IEC104 communication access control method
An access control and control domain technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as inability to prevent attacks and firewalls that cannot be identified, and achieve the effect of preventing deceptive attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
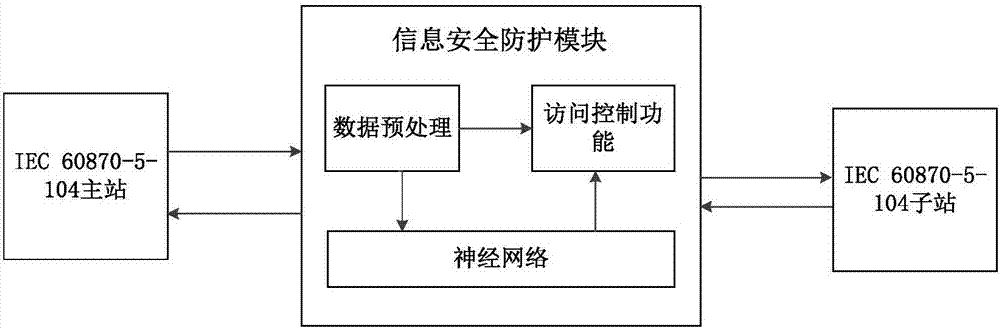
[0034] figure 1 It is the IEC 60870-5-104 communication topology diagram.
[0035] In this example, if figure 1 As shown, the IEC 60870-5-104 communication topology includes a master station and multiple sub-stations. Adding communication access control between the master station and the sub-stations can effectively prevent attacks.
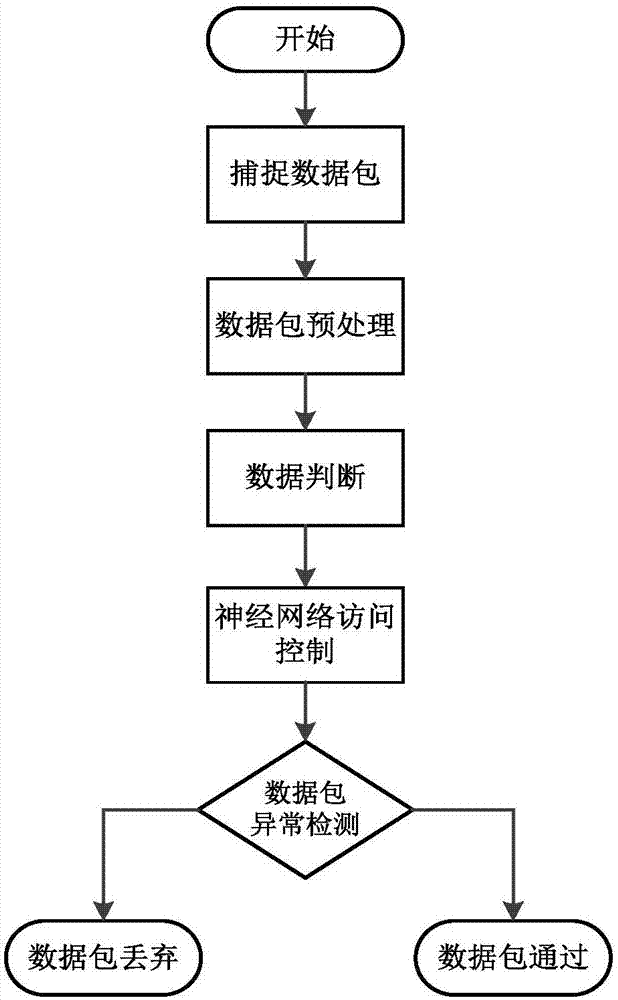
[0036] Combine below figure 1 A kind of IEC 60870-5-104 communication access control method of the present invention is described in detail, as image 3 shown, including the following steps:
[0037] S1, capture data packets
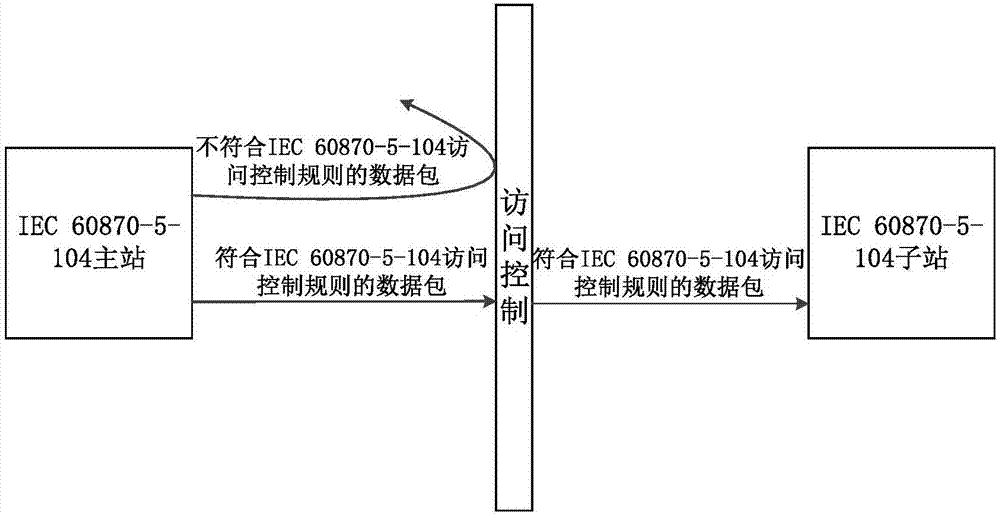
[0038] Such as figure 2 As shown, the Ethernet packet capture tool is used between the master station and the slave station to capture IEC 60870-5-104 data packets according to the IEC 60870-5-104 protocol port, so that the set access control eliminates the IEC60870-free - a data packet of the 5-104 protocol; in this embodiment, the IEC60870-5-104 data packet is captured through the port 2404 of the IEC 60870-5-104 p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com