Http tunnel active detection method, terminal device and storage medium
A technology of active detection and http protocol, which is applied in the field of computer network, to achieve the effect of reducing workload, efficient and accurate detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
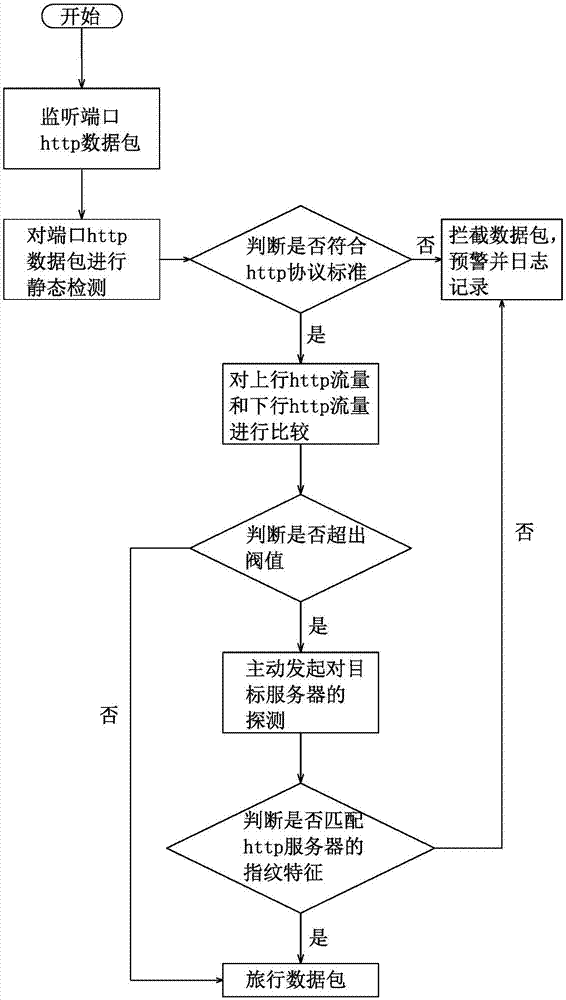
[0026] see figure 1 As shown, the present invention provides a kind of http tunnel active detection method, comprises the following steps:
[0027] S1: Monitor data packets: continue to monitor the http data packets connected to the network through the port until the http data packets are monitored, then enter the S2 step;
[0028] S2: Detect data packets: statically detect the monitored http data packets to determine whether they conform to the http protocol standard,
[0029] Determine whether it conforms to the http protocol standard, specifically: check whether the request command sent by the client to the server conforms to the http protocol standard, and check whether the response information sent by the server to the client conforms to the http protocol standard.
[0030] If yes, enter step S3; if not, enter step S6;
[0031] S3: Traffic comparison of this connection: compare the uplink http traffic and downlink http traffic of this connection to determine whether the...
Embodiment 2
[0049] The present invention also provides an active http tunnel detection terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the processor implements the present invention when executing the computer program. Embodiments of the invention The steps in the above method embodiments, for example figure 1 Method steps for the steps shown.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com