Open RFID access control system and its processing method for access detection
An access control system and RFID tag technology, applied in the field of open RFID access control systems, can solve problems such as restricting access control throughput efficiency, unfavorable personnel experience, and limited throughput, and achieve the effects of eliminating physical constraints, optimizing personnel experience, and saving time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
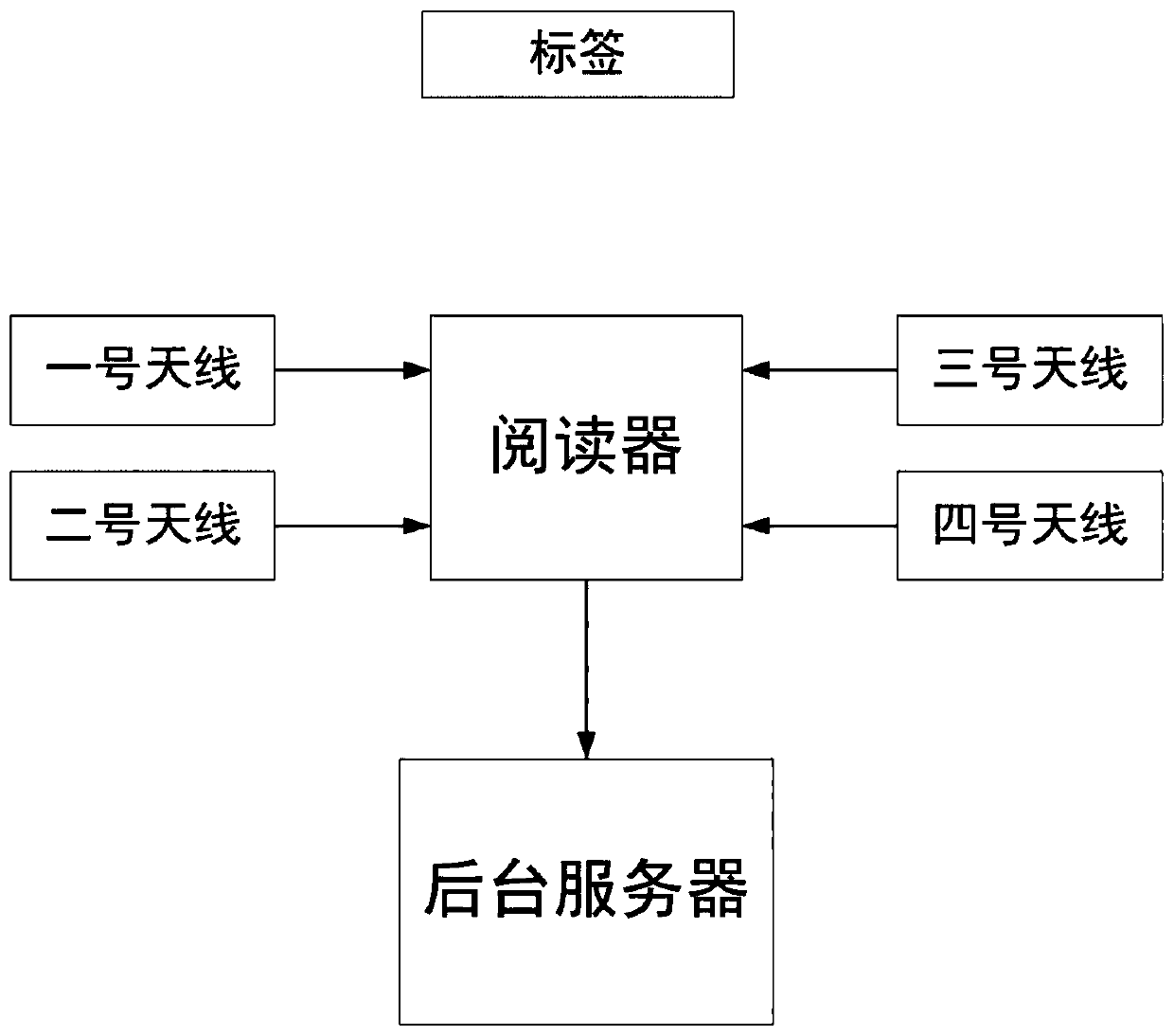
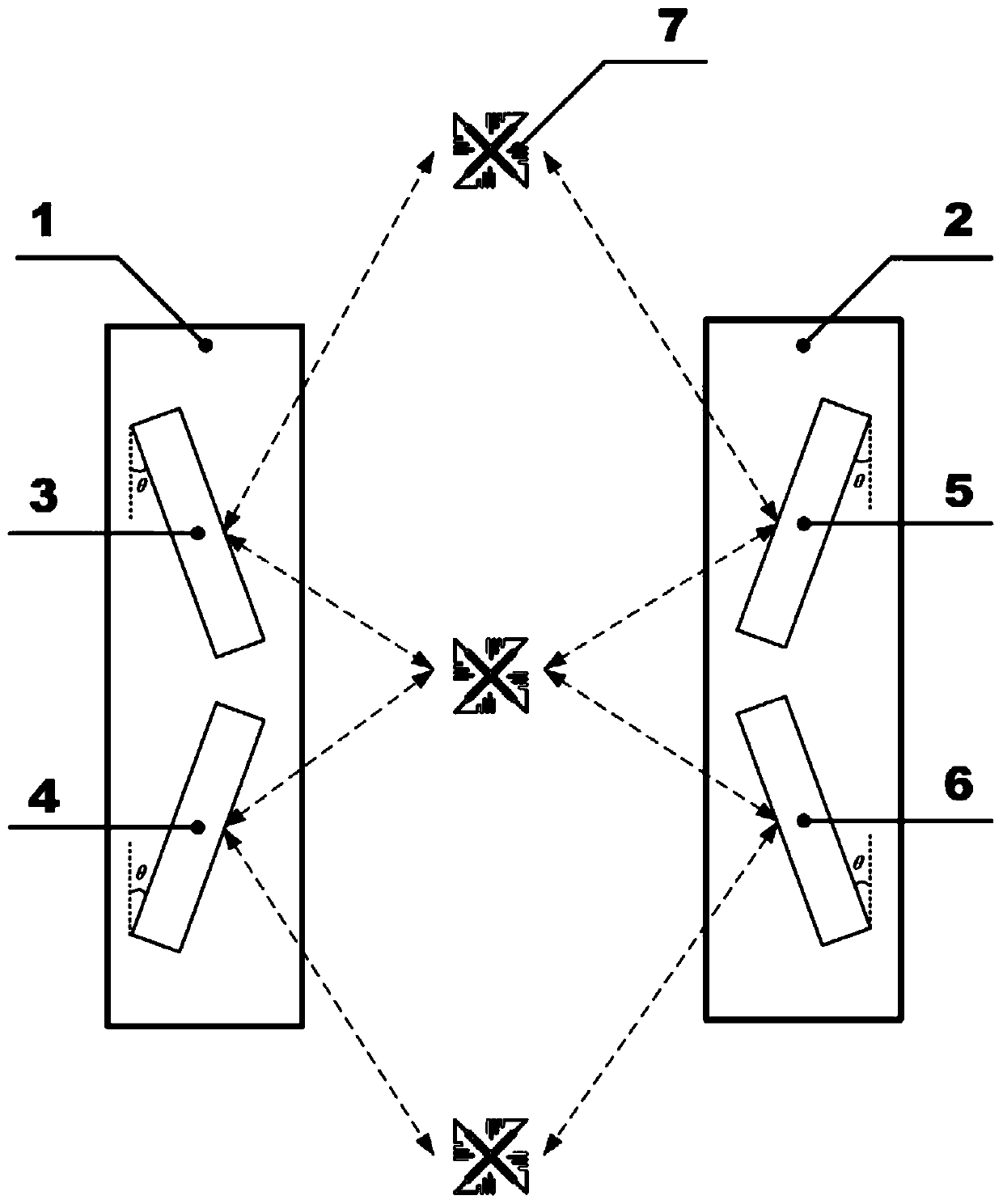
[0067] The invention discloses an open RFID access control system for access detection, such as figure 1 with figure 2 As shown, this embodiment includes access control left device 1, access control right device 2, RFID reader, No. 1 antenna 3, No. 2 antenna 4, No. 3 antenna 5, No. 4 antenna 6, RFID tag 7, and No. 1 antenna Antennas No. 2 and No. 3 are located at the A side of the access control, and Antennas No. 2 and No. 4 are located at the B side of the access control.
[0068] The access control system consists of two parts: RFID signal acquisition equipment and background server. Among them, the RFID signal acquisition device is composed of an RFID reader and an antenna, and the background server is divided into two parts: an algorithm for determining the direction of access control and a display interface. The functions of each part are as follows:
[0069] RFID reader: connected to an external antenna, feeds back the read tag signal to the background server in real...
Embodiment 2
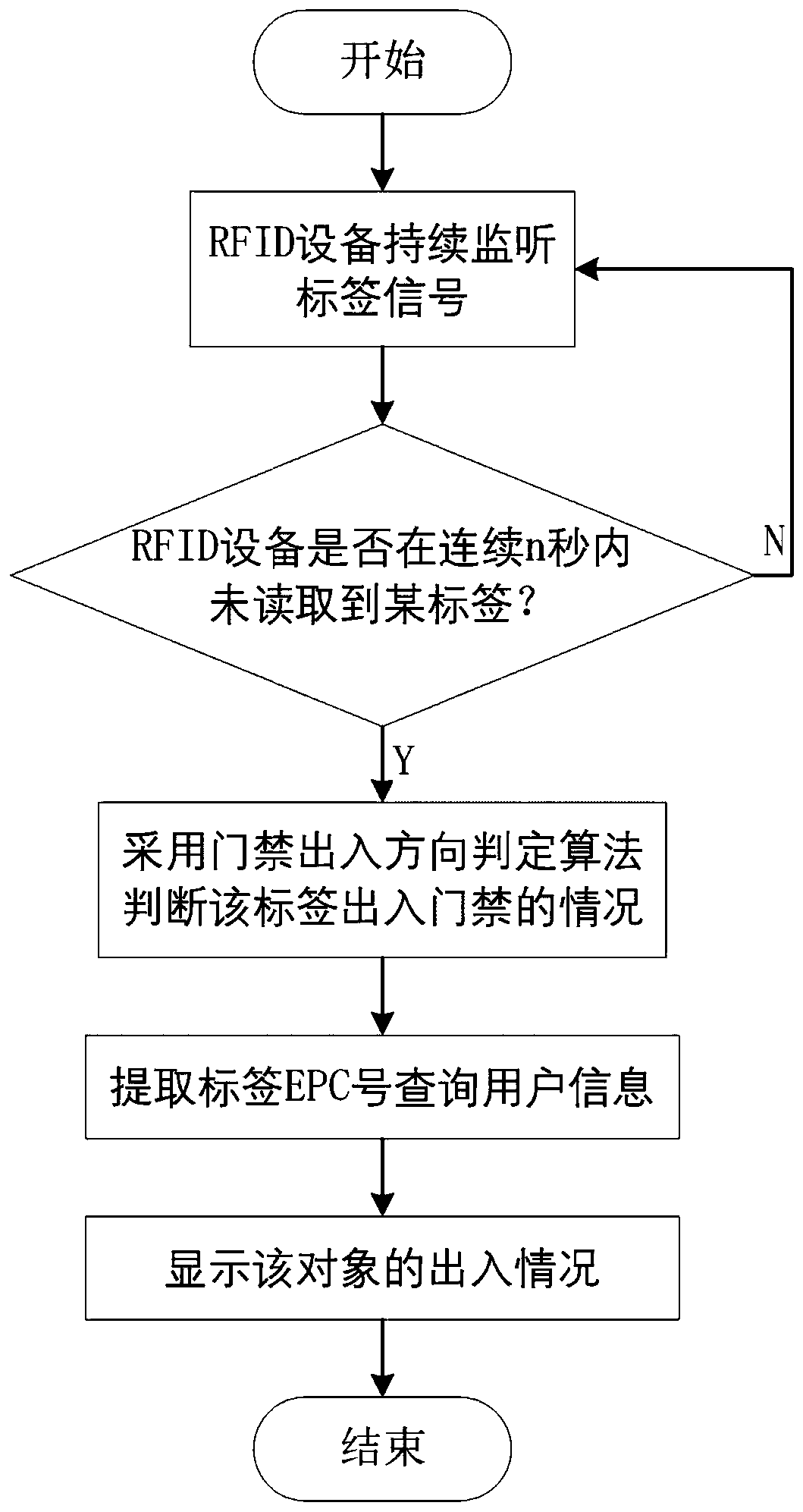
[0089] This embodiment combines Figure 4 , Figure 5 The access control entry and exit judgment algorithm is described.
[0090] Figure 5 The circle pattern and the triangle pattern represent the tag signals that have been classified according to the antenna port number, and the EPC number of the tag is epc 1 . Among them, the circle pattern represents the tag signal read by the antenna at the A-end, and the triangle pattern represents the tag signal read by the antenna at the B-end. The total time T corresponding to the tag signal sequence is 590 ms. The classified data is divided into 6 segments with a time period of 100ms. For the A-end antenna, there are triplets in segments 1, 2, 3, 4, and 5, that is, there are corresponding feature triplets in segments 1, 2, 3, 4, and 5. For the B-end antenna, there are triplets in segments 2, 3, 4, and 6, that is, there are corresponding feature triplets in segments 2, 3, 4, and 6. Taking the first segment of the antenna at end A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com