XSS and CSRF based Web attack defense system and method
A defense system, the technology of this system, applied in transmission systems, electrical components, etc., can solve problems such as hindering technological development, and achieve the effects of low false positive rate, reduced false positive rate, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Below in conjunction with accompanying drawing and embodiment describe in detail:
[0034] 1. System
[0035] 1. Overall
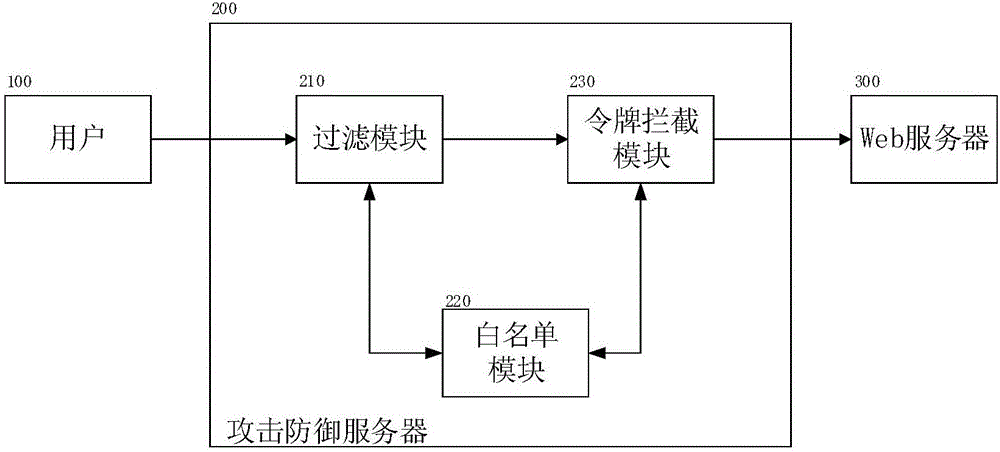
[0036] Such as figure 1 , the system includes a user 100 and a Web server 300;
[0037] An attack defense server 200 is provided, and the attack defense server 200 includes a filtering module 210, a whitelist module 220 and a token interception module 230;
[0038] Its interaction relationship is:
[0039] The user 100, the filtering module 210, the token intercepting module 230 and the Web server 300 interact in sequence;
[0040] The whitelist module module 220 interacts with the filter module 210 and the token intercept module 230 respectively.
[0041] 2. Function block
[0042] 1) User 100
[0043] User 100 is a mobile terminal, including a mobile phone and a notebook.
[0044] 2) Attack defense server 200
[0045] It is embedded with a filter module 210 , a whitelist module 220 and a token interception module 230 .
[0046] (1) Filtr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com