Mixed feature-based Android malicious software detection method and system
A technology of malware and detection methods, applied in the direction of computer parts, instruments, platform integrity maintenance, etc., can solve the problem of low classification accuracy, and achieve the effects of improving identification accuracy, improving classification accuracy, and reducing false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The technical means adopted by the present invention to achieve the intended invention purpose are further described below in conjunction with the drawings and preferred embodiments of the present invention.
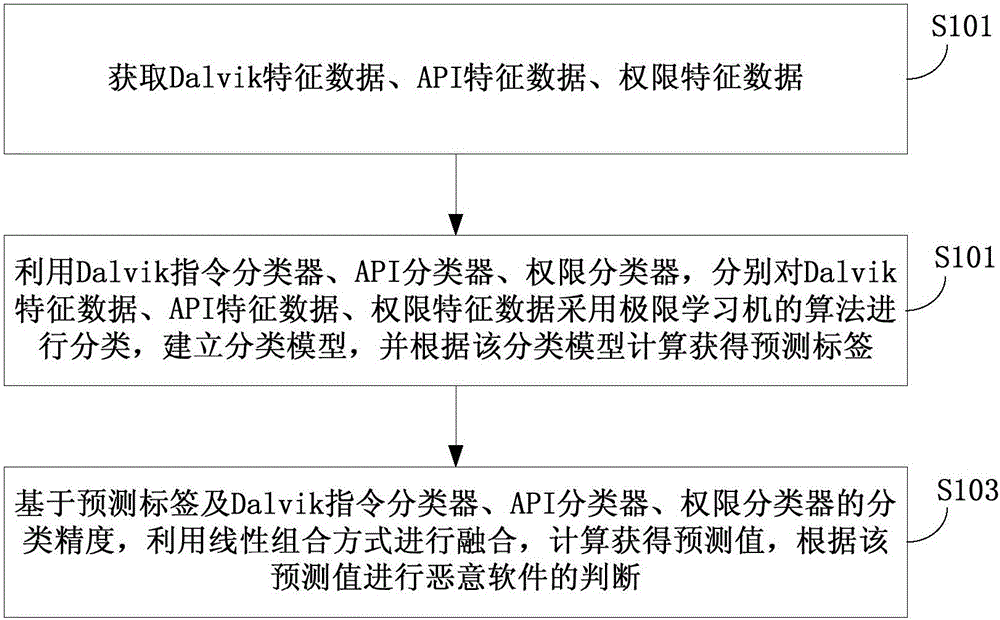
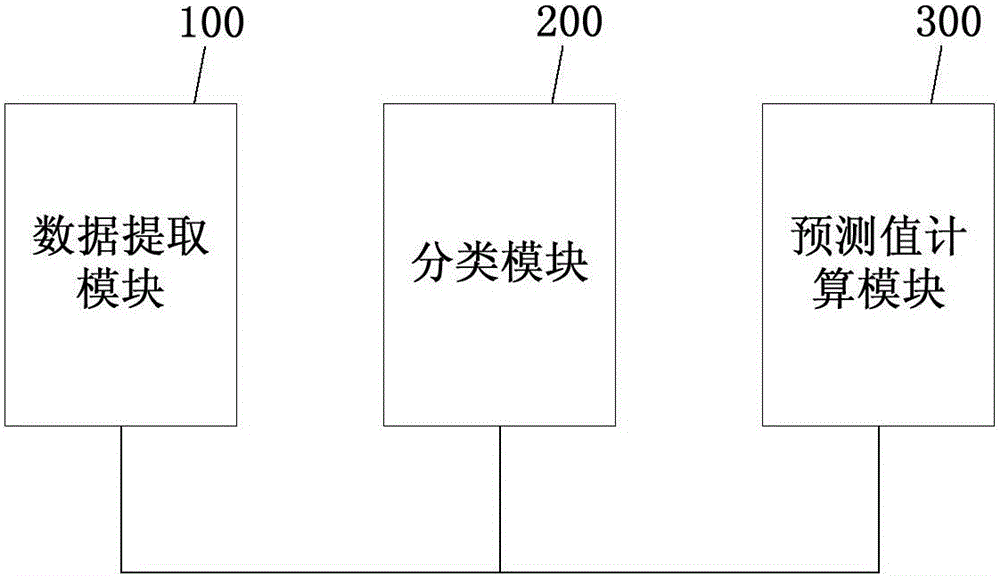
[0017] figure 1 It is a flowchart of a method for detecting Android malware based on mixed features according to an embodiment of the present invention. Such as figure 1 As shown, the method includes:
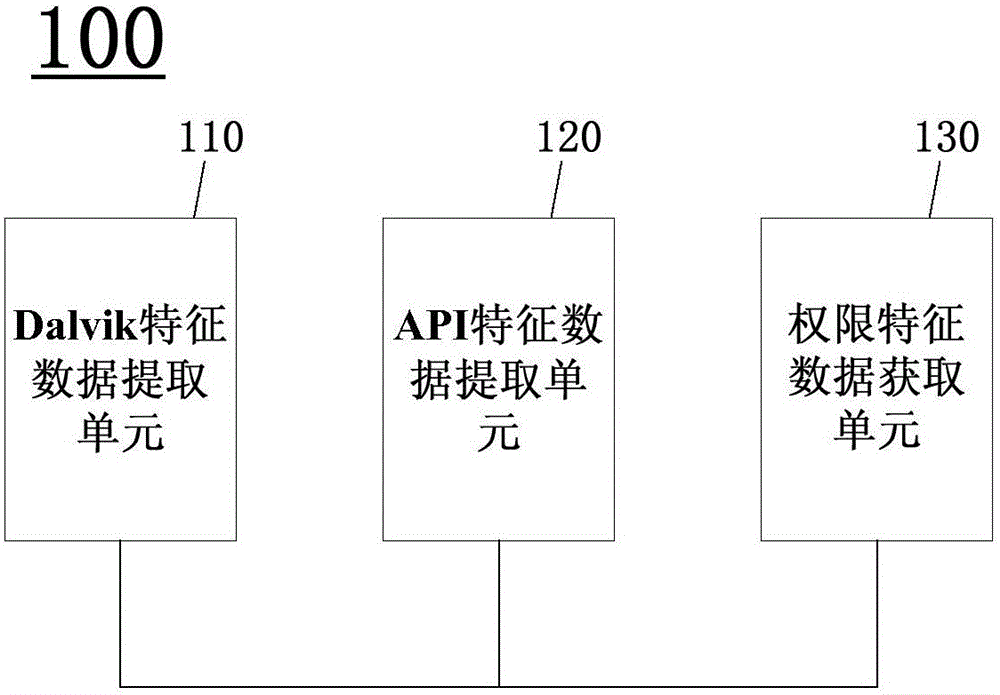
[0018] Step S101, acquiring Dalvik feature data, API feature data, and authority feature data.
[0019] Specifically, the extraction of Dalvik feature data is to use the baksmali tool to decompile the dex file, output the Dalvik assembly file, extract the Dalvik feature data, and use the feature vector to represent the Android application software; if there is a Dalvik feature data, set it to 1, otherwise set it to 0.
[0020] The API feature data is extracted by using the Dedexer tool, through the operation command "java-jar Dedexer.jar-d " decompiles the cla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com