A dynamic detection method of rop and its variant attacks based on pin tool
A technology of dynamic detection and tools, which is applied in the direction of instruments, calculations, electrical digital data processing, etc., can solve the problems of low detection efficiency, achieve the effect of convenient deployment, strong practicability, and overcome the single type
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] All the features disclosed in this specification, except for mutually exclusive features and / or steps, can be combined in any manner.
[0033] The present invention will be described in detail below in conjunction with the drawings.
[0034] A dynamic detection method for ROP and its variant attacks based on the Pin tool, including the following steps:
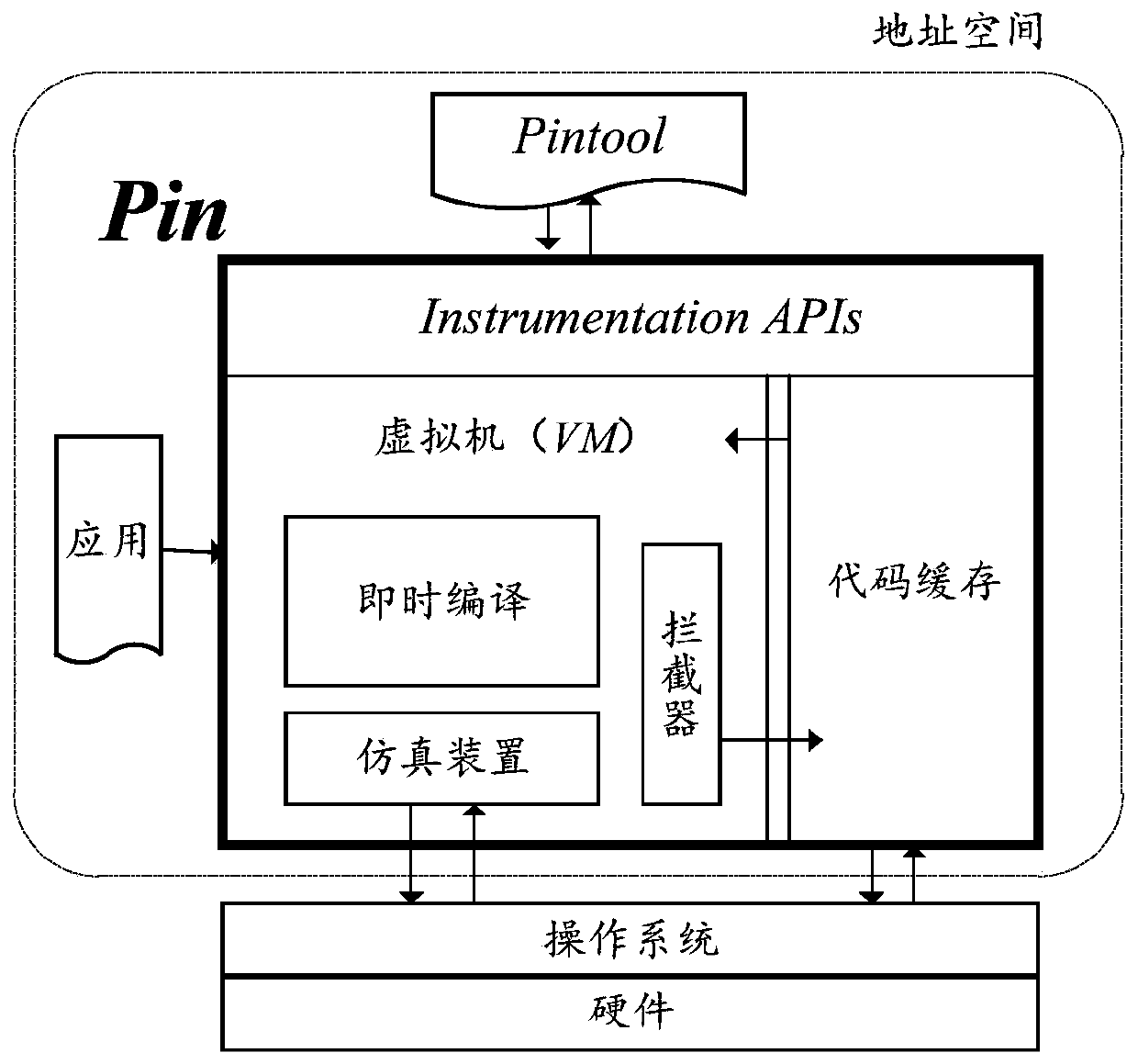
[0035] Step 1: Use binary Pin instrumentation tools (such as figure 1 ) Enable the target program, specifically loading PINTOOL.DLL through PIN.EXE, and return the request to start the target program after PINTOOL.DLL is initialized;
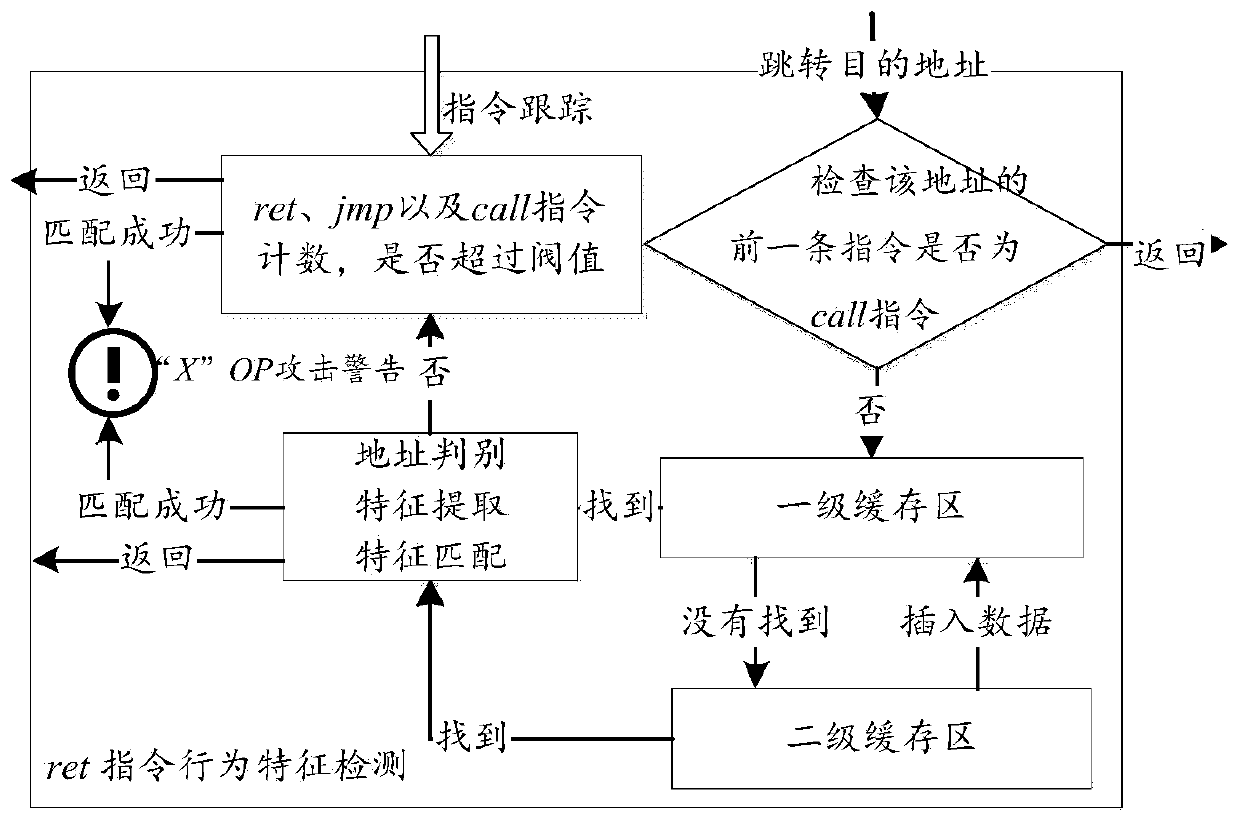
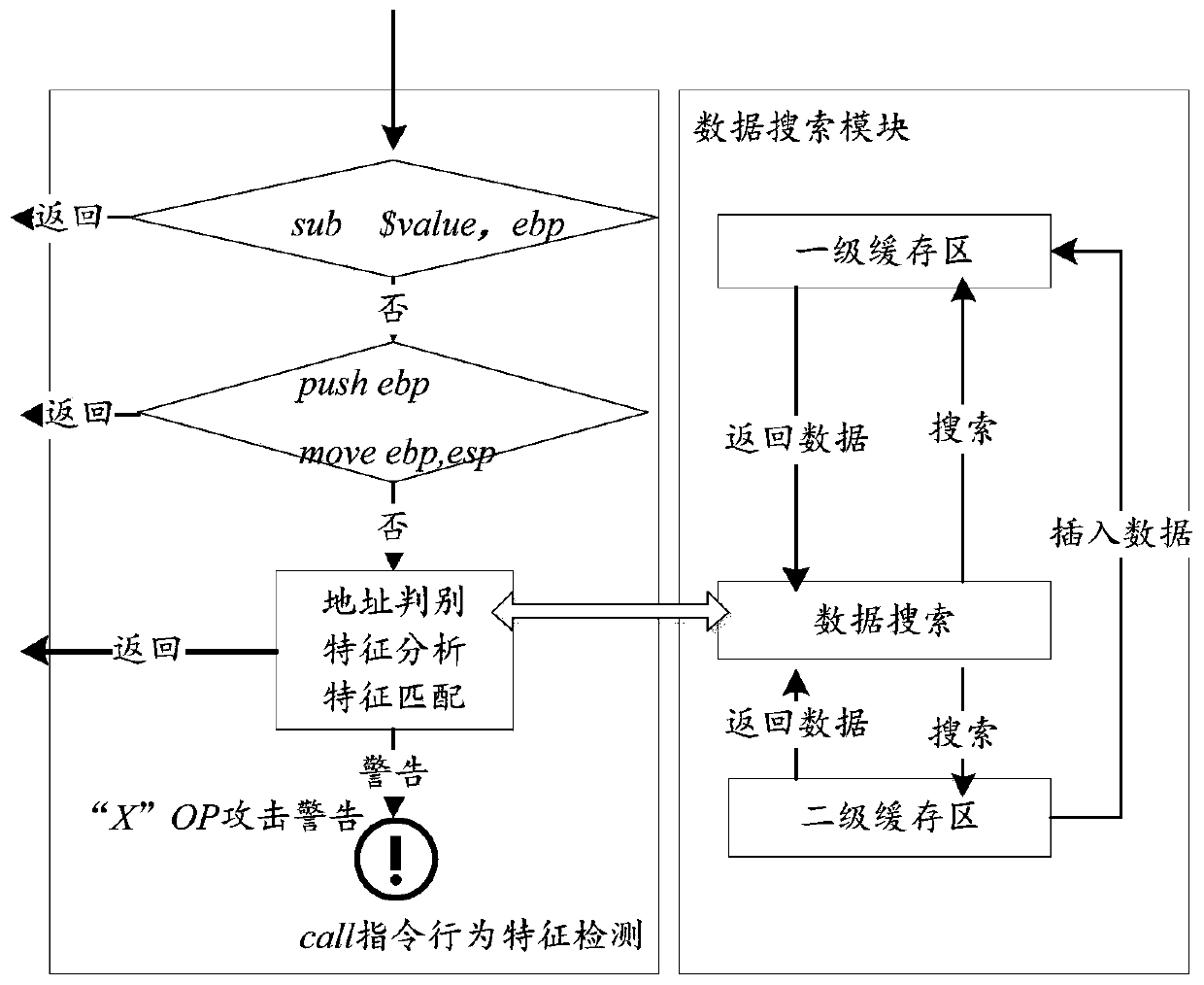
[0036] Step 2: Use the binary Pin instrumentation tool to track the target program, and match the ret instruction, call instruction and jmp instruction. The binary Pin instrumentation tool includes a dynamic link library analysis module, a dynamic monitoring module, and an attack detection module;
[0037] The binary instrumentation tool Pin supports IA-32, Intel(R)64 and Intel(R) many integrated c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com