Illegal wireless AP (Access Point) detection method and device
A detection method and a detection device technology, which are applied in the field of network security, can solve the problems of undetectable illegal APs and hysteresis, and achieve the effect of improving the detection rate and reducing security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
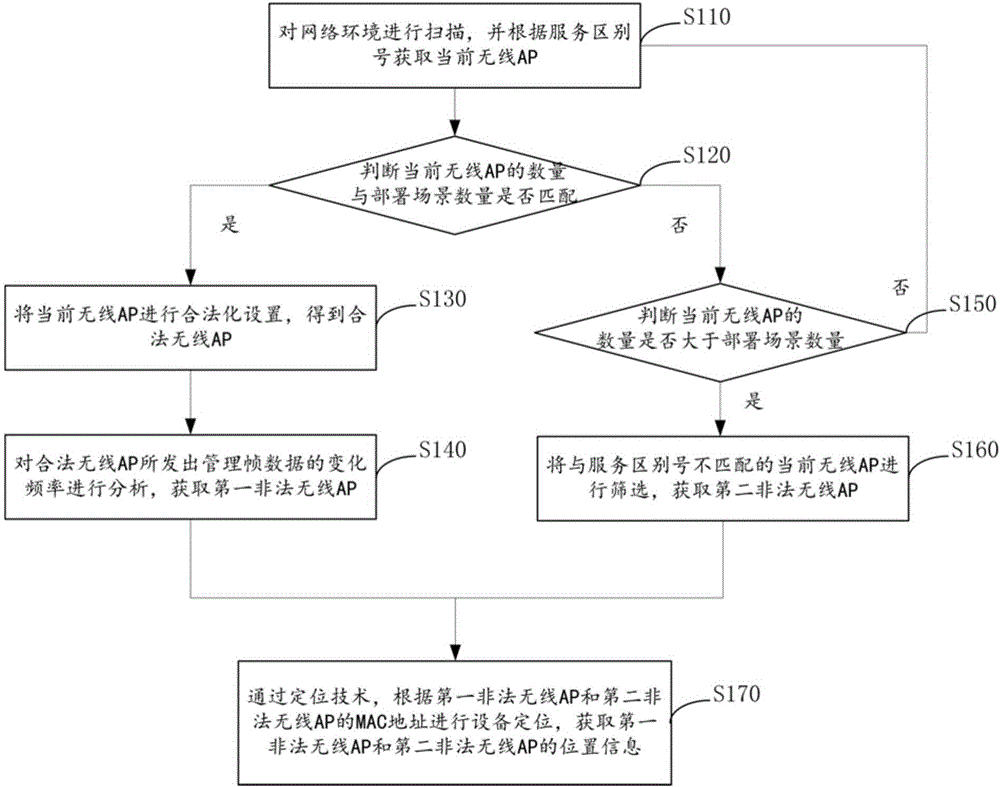
[0060] figure 1 It is a flowchart of a method for detecting an illegal wireless AP provided in Embodiment 1 of the present invention.
[0061] refer to figure 1 , the illegal wireless AP detection method comprises the steps:
[0062] Step S110, scan the network environment, and obtain the current wireless access point AP according to the service distinction number;
[0063] Specifically, all surrounding APs are scanned through the Wi-Fi module supporting the monitoring mode, and a B / S (Browser / Server, browser / server) structure is adopted to display all surrounding wireless APs through the browser. The specific display information includes SSID (Service Set IDentifier, service distinction number), MAC address, device manufacturer, protection method, encryption algorithm, authentication method of surrounding wireless APs, whether to broadcast SSID, whether to enable WPS (Wi-Fi ProtectedSetup, Wi-Fi protection settings). The Wi-Fi module here is a small portable device that c...
Embodiment 2
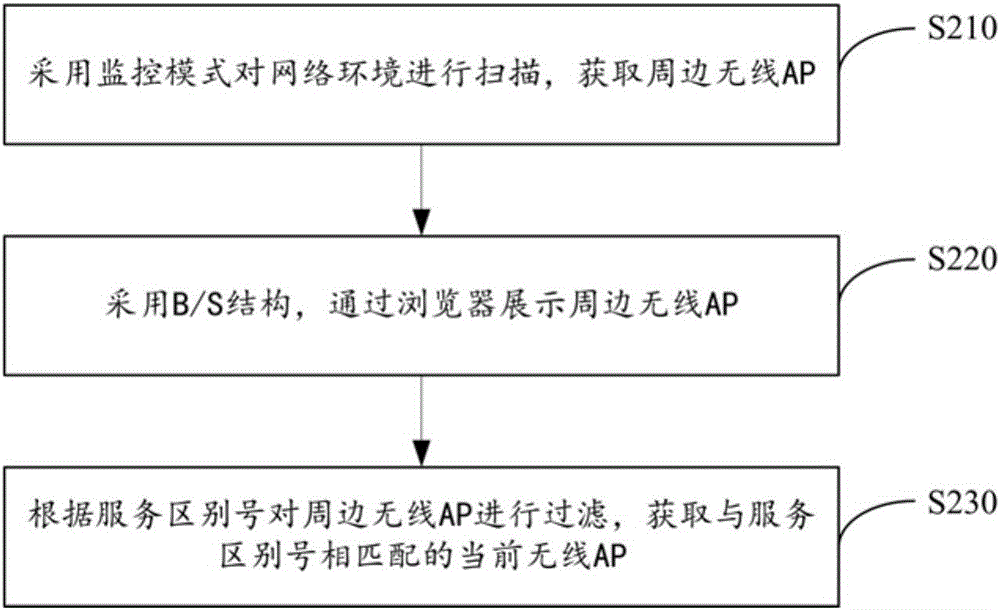
[0078] Such as figure 2 As shown, the acquisition method of step S110 in the illegal wireless AP detection method includes the following steps:
[0079] Step S210, using the monitoring mode to scan the network environment to obtain surrounding wireless APs;
[0080] Step S220, using a B / S structure to display peripheral wireless APs through a browser;
[0081] In step S230, the surrounding wireless APs are filtered according to the service distinction number, and the current wireless APs matching the service distinction number are obtained.
[0082] Specifically, the Wi-Fi module uses monitoring mode to scan all surrounding wireless APs in the network environment, and adopts a B / S structure to display surrounding wireless APs through a browser. The specific display information includes SSID, MAC address, etc. According to the service distinction number created by the individual, such as "yidong-00", the surrounding wireless APs are filtered to get all the current wireless A...
Embodiment 3
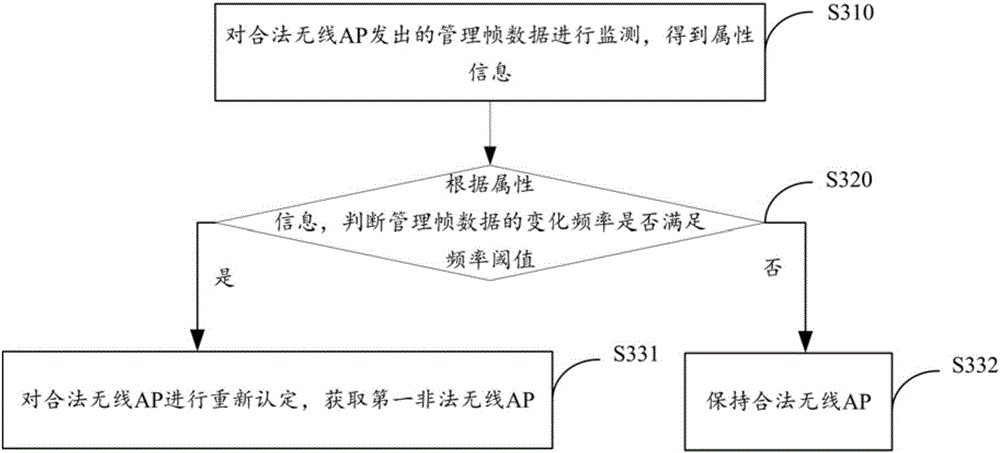
[0084] Such as image 3 As shown, the acquisition method of step S140 in the illegal wireless AP detection method includes the following steps:
[0085] Step S310, monitoring the management frame data sent by the legitimate wireless AP to obtain attribute information;
[0086] Step S320, according to the attribute information, judge whether the change frequency of the management frame data satisfies the frequency threshold; if yes, execute step S331; if not, execute step S332;
[0087] Step S331, re-identify the legal wireless AP, and obtain the first illegal wireless AP;
[0088] Step S332, keep the legal wireless AP.
[0089] Specifically, the Wi-Fi module monitors the management frame data sent by the MAC of the legitimate wireless AP to obtain attribute information, which includes BI, SSID, and supported rate. According to the analyzed attribute information, judge whether the change frequency of the management frame data sent by the legal wireless AP is greater than a c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com