Mobile phone financial transaction method and mobile phone dual bank cards
A technology for financial transactions and mobile banking, applied in the field of bank cards and financial transactions, can solve the problems of unpopularization of card-free cash withdrawal business, complicated transaction process, and limited income generation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
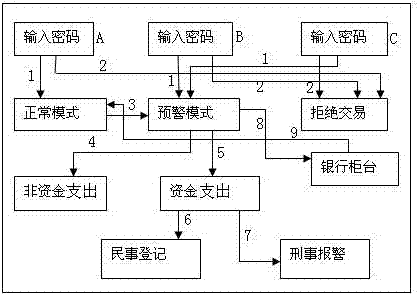
[0071] Example 1: Cash withdrawal or transfer: the cardholder inserts the external bank card, enters the user password, waits for the server to send the temporary password, and after receiving the temporary password information in the short message of the mobile phone, then enters the temporary password, and the temporary password is sent to the mobile financial transaction According to the program, the cardholder only needs to wait, and after seeing the prompt message of successful transaction reservation, take down the external bank card, go to the bank counter or teller machine to continue the transaction within the time set by the cardholder, and insert the external bank card into the teller machine card, enter the temporary password, and select the business type. For safety, the cardholder can also reserve the transaction type at the reservation stage and enter the transaction amount. In this case, the cardholder still needs to enter the transaction amount at the teller mac...
Embodiment 2
[0072] Example 2: Cash withdrawal or transfer: the cardholder uses the electronic cipher to make an appointment through the transaction, and the server sends a temporary password to the mobile phone number bound to the cardholder or sends a temporary password to the mobile financial transaction program, and the cardholder scans it with the mobile phone Electronic cipher, when the electronic cipher receives the scanning signal, the program automatically generates the temporary data. The cardholder needs to enter the temporary password and the temporary data to encrypt with the electronic cipher. After the encryption is completed, the electronic cipher uses the encrypted result Two-dimensional code or other data forms that can be recognized by mobile phones are displayed, and the number of the electronic cipher is displayed at the same time. Use the mobile phone to scan the screen of the electronic cipher, and the mobile financial transaction program imports the password data of t...
Embodiment 3
[0073] Example 3: If the elderly are difficult to operate the short message function of the mobile phone proficiently, fill in the mobile phone number of their children or other relatives when opening an account, and the bank card password will be informed by the children during the reservation stage, and the elderly choose to avoid it at home. Others, to ensure the security during the process of entering the password, the child or other relatives will inform the temporary password when the teller machine is operated or when cash is withdrawn at the counter. The temporary password is only used once. Even if others know the temporary password, it is useless. If the transaction is completed within the time limit, the transaction will be voided.
[0074] Embodiment: 4: mobile banking or online banking recharge, the cardholder inserts the external bank card, the built-in bank card is on the mobile phone, no need to insert, enter the user password, after password verification, enter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com