User data security lock
A technology of user data and security lock, which is applied in the field of computer security, can solve problems such as data destruction, personal firewall resistance effect is negligible, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
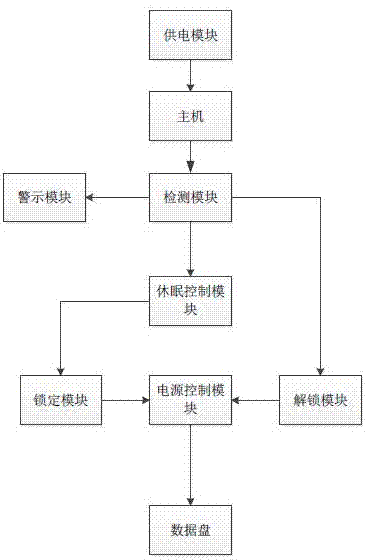
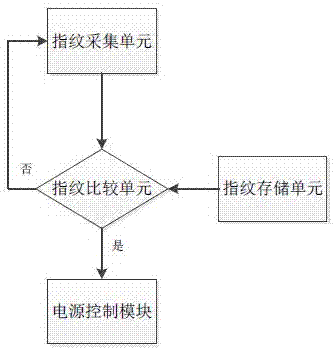
[0025] Such as figure 1 The user data security lock shown includes a power supply module connected to the host, and also includes a detection module for detecting the network security of the host. When a dangerous situation is detected, an emergency signal can be sent to the power control module first. Then send a locking signal to the locking module, and when the detection situation is safe, the unlocking module can be controlled to open and send a safety signal to the dormancy control module;
[0026] The power control module is used to receive emergency signals and safety signals, and can control the power on and off of the data disk in the host;
[0027] The dormancy control module, the detection module first sends the emergency signal to the dormancy control module. After receiving the emergency signal, the dormancy control signal controls the data disk to enter the dormant state, stops the data connection between the data disk and the host, and then the dormancy control ...
Embodiment 2
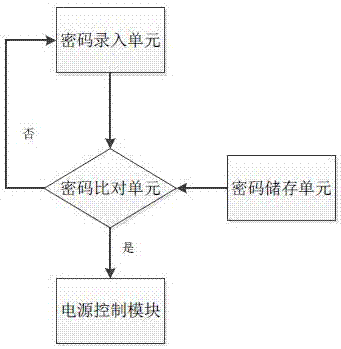
[0037] Such as image 3 As shown, the difference from Embodiment 1 is that the unlocking module in this embodiment is a password verification module arranged on the host computer, including a password input unit for the user to input a password; a password storage unit for storing correct password information The password comparison unit is used to compare the entered password signal with the correct password information in the password storage unit, and output an unlocking signal to the power control module after the comparison is successful.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com