Web security vulnerability detection system and detection method based on information collection
A technology of information collection and vulnerability detection, applied in the field of network security, can solve the problems of less information collection by scanners, incomplete information, affecting the normal operation of target business, etc., and achieve the effect of thorough scanning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
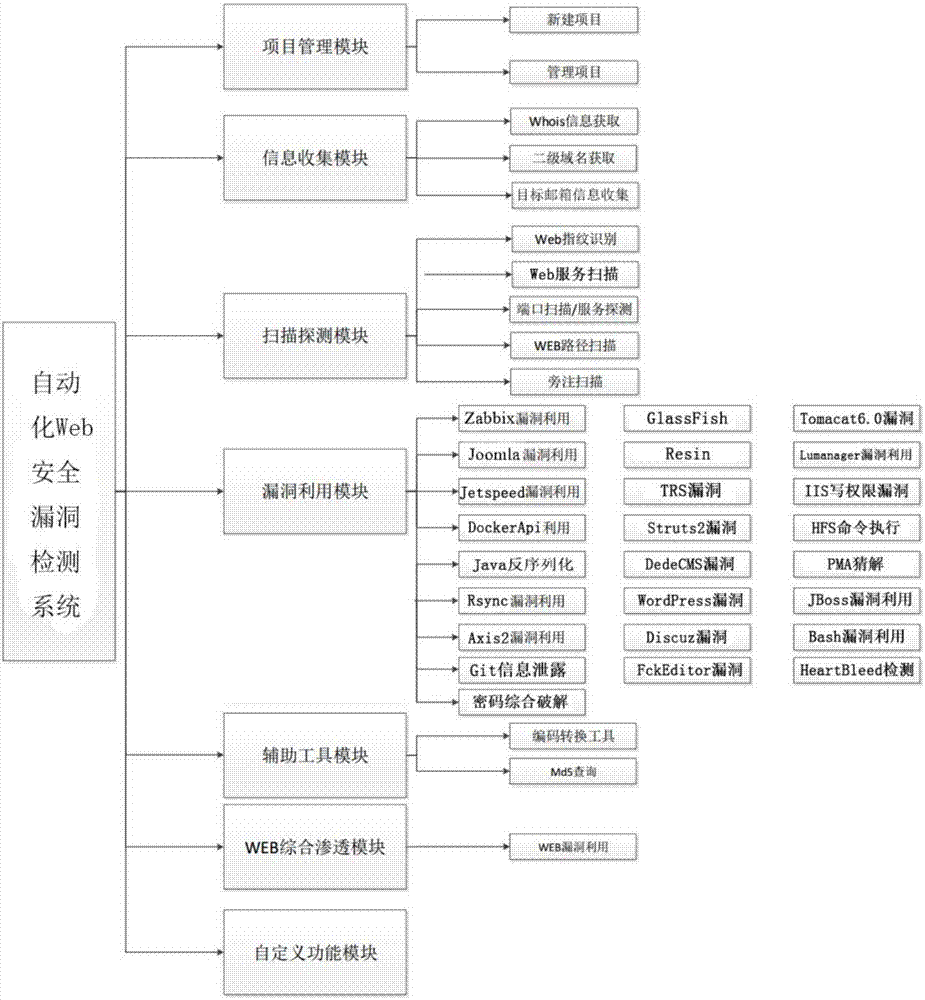
[0017] Such as figure 1 As shown, a Web security vulnerability detection system based on information collection is characterized in that it includes a project management module, an information collection module, a scanning detection module, a vulnerability utilization module, an auxiliary tool module, a Web comprehensive penetration module and a custom function module,
[0018] The information collection module integrates three tools: Whois information acquisition, second-level domain name acquisition and target mailbox information collection. Whois information acquisition can query and extract key registrant information, and query other domain names of the same registrant, NS records and MX records corresponding to domain names, so as to further expand penetration ideas; second-level domain name acquisition tools are equipped with search engine type and brut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com