Industrial control private agreement-based fuzzy test method
A proprietary protocol and fuzz testing technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems that the vulnerability mining method is not suitable for industrial control networks and less research
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
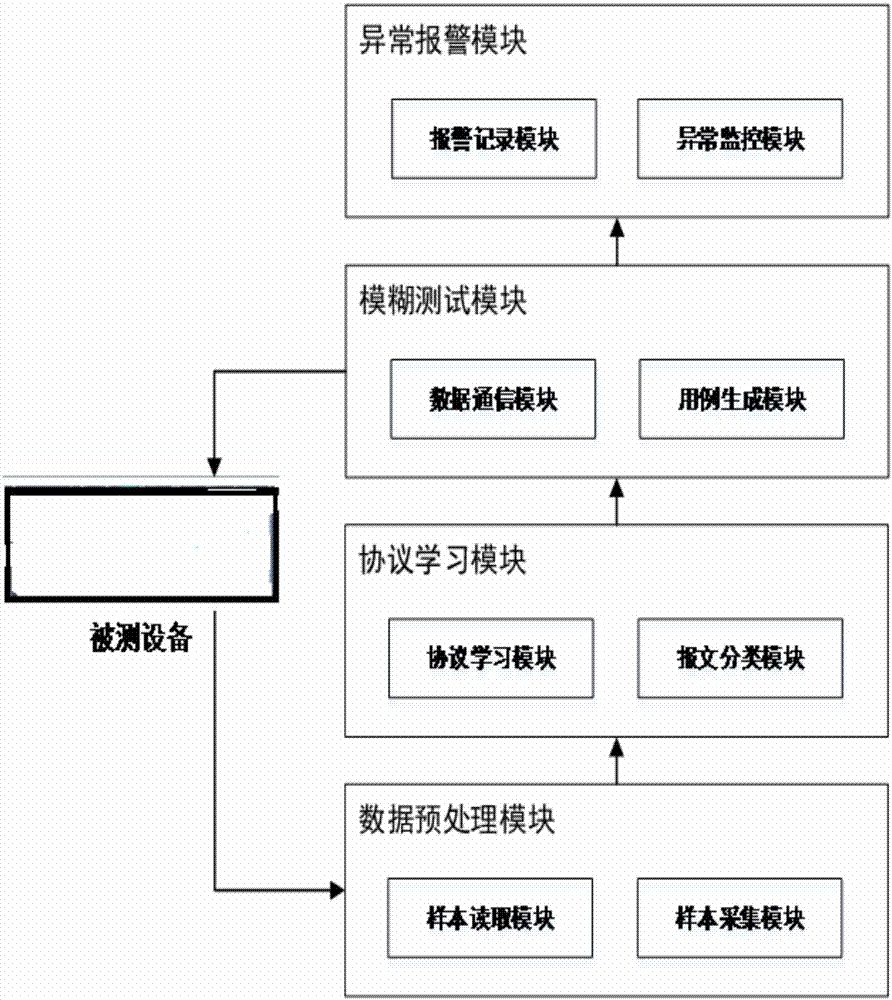
[0016] figure 1 It is a schematic structural diagram of the fuzzing testing method based on the industrial control private protocol of the present invention, such as figure 1 As shown, the steps include:
[0017] Step 11: In the normal industrial control process environment, collect the communication traffic of the private protocol, and use wireshark to save it as a pcap file. The program instantiates a virtual capture device through the ICaptureDevice interface of SharpPcap, uses TcpDump rules to filter the sample set, saves all request data in the request queue, and saves all request response data in the request response queue.
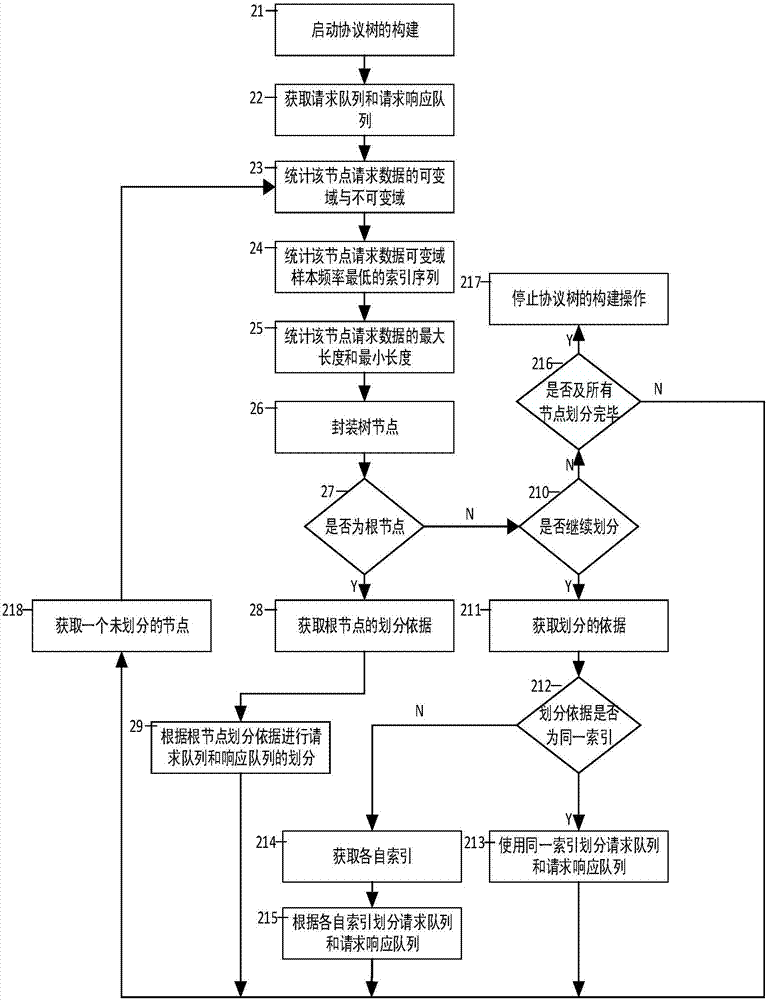
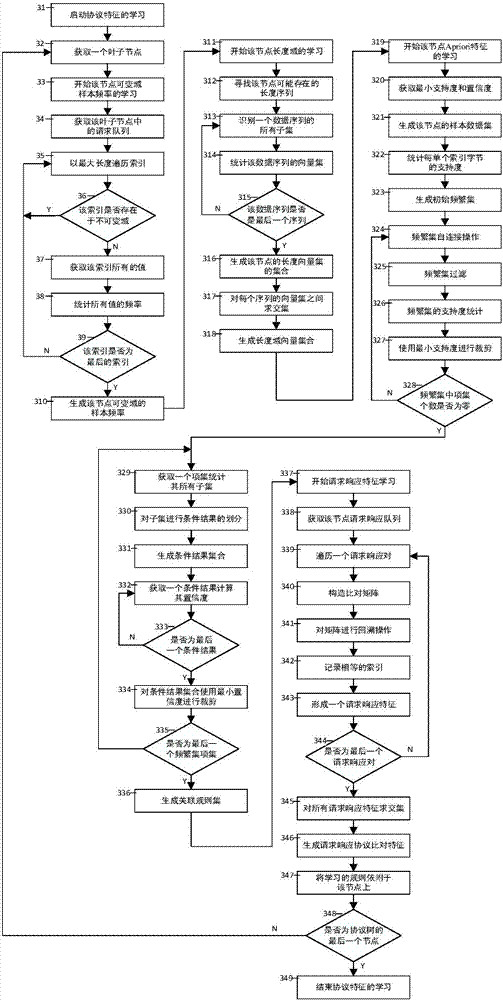
[0018] Step 12: Use the protocol tree generation algorithm to classify the private protocol packets through the two buffer queues, and generate a private protocol feature classification tree by instantiating...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com