Intelligent password signature identity authentication method and system
A smart password and identity authentication technology, which is applied in the field of smart password signature identity authentication and authentication, can solve the problems of identity forgery and identity denial, and the difficulty of judicial evidence collection, and achieve the effect of ensuring uniqueness and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
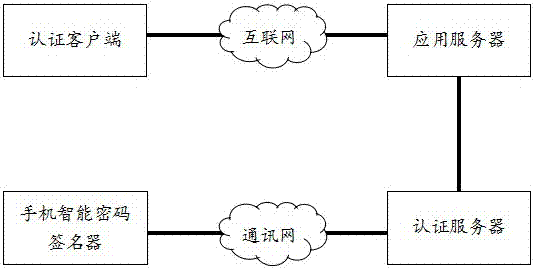
[0015] Described in this embodiment is a method and system for identifying and authenticating an intelligent cryptographic signature, the method and system comprising: a smart cryptographic signature device for a mobile phone, a communication network, an authentication server, an authentication client, the Internet, and an application server, such as figure 1shown. The mobile phone intelligent password signer includes a time seed that changes the dynamic password within 60 seconds, and the user uses the rule key and the dynamic password to calculate the signature and transform the smart password through the rule key operation key and the rule key operation module. Communication networks include mobile communication networks, the Internet, wired telephone networks, local area networks, wireless communication networks, and all communication networks that are used in the public domain and can communicate with each other are included. The authentication server controls all remote ...
Embodiment 2
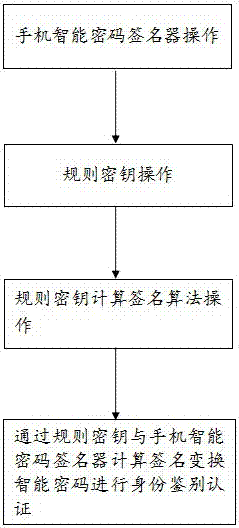
[0024] This embodiment is an improvement in the step of using the rule key and the smart password signer of the mobile phone to calculate the signature and transform the smart password for identity authentication and authentication in the smart password signature identity authentication method and system described in the first embodiment, as follows: image 3 shown.
[0025] The sub-steps in the step of performing identity authentication and authentication by calculating signatures and transforming smart passwords with the rule key and the smart password signer of the mobile phone include:
[0026] Log in to the authentication client to enter the user account and use the rule key and the dynamic password of the smart password signer of the mobile phone to calculate the signature through the rule key operation key and the rule key operation module. The smart password is sent to the authentication server to verify the signature identity authentication, and the calculated signatur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com