Database user behavior security auditing method for internal and external network boundaries of electric power information
A technology of security auditing and power information, applied in the direction of electrical digital data processing, digital data authentication, computer security devices, etc., can solve problems such as compatibility of difficult-to-isolate devices, achieve effective data preparation, improve anomaly detection efficiency, and improve overall security protection effect of ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
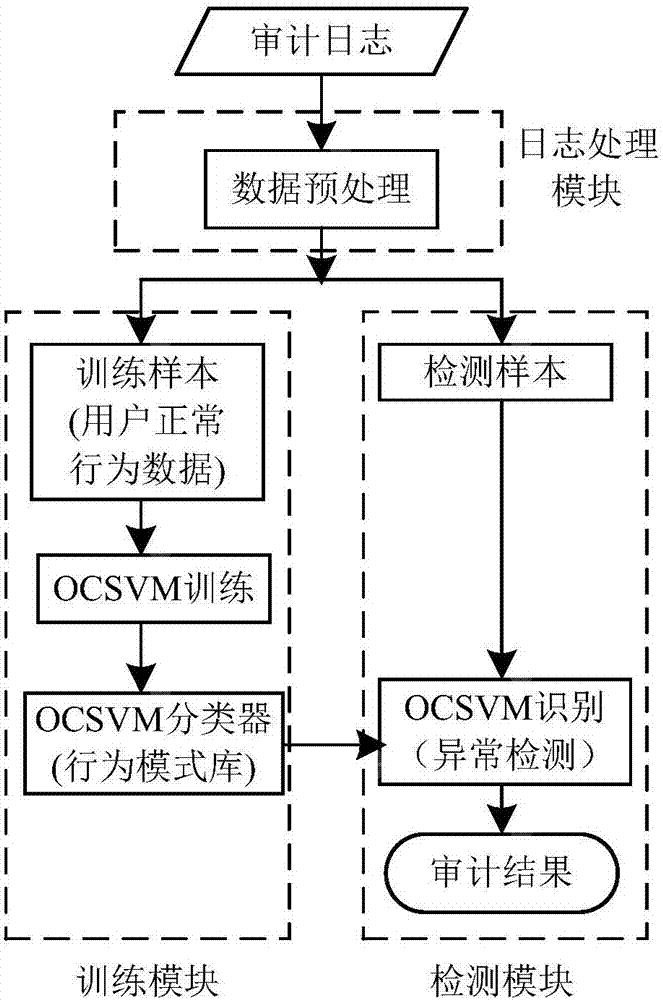
[0075] (1) Experimental simulation environment. On the Eclipse development platform, the libsvm.jar toolkit is used to complete the toolkit, which can provide basic SVM implementation functions.
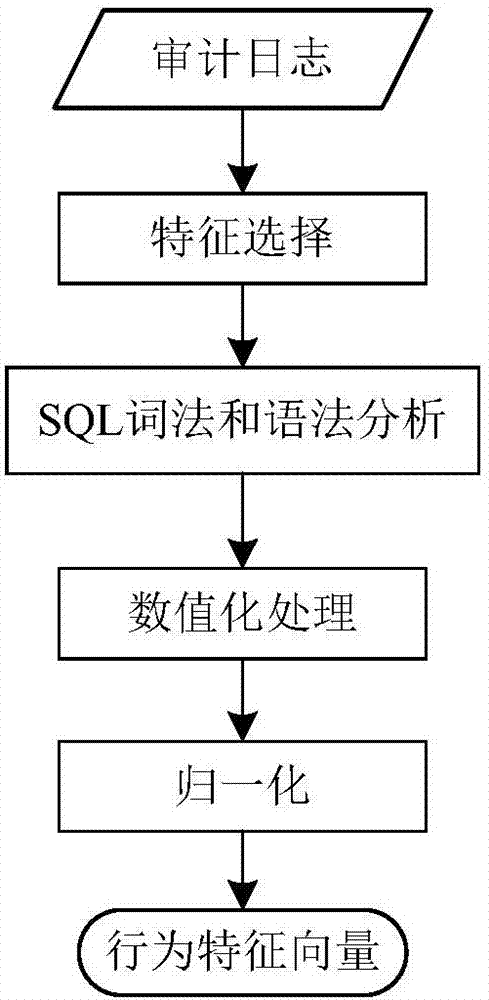
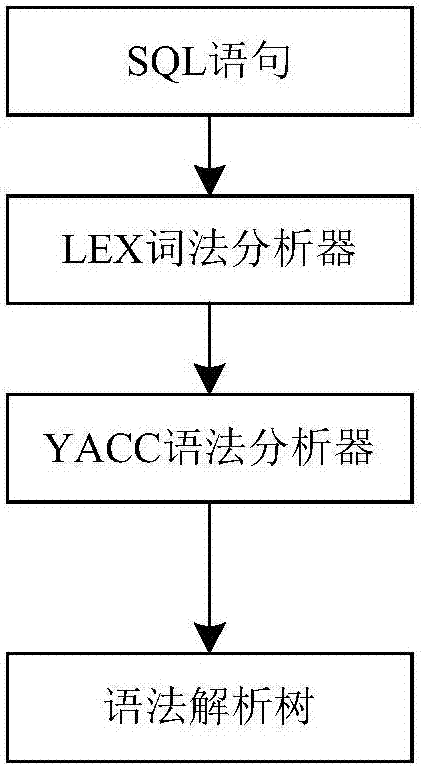
[0076] (2) Sample collection. The normal sample data collection of the experiment comes from the log records of the isolation device at the boundary of the internal and external network of electric power information. The log includes records such as operation code, execution time, SQL operation statement, source IP address, and port number. By analyzing the characteristics of normal behavior log data, simulate and construct the log data of three common abnormal behaviors of user unauthorized operation, illegal user operation and sensitive table resource reading, and use it as test data to verify the feasibility of this audit scheme. Select 200 training samples, 60 test samples of normal behavior, 36 samples of user unauthorized operation, 32 samples of illegal user operation, and 25...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com