A resource security protection method based on data graph, information graph and knowledge graph with definable security of input decision
A knowledge graph and resource security technology, applied in digital data protection, other database retrieval, other database indexing, etc., can solve the problem that data privacy protection has not yet been managed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
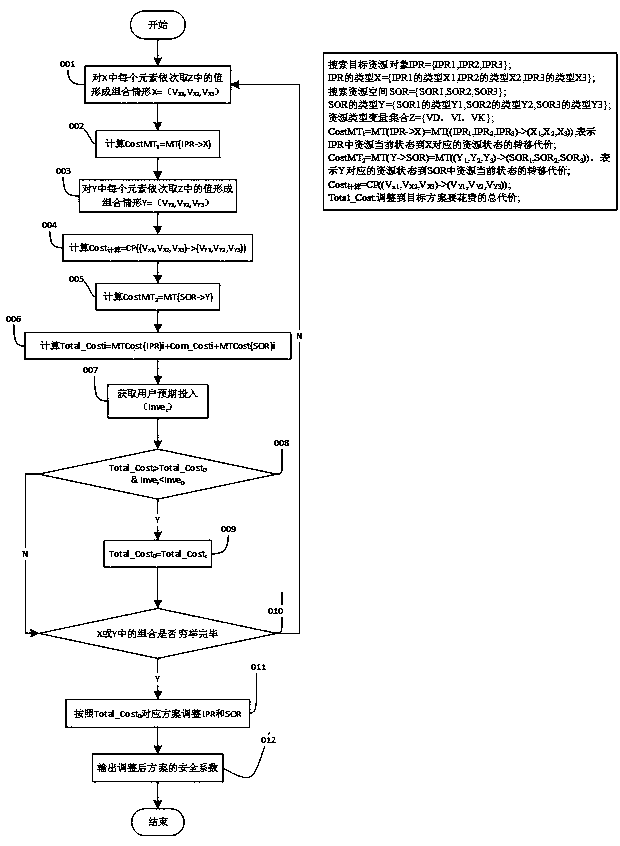
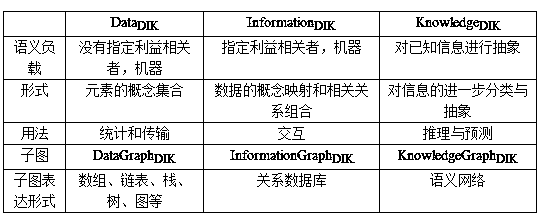
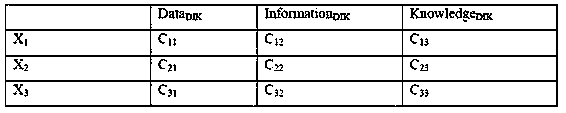
[0044] The security of input decision is a definable resource security protection method based on data graph, information graph and knowledge graph, which is characterized in that the data DIK , Information DIK and Knowledge DIK The resources that exist in the form are organized and stored reasonably according to the storage cost and safety factor, and it is impossible to judge which layer of the resource should be stored on the map only by the resource type. The specific implementation steps are:
[0045] Step 1) corresponds to figure 1 In operation 001, take the value in Z for each element in X in turn to form a combination situation X={X 1i ,X 2j ,X 3k},i,j,k∈{1,2,3};
[0046] Step 2) corresponds to figure 1 In operation 002, for each situation, calculate the cost of transferring resources from the current situation to each situation in IPR (CostMT1) according to formula 1:
[0047] (1)
[0048] Step 3) corresponds to figure 1 In operation 003, take the value i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com