Machine learning based intrusion detection method of industrial control system
An industrial control system and intrusion detection technology, applied in transmission systems, electrical components, platform integrity maintenance, etc., can solve key industrial control process damage, unauthorized access to industrial system functions, core data theft, etc., to improve The effect of communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
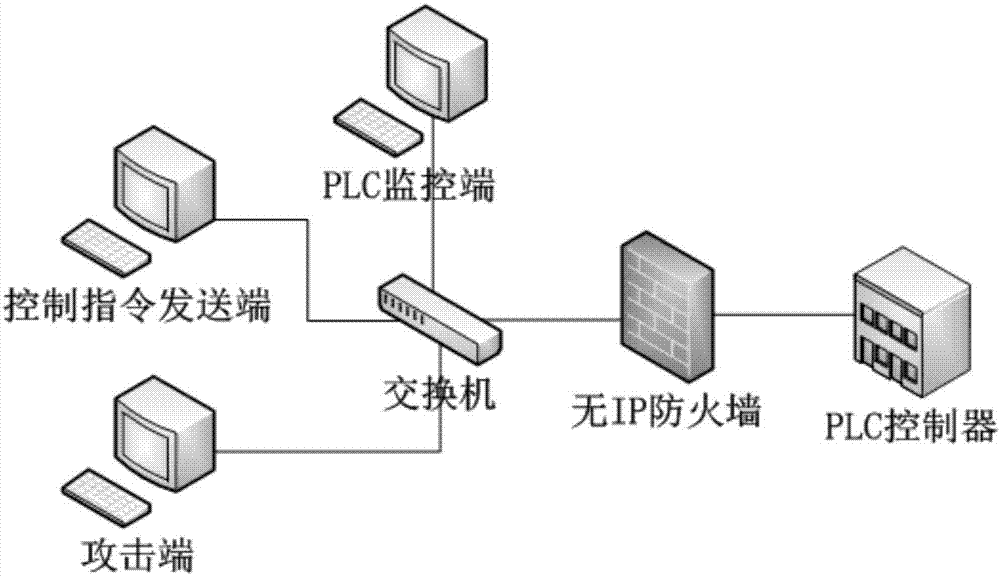
[0024] figure 1 It is a topological structure diagram of the machine learning-based industrial control system intrusion detection of the present invention.
[0025] In this example, if figure 1 As shown, all communication traffic between the control end and the execution end will pass through the firewall, and the intrusion detection module is inside the firewall, which includes an intrusion detection module and a deep packet analysis module.
[0026] Combine below figure 1 A machine learning-based industrial control system intrusion detection method of the present invention is described in detail, which specifically includes the following steps:
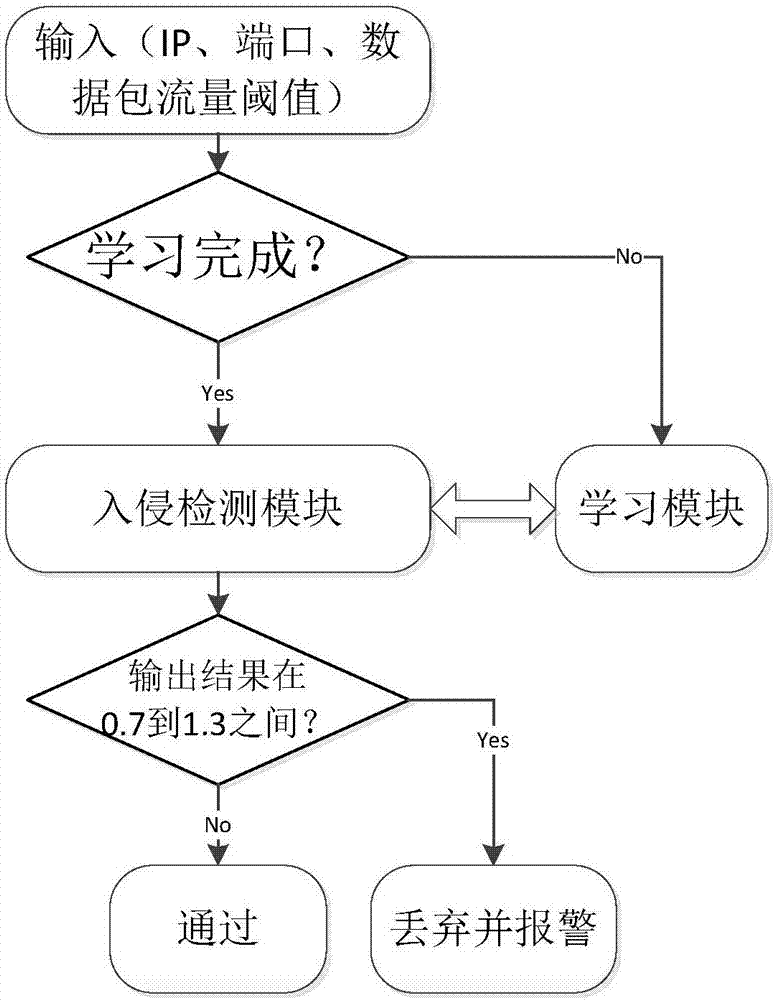
[0027] S1. Detect, identify and analyze the data packets of the communication of the industrial control system to be detected;
[0028] It is assumed that there are M groups of control terminal and execution terminal combinations in the industrial control system, and the communication cycle is divided into X unit time;
[0029] ...
example
[0040] Use the control software as the client, execute the software server, and set it to read data every 1 minute.
[0041] For a period of communication, the legal sample value we selected is:
[0042] x 1 =(19216810147,10036,19216810133,502,011008,30)
[0043] x 2 =(19216810147,10098,19216810133,502,011009,45)
[0044] x 3 =(19216810147,10023,19216810133,502,011010,50)
[0045] x 4 =(19216810125,10211,19216810133,502,011010,19)
[0046] Choose an illegal sample value:
[0047] x 1 =(19216810147,10036,19216810133,502,011008,100)
[0048] x 2 =(19216810147,10098,19216810133,502,011009,10)
[0049] x 3 =(19216810147,10023,19216810133,502,011010,198)
[0050] x 4 =(19216810125,10211,19216810133,502,011010,201)
[0051] Output result: For this model, when the data obtained by the intrusion detection module is (19216810147, 10036, 19216810133, 502, 011008, 30), input the intrusion detection model, normally the source IP address is 19216810147, the source port numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com