Personal code forming and management method based on improved AES
A management method and password technology, which is applied in the field of personal password generation and management based on improved AES, can solve problems such as poor security, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
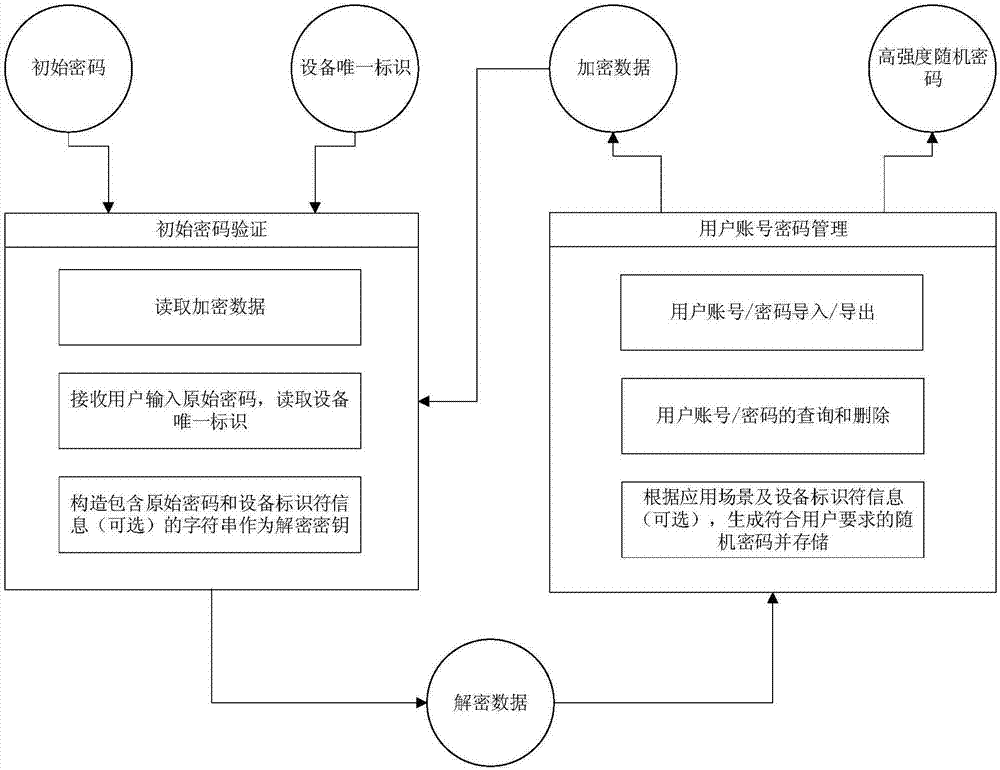
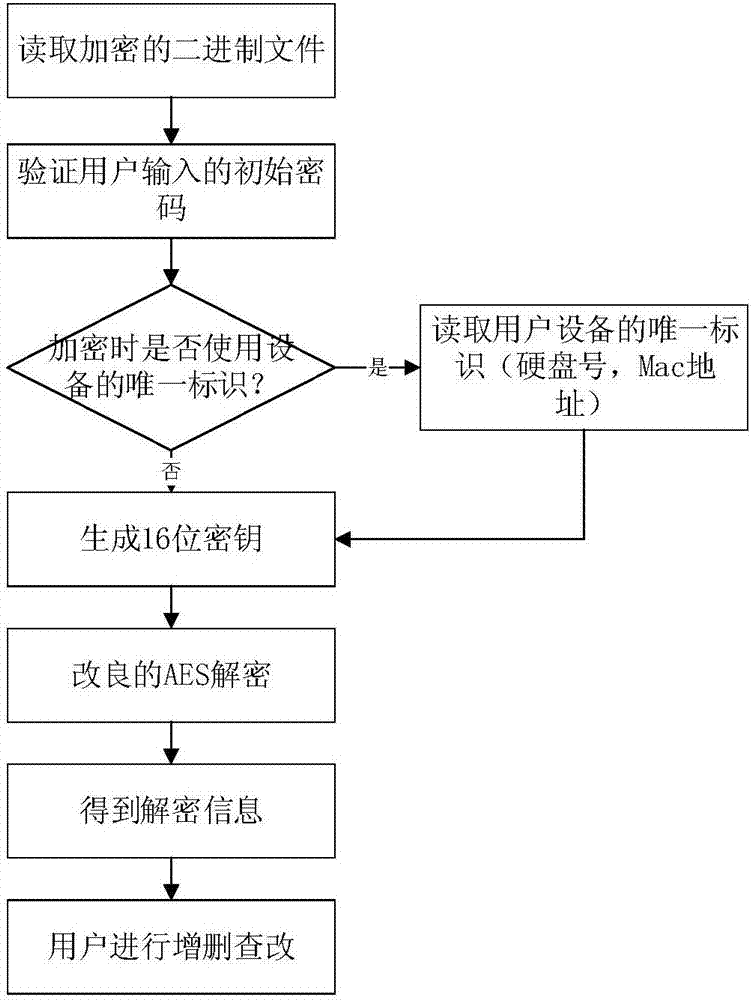
[0041] refer to Figure 1-3 . The present invention is based on the personal password generation of improved AES and the specific steps of management method are as follows:
[0042] The method of the invention includes two modules: an initial password verification module and a user account password management module.
[0043] Among them, the initial password verification module includes: reading and verification of the initial password, reading of the unique identification of the device, formation of the encryption key, and analysis of the encrypted file.
[0044] The user account password management module includes: import and export of user account passwords, query and deletion of generated passwords, and generate new random passwords according to user application scenarios and requirements.
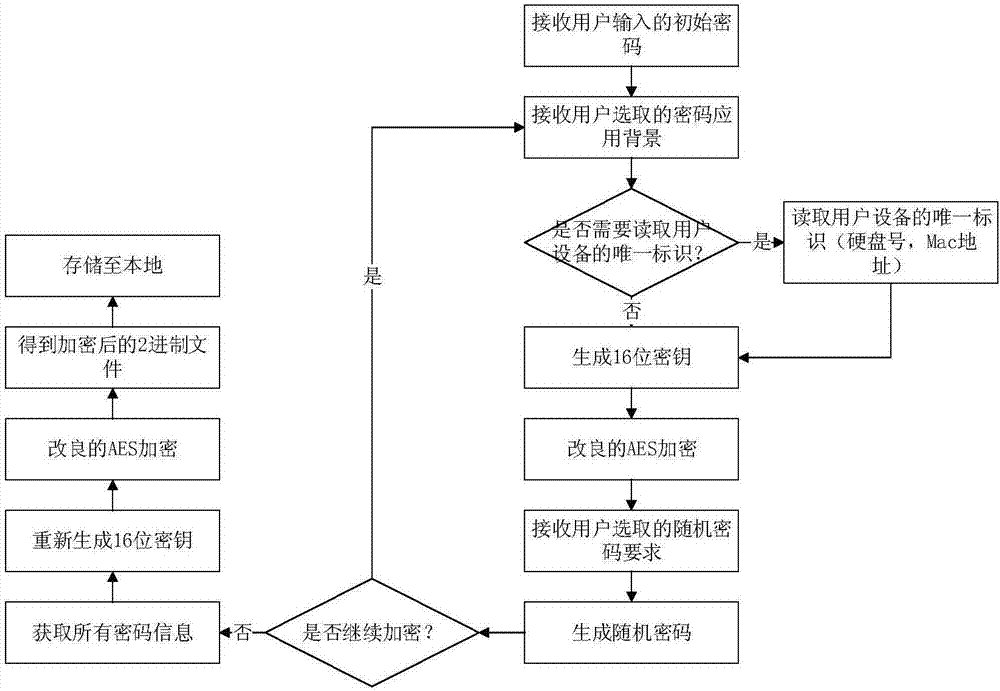
[0045] The password generation and storage process is as follows:
[0046] Step 1: Receive the user's initial password.
[0047] This process is the user's personal input, and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com