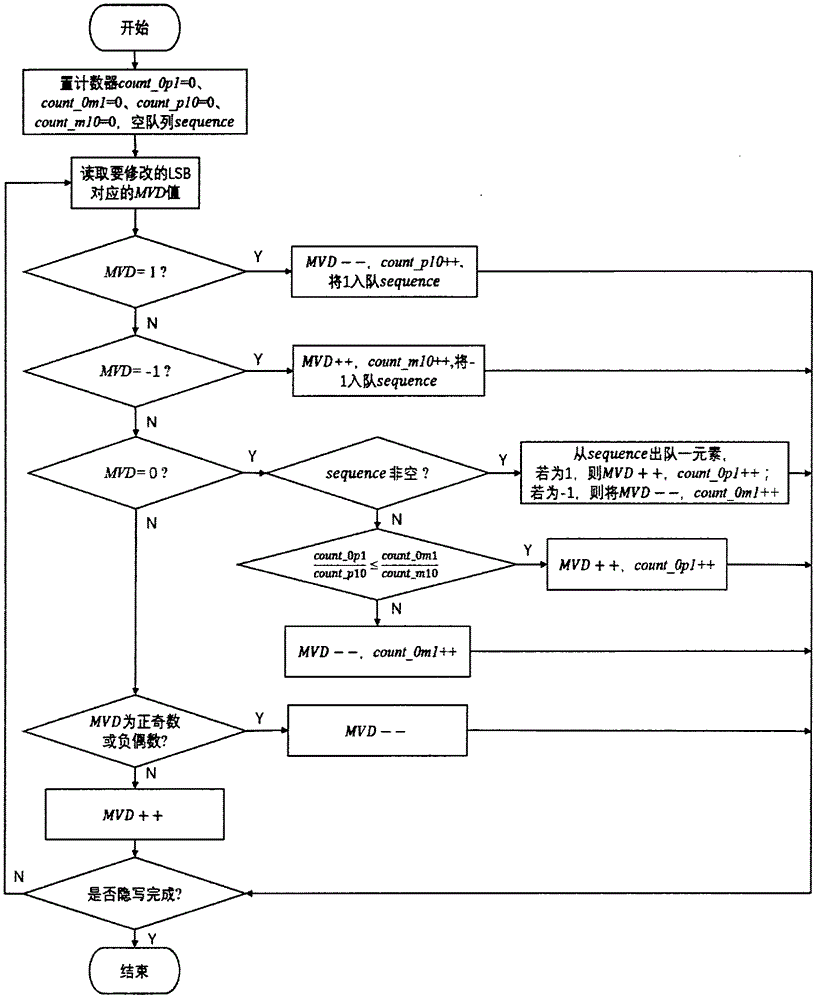
[0066] Embodiment 2 of the present invention introduces the LSB modification rule for maintaining the statistical characteristics of motion vector residuals, and its specific steps are as follows image 3 shown, including:
[0067] (1) Set counters count_0p1=0, count_0m1=0, count_p10=0, count_m10=0, empty queue sequence.
[0068] (2) If MVD b is 1, the MVD b -1 becomes 0, count_p10++, enqueues 1 into the sequence.
[0069] (3) If MVD b is -1, the MVD b +1 becomes 0, count_m10++, and -1 is added to the queue sequence.
[0070] (4) If MVD b is 0, and the sequence is not empty, then the sequence will dequeue an element, if the element is 1, then the MVD b +1 becomes 1, count_0p1++; if the element is -1, then MVD b -1 becomes -1, count_0m1++.
[0071] (5) If MVD b is 0, and the sequence is empty, judge the counter, if then the MVD b +1 becomes 1, count_0p1++; otherwise, MVD b -1 becomes -1, count_0m1++.
[0072] (6) If MVD b Not -1, 0, 1, and MVD b is positive odd...
Embodiment 3
[0075] Embodiment 3 of the present invention introduces the process that the receiving party uses the same matrix embedding key selection and matrix embedding code extraction rules to restore and extract secret information after receiving the encrypted video file. The specific steps are as follows: Figure 4 shown, including:
[0076] (1) Set counters count_n=0, count_m=0;
[0077] (2) If count_n<32, execute (3), otherwise execute (5);
[0078] (3) Read the MVD sequence of the current decoding macroblock in order, select the one with the larger absolute value in the horizontal and vertical components of the MVD as the carrier, and save its LSB information as a sequence G=(lsb 1 lsb 2 ... lsb l ), l is the length of sequence G. Compute the qualified a such that 2 a -1≤la+1 -1, take is the carrier sequence of secret information;
[0079] (4) Take the corresponding line a 2 a -1 column binary matrix calculate m'=(m 1 m 2 ...m a ) is the information sequence extrac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com