Ransomware detection method based on file status analysis
A software detection and state analysis technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as powerlessness and malicious code helplessness, so as to minimize the degree of damage, improve defense capabilities, and improve security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the technical problems, technical solutions and beneficial effects to be solved by the present invention clearer, the present invention will be described in detail below in conjunction with the embodiments. It should be noted that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
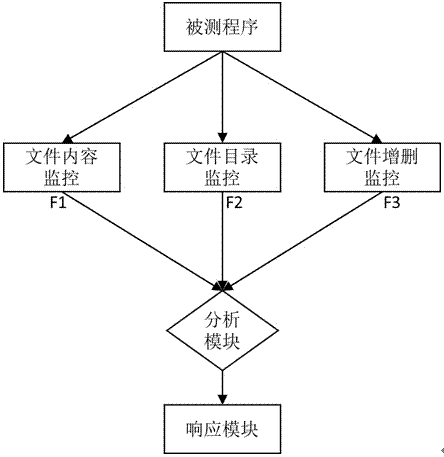
[0030] In the ransomware detection method based on file state analysis, firstly, the system sets three monitoring modules: a file content monitoring module, a file directory monitoring module, and a file addition and deletion monitoring module, an analysis module, a response module, and a monitoring time window W; then, Starting from the multi-faceted logic of the file state in the host, within each time unit of length W, comprehensively combine the three aspects of file content monitoring, file directory monitoring, and file addition and deletion monitoring to continuously monitor the file access behavi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com