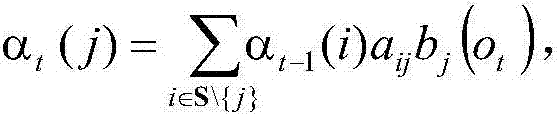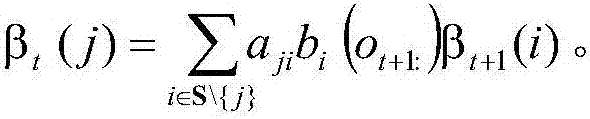Malicious web crawler detection method based on hidden Markov model (HMM)
A hidden Markov and web crawler technology, applied in data exchange networks, special data processing applications, instruments, etc., can solve the problem of exposure of business secrets, difficulty in distinguishing benign and malicious web crawlers, and regardless of the adverse impact of crawling behavior on the website And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
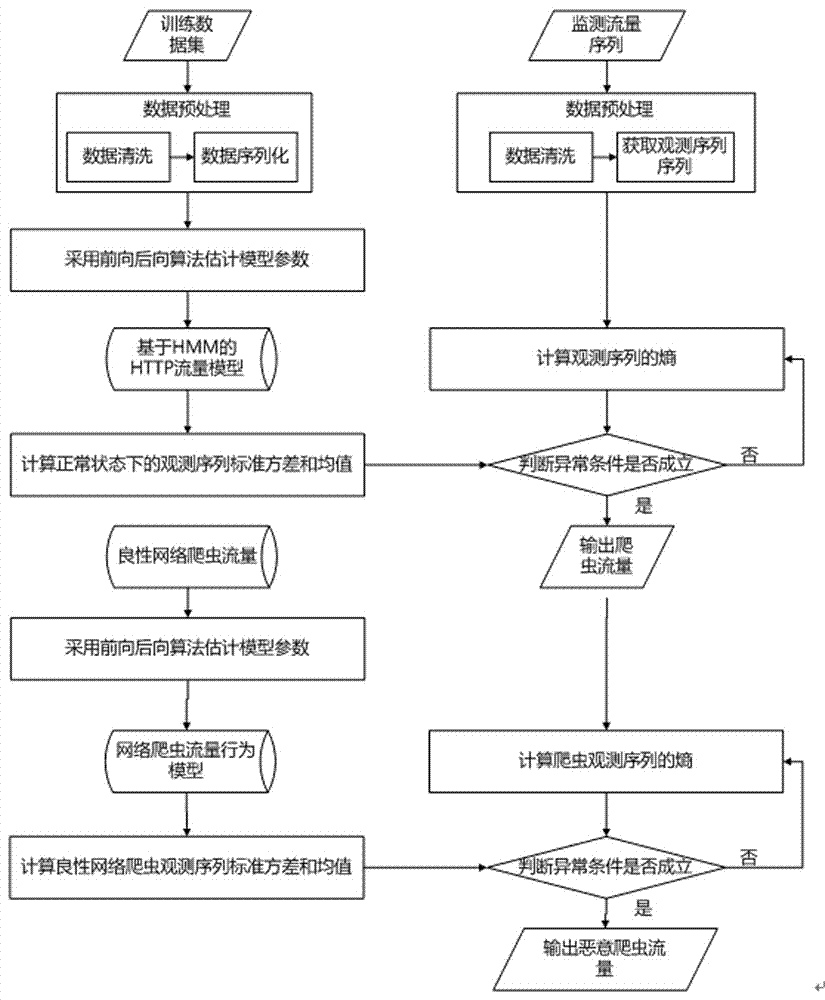
[0041] Implementation process
[0042] Step 1: preprocessing of training data to generate a training data set for web crawler detection;
[0043] Step 2: Use the forward-backward algorithm to estimate the parameters of the model, and obtain the HMM-based HTTP traffic model;
[0044] Step 3: Calculate the entropy of the monitoring sequence using the trained model;
[0045] Step 4: Calculate the traffic anomaly detection amount |μ-μ 0 |;
[0046] Step 5: By judging |μ-μ 0 |≥3σ 0 Whether it is established to identify web crawler traffic;
[0047] Step 6: Extract the training data set for benign crawler detection;
[0048] Step 7: Estimate the model parameters of the benign web crawler using the forward-backward algorithm;
[0049] Step 8: use the trained benign web crawler model to calculate the entropy of the web crawler sequence;
[0050] Step 9: Calculate the amount of anomaly detection |μ-μ 0 |;
[0051] Step 10: By judging |μ-μ 0 |≥3σ 0 true to identify malicious...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com