Method and device for achieving voice encryption based on DMR (Digital Mobile Radio) standard
A voice encryption and standard technology, applied in the electronic field, can solve the problem of inability to perform voice encryption, and achieve the effect of improving user experience and security performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
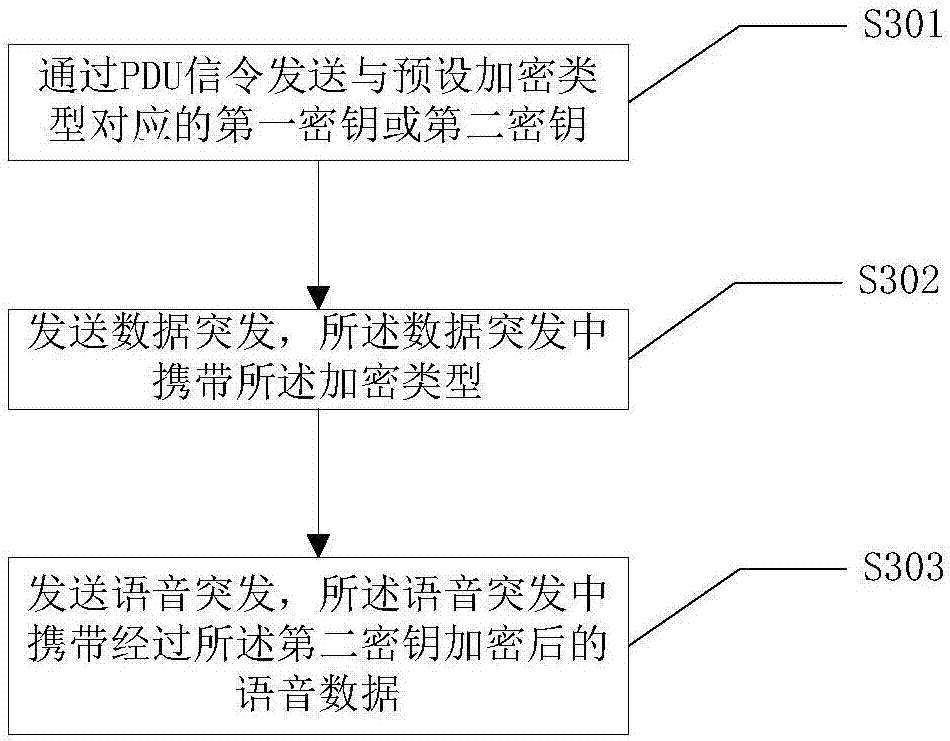
[0047] refer to image 3 , image 3 A flowchart of a method for implementing voice encryption based on the DMR standard provided by the first embodiment of the present invention, the method includes:
[0048] S301. Send a first key or a second key corresponding to a preset encryption type through PDU signaling, where the second key is a key generated according to a generation rule agreed with the other party according to the first key ;
[0049] S302. Send a data burst, where the data burst carries the encryption type;
[0050] S303. Send a voice burst, where the voice burst carries voice data encrypted by the second key.
[0051] Take the following two types of encryption as an example: the first type that uses a fixed call key for encryption, and the second type that updates the call key before each call and uses the updated call key to encrypt the call. The first type of value means that all calls use the same key within a period of time, and the second type means that ...
no. 2 example
[0070] In this embodiment, the first type of encryption method is used for voice encryption. refer to Figure 5 , the method for implementing voice encryption based on the DMR standard mainly includes:
[0071] S501. Acquire a first key and a second key corresponding to the first type in the following manner.
[0072] The 32-byte key input by the user is used as the first key, and the AES algorithm is performed with the preset 32-byte first character string to obtain the 32-byte second key.
[0073] S502. Send the second key generated in step S501 to the other party through PDU signaling.
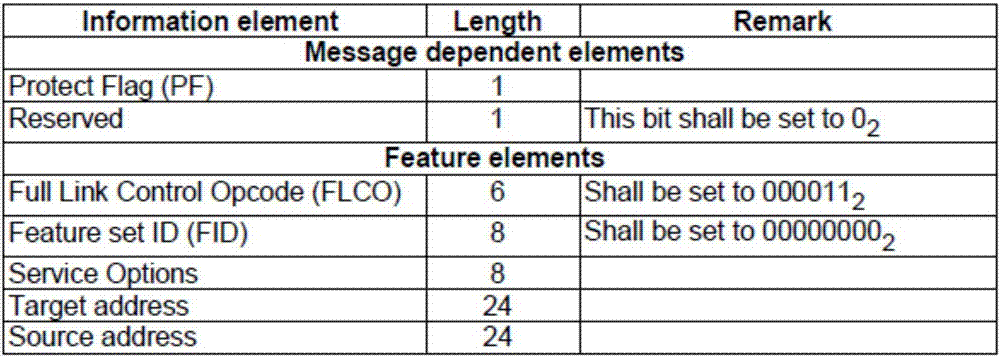
[0074] If it is a single call, the second key is added to the Target address of the PDU signaling for transmission;
[0075] If it is a group call, the second key is added to the Group address of the PDU signaling for transmission.
[0076] After the second key is sent to the other party, the other party saves it. The second key can be used for all calls between the two parties within a...
no. 3 example
[0084] In this embodiment, the second type of encryption is used for voice encryption. refer to Figure 6 , the method for implementing voice encryption based on the DMR standard mainly includes:
[0085] S601. Acquire a first key and a second key corresponding to the second type in the following manner.
[0086] Cycle the preset 3-byte variable key in byte order to determine the first key for this call;
[0087] XORing the first key and the 32-byte key input by the user;
[0088] Perform the AES algorithm on the XOR result and the preset second character string of 32 bytes to obtain a 32-byte key as the second key of this call.
[0089] S602. Send the first key obtained in step S601 to the other party through PDU signaling.
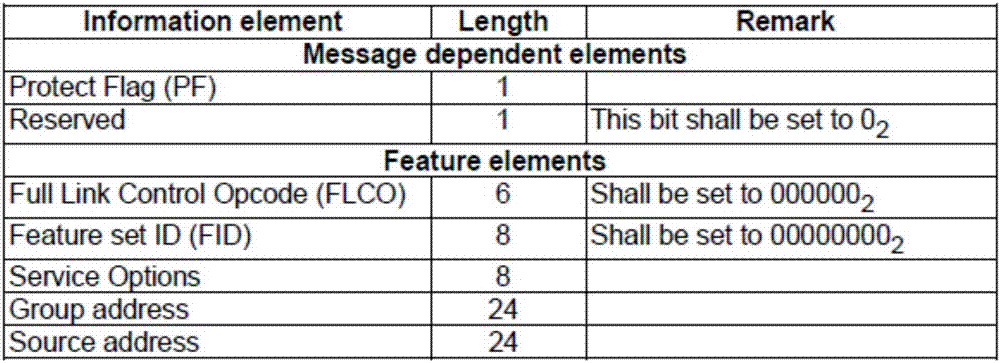
[0090] If it is a single call, the first key is added to the Target address of the PDU signaling for transmission;
[0091] If it is a group call, the first key is added to the Group address of the PDU signaling for transmission.
[0092] Preferabl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com