Access control method for dnp communication based on neural network
An access control and neural network technology, applied in the field of industrial control information security, can solve problems such as unrecognizable and unpreventable firewalls, and achieve the effects of improving security and reliability, ensuring security, and preventing fraudulent attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
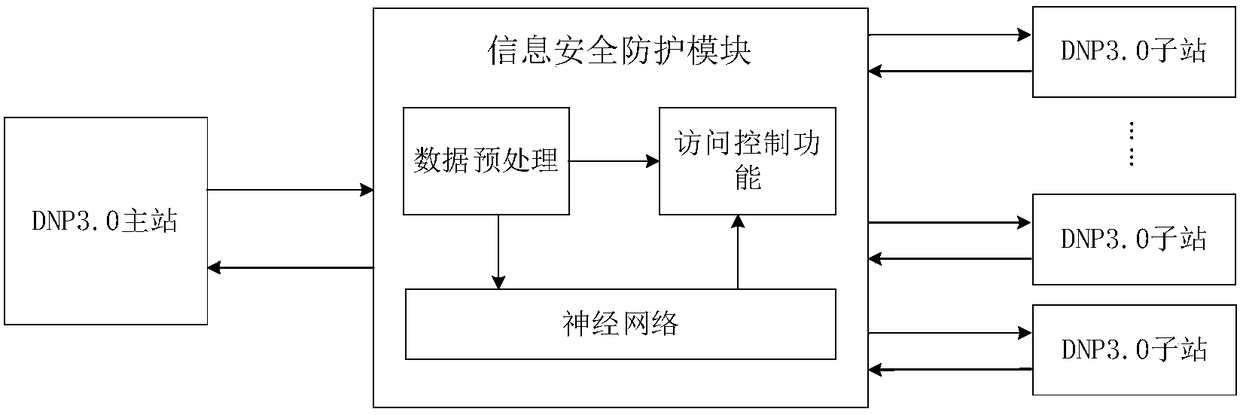
[0031] figure 1 It is a DNP3.0 communication topology diagram.
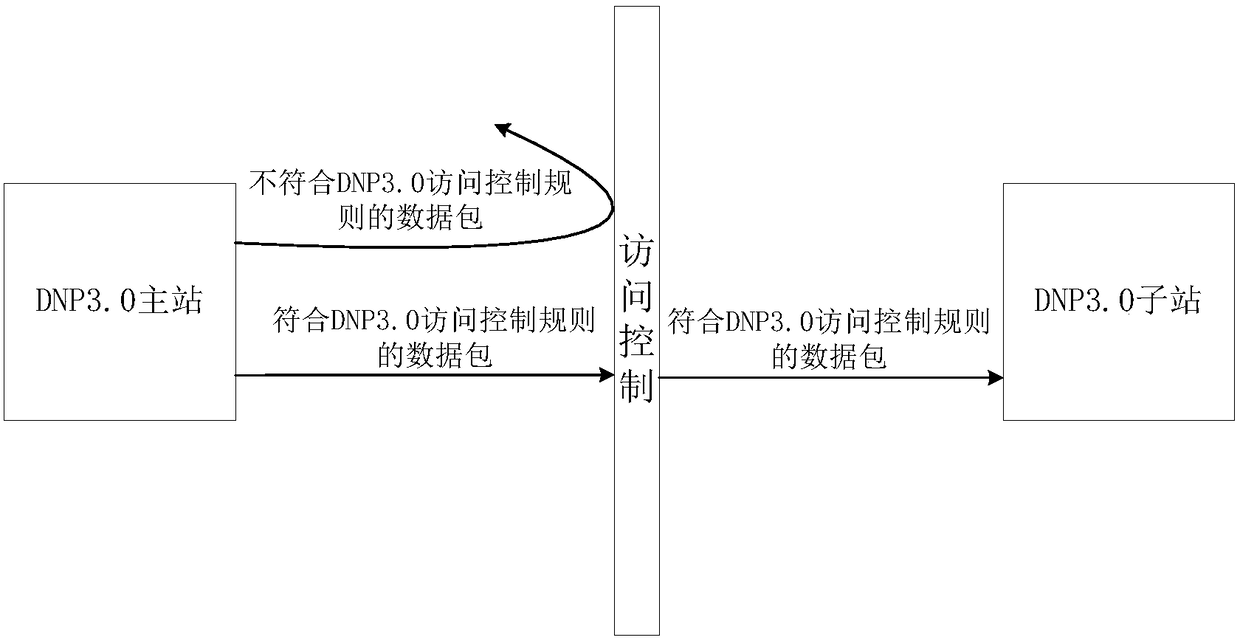
[0032] In this example, if figure 1 As shown, the DNP3.0 communication topology includes a master station and multiple sub-stations. Adding communication access control between the master station and the sub-stations can effectively prevent attacks without changing the network topology of the control system. The principle is as follows figure 2 As shown, this improves the security and reliability of the DNP3.0 communication process and ensures the safety of the power system.
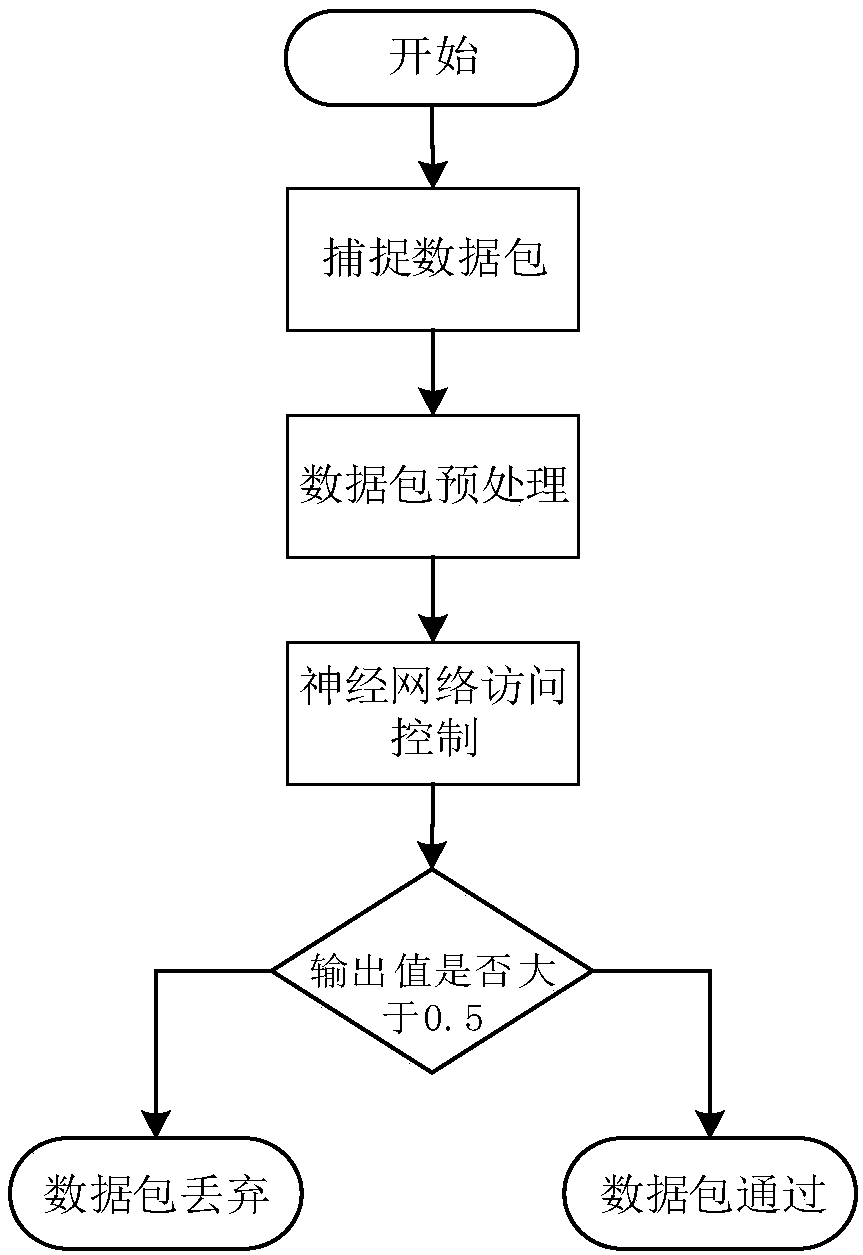
[0033] Combine below image 3 The DNP communication access control method based on neural network described in the present invention is described in detail, specifically comprises the following steps:
[0034] S1, capture data packets
[0035] Use the Netfilter framework of Linux between the master station and the slave station to capture all DNP3.0 data packets within a unit time T on the DNP3.0 protocol port, so that the data packets...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com