Chinese multi-keyword fuzzy sort encryption text search method based on local sensitive hash
A technology of local-sensitive hashing and search methods, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems of wasting storage space and time overhead, unable to realize Chinese fuzzy search, etc., to reduce computing and storage. Overhead, the effect of efficient fuzzy keyword storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The technical solutions of the present invention will be described in detail below with reference to the accompanying drawings.
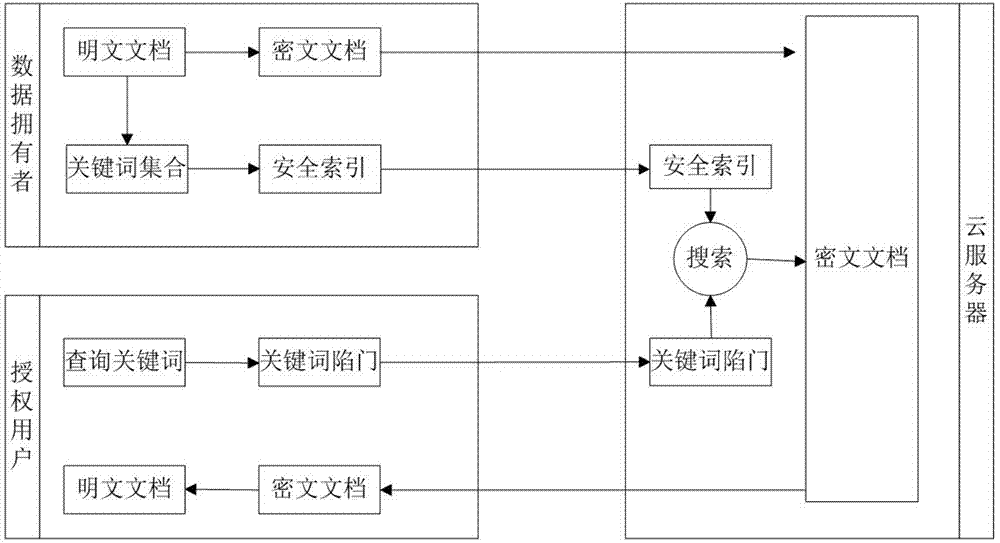
[0028] The invention provides a Chinese multi-keyword fuzzy sorting ciphertext search method based on local sensitive hash, figure 1 The system framework of the present invention includes three entities: data owner, authorized user and cloud server. The index and trapdoor encryption of the present invention are encrypted by using the secure KNN algorithm, and can refer to: WongW K, Cheung W L, Kao B, et al.SecurekNN computation on encrypted databases / / Proceedings of the ACM Sigmod International Conference on Management of Data. New York, USA, 2009: 139-152.
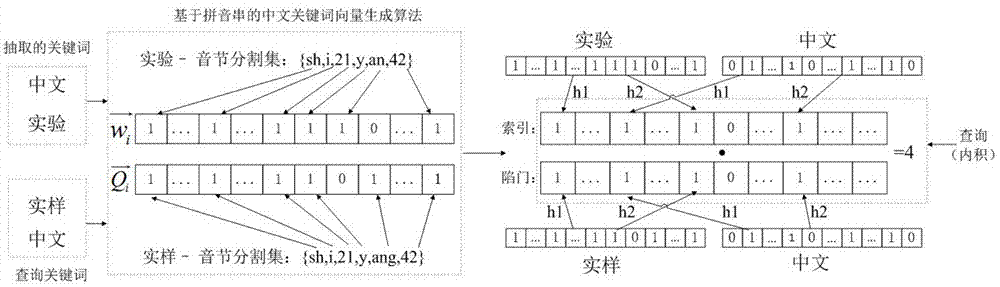
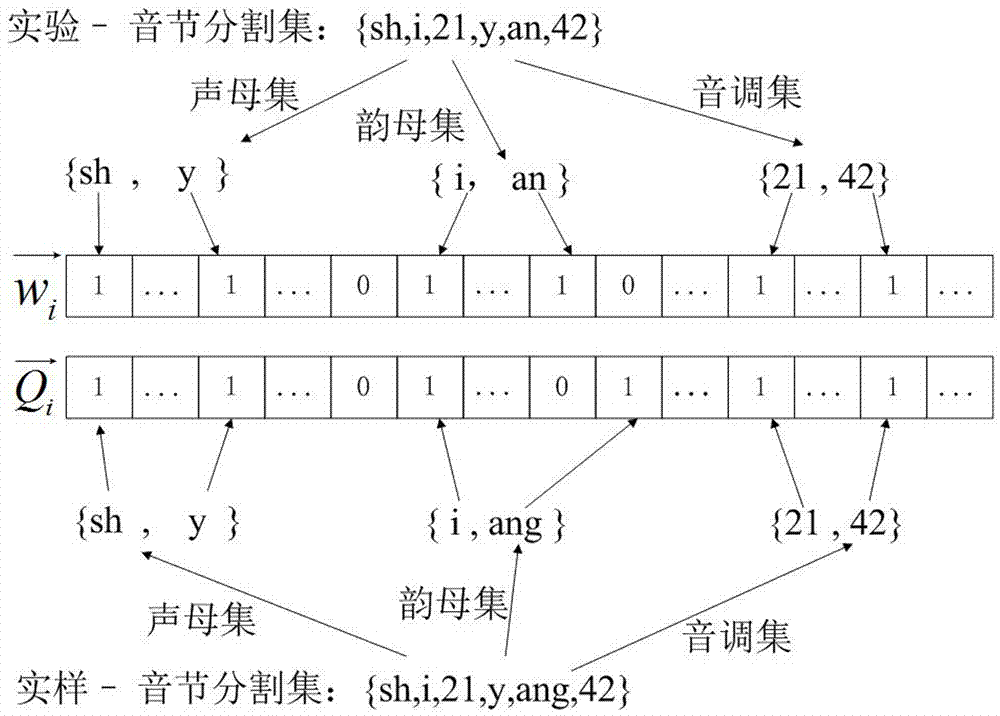
[0029] further, as figure 2 It is the basic flow of the present invention, and the concrete steps are as follows:
[0030] (1) Setup: The data owner selects the plaintext document collection F=(f 1 ,f 2 ,…,f m ) to extract keywords to obtain the keyword set W=(w 1 ,w 2 ,…,w n )...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com