Method and device for ensuring the security of pos machine firmware
A POS machine and firmware technology, which is applied in computer security devices, data processing applications, instruments, etc., can solve the problems of tampering of POS machine firmware and inability to guarantee the security requirements of POS machines, and achieve the effect of reducing costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
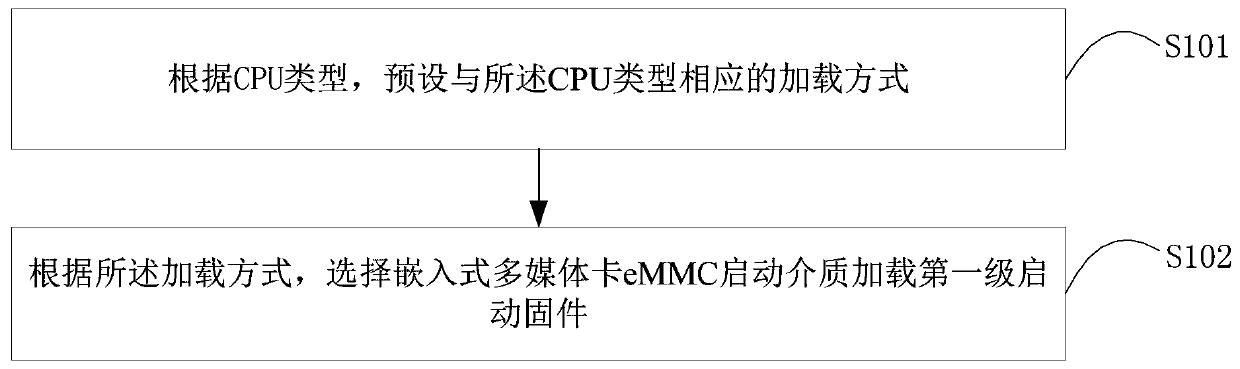
[0025] figure 1 A flow chart of a method for ensuring the security of POS machine firmware provided by an embodiment of the present invention is shown, and the details are as follows:
[0026] Step S101, according to the CPU type, preset a loading mode corresponding to the CPU type.
[0027] Specifically, generally in a terminal device such as an Android device, it mainly includes firmware such as ROM Boot, First Boot, Boot, Kernel, and System. Wherein, ROM Boot is a firmware solidified inside the CPU chip and cannot be changed. After the CPU starts, Run the program in ROM Boot, load First Boot and run; First Boot is the first-level boot firmware, which is used to initialize CPU, memory and other devices, and load the next-level firmware such as Boot; Boot is generally a little kernel or uboot, responsible for Load Kernel; Kernel is the system kernel; System is the Android system. When the CPU starts, it starts from the ROM Boot in the CPU, and the ROM Boot will select the b...
Embodiment 2
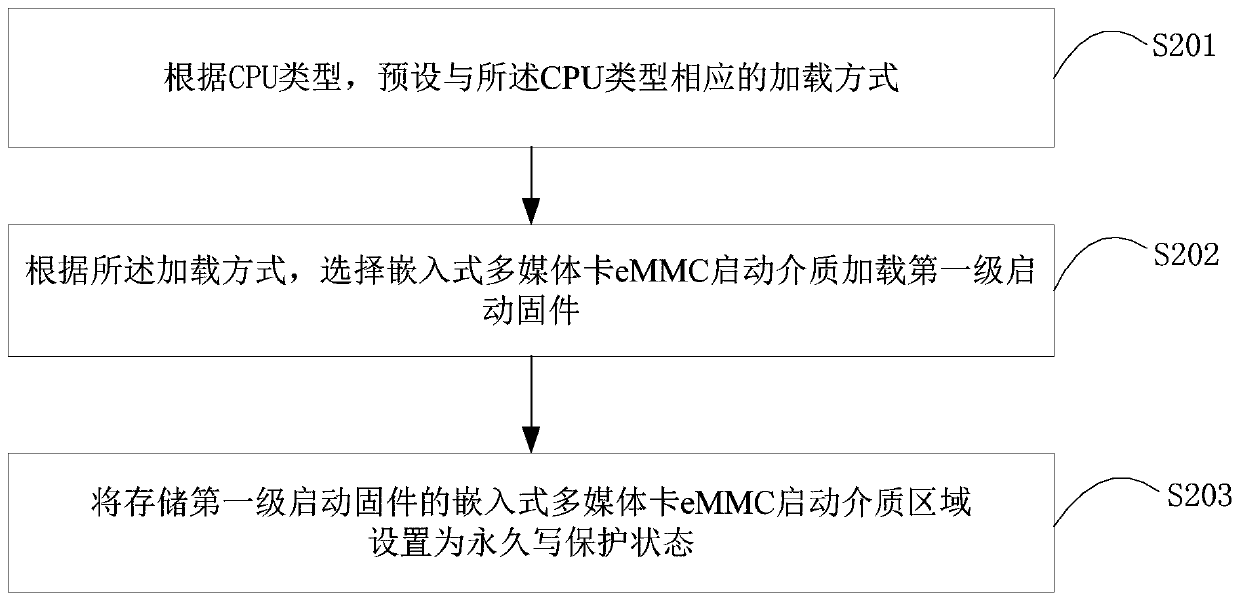
[0044] Figure 2a A flow chart of a method for ensuring the security of POS machine firmware provided by the first embodiment of the present invention is shown, and the details are as follows:
[0045] Step S201, according to the CPU type, preset a loading mode corresponding to the CPU type.
[0046] Among them, the ROM Boot of different types of CPUs selects the boot medium to load the First Boot in different ways. For example, there is a type of CPU with a fuse configuration. This type of CPU selects the boot medium according to the fuse configuration inside the CPU. The fuse inside the CPU is a one-time configuration and cannot be changed after burning. There is a type of CPU that selects the boot medium according to the configuration of the boot pins. When the system is powered on, the boot medium is selected according to the status of certain external GPIOs. There is also a type of CPU that will try to load various boot media in turn. This type of CPU will try to load F...
Embodiment 3
[0058] image 3 A flow chart of a method for ensuring the security of POS machine firmware provided by the first embodiment of the present invention is shown, and the details are as follows:
[0059] Step S301, according to the CPU type, preset a loading mode corresponding to the CPU type.
[0060] Step S302, according to the loading method, select the embedded multimedia card eMMC boot medium to load the first-level boot firmware.
[0061] Step S303, setting the eMMC boot medium area of the embedded multimedia card storing the first-level boot firmware as a permanent write-protected state.
[0062] In this embodiment, for the specific steps from step S301 to step S303, refer to step S201 to step S203 in the second embodiment, which will not be repeated here.
[0063] Step S304, after the first-level boot firmware runs, perform signature verification on the next-level firmware after the first-level boot firmware, and calculate the hash value of the next-level firmware.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com