Abnormality detecting method and device
An anomaly detection and abnormal sample technology, applied in the field of anomaly detection, can solve the problems of parameter sensitivity and linear inseparability, and achieve the effect of improving detection performance, reducing labeling cost, and reducing the amount of labeling data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] An anomaly detection method provided by an embodiment of the present invention is introduced in detail.
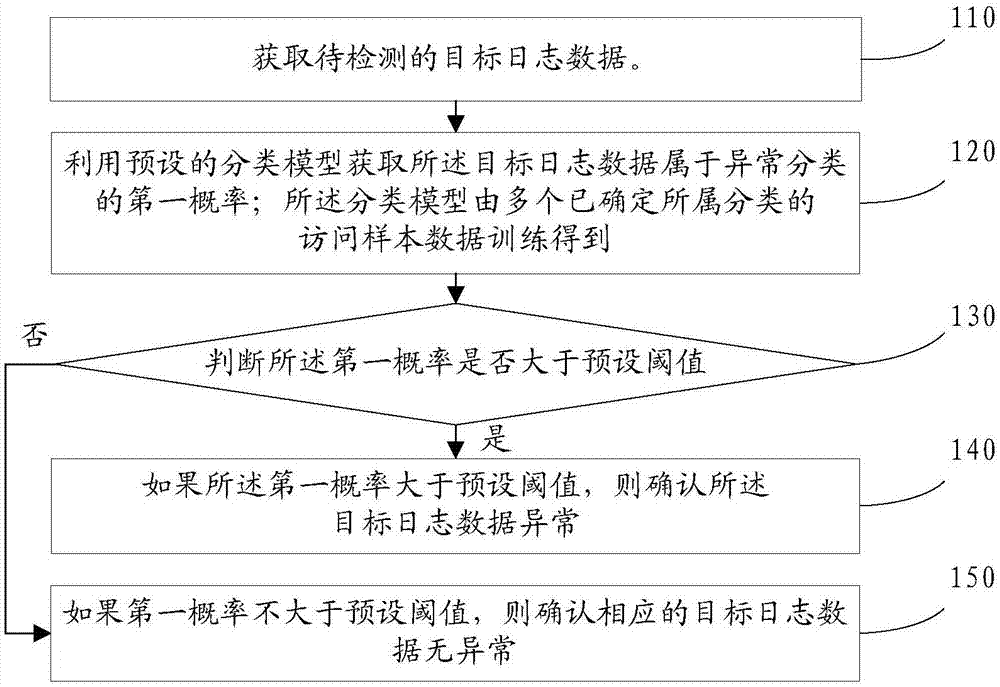
[0057] refer to figure 1 , shows a flowchart of steps of an abnormality detection method in an embodiment of the present invention.
[0058] Step 110, acquiring target log data to be detected.
[0059] Simply put, the core of log data is log messages or logs. Log messages are things generated by computer systems, equipment, software, etc. in response to certain stimuli. The exact stimulus depends largely on the source of the log message. For example, the Unix operating system will record user login and logout messages, the firewall will record the ACL (Access Control List, Access Control List) passed and rejected messages, and the disk storage system will fail when a failure occurs or some systems think that it will fail. log information is generated.
[0060] Log data is the intrinsic meaning of a log message. In other words, log data is the information in a ...
Embodiment 2
[0079] An anomaly detection method provided by an embodiment of the present invention is introduced in detail.
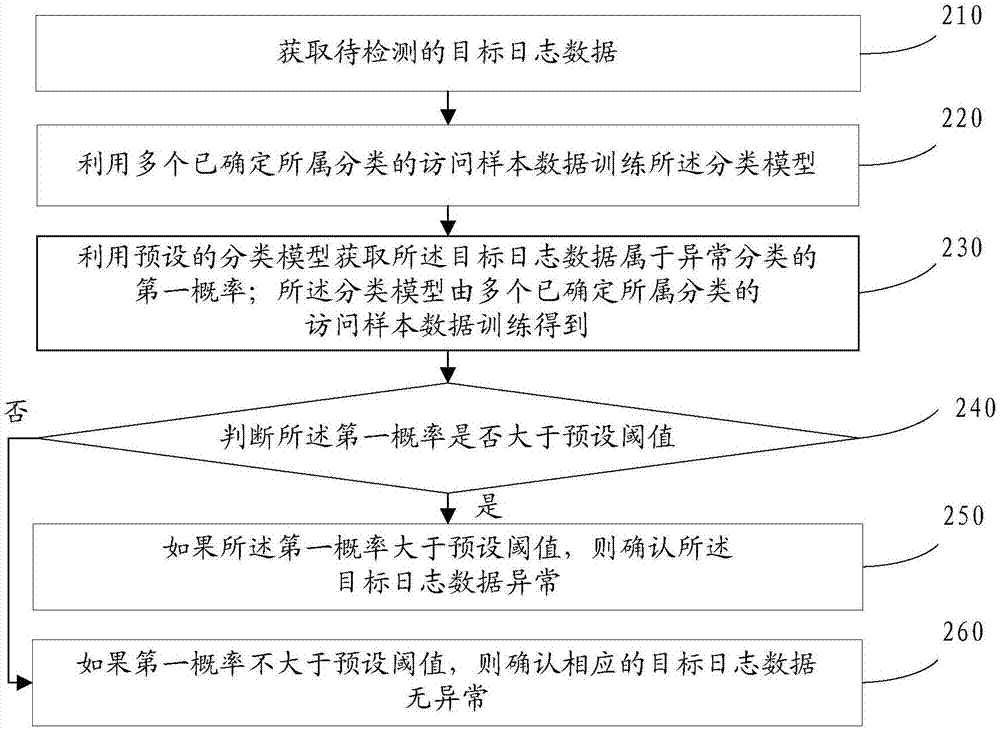
[0080] refer to figure 2 , shows a flowchart of steps of an abnormality detection method in an embodiment of the present invention.
[0081] Step 210, acquiring target log data to be detected.
[0082] Step 220, train the classification model by using a plurality of access sample data whose categories have been determined.
[0083] In this application, before using the classification model to obtain the first probability that the target log data belongs to the abnormal classification, the classification model needs to be trained. Specifically, the classification model can be trained by utilizing multiple access sample data whose classifications have been determined.
[0084] For example, a plurality of access sample data whose categories have been determined can be used as the input of the classification model, and the classification results of the corresponding...
Embodiment 3
[0097] An anomaly detection method provided by an embodiment of the present invention is introduced in detail.
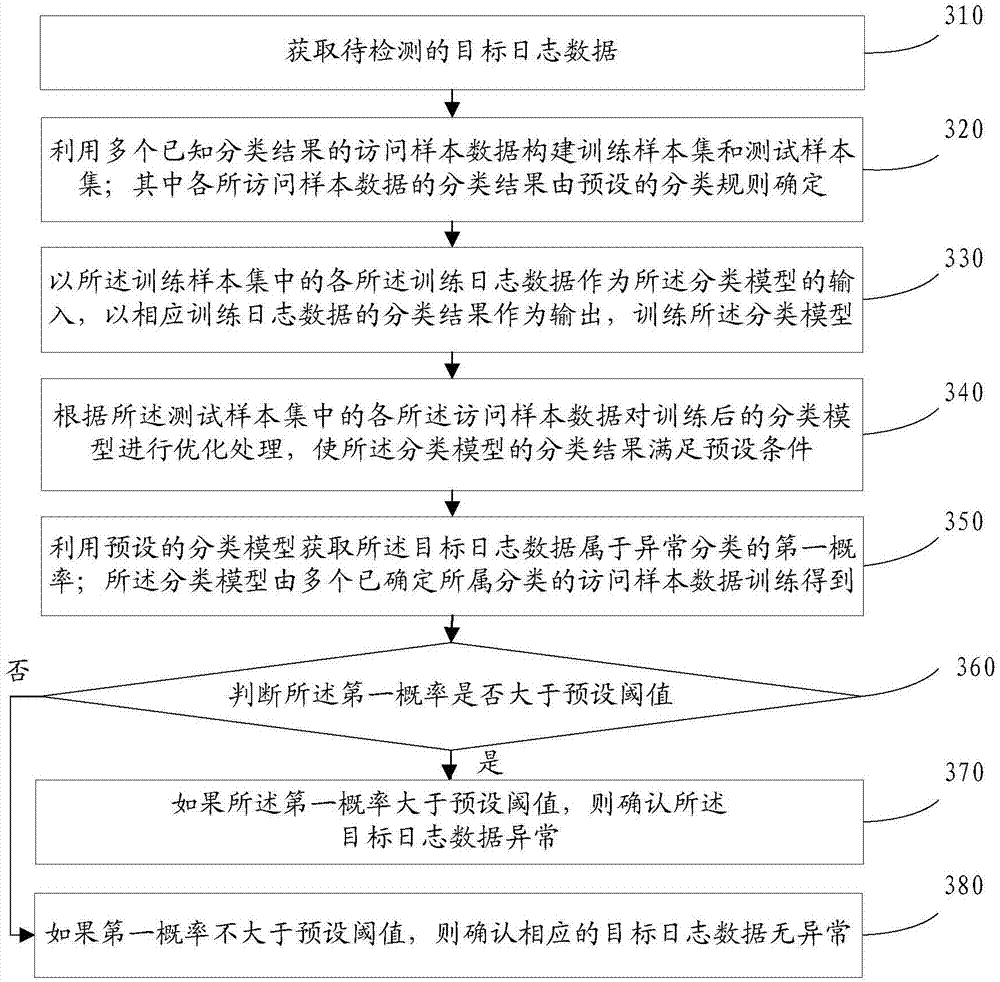
[0098] refer to image 3 , shows a flowchart of steps of an abnormality detection method in an embodiment of the present invention.
[0099] Step 310, acquiring target log data to be detected.
[0100] Step 320, constructing a training sample set and a test sample set by using multiple access sample data with known classification results; wherein the classification results of each accessed sample data are determined by preset classification rules.
[0101] In this application, in order to train the classification model, a plurality of access sample data with known classification results can be used to construct a training sample set and a test sample set. The training sample set can be used to train the classification model, and the test sample set can be used to test the performance of the trained classification model. The access sample data contained in the tra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com