A user behavior trust evaluation method and system based on improved ahp
A user and behavior technology, applied in the field of network security, can solve the problems of ignoring user historical behavior trust considerations, lack of accuracy and comprehensiveness of evaluation results, and inability to obtain comprehensive information of user trust evaluation, so as to reduce one-sidedness and ensure safety and credibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
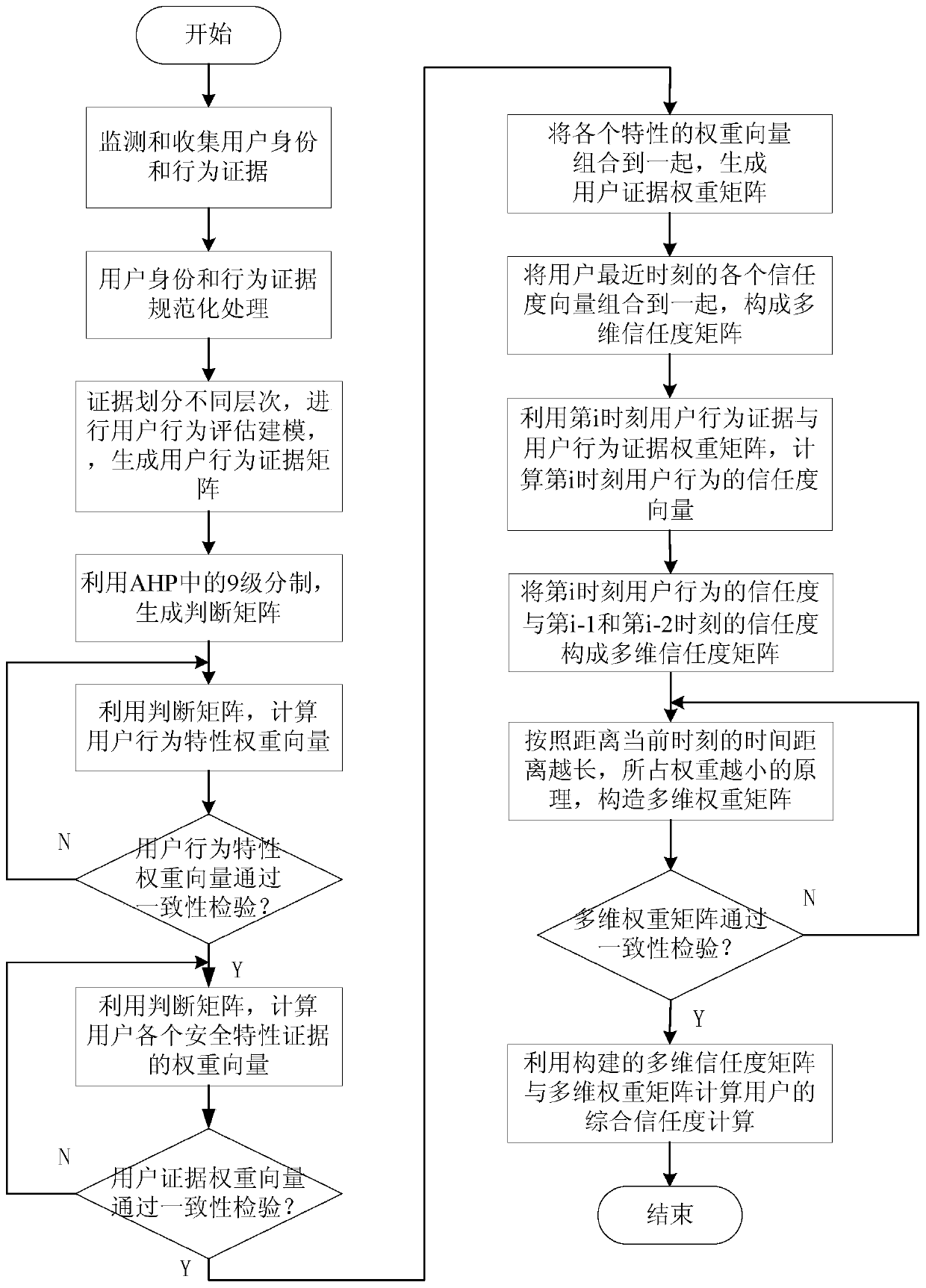
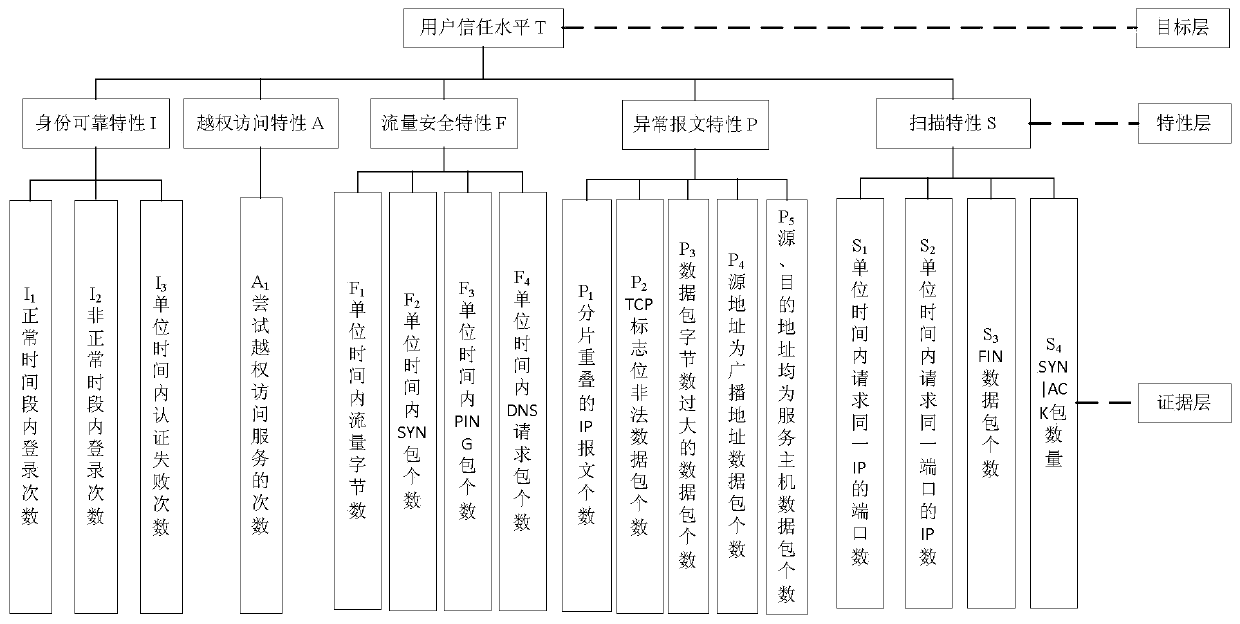
[0023] Based on the improved AHP user behavior trust evaluation and decision-making method, the invention uses the AHP principle to add time factors to collect and model the evidence of the user's historical continuous time, constructs the user behavior evidence matrix and weight matrix of the continuous time, and calculates the comprehensive security of the user. The evaluation results make the security evaluation for network users more accurate and comprehensive, thereby effectively ensuring the security and credibility of the network.
[0024] In order to make the objectives, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be described in detail below with reference to the accompanying drawings.
[0025] A user behavior trust evaluation and decision-making method based on improved AHP, the process of the method is as follows figure 1 As shown, the specific process is:
[0026] Step 201, using a security mon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com