Malicious crawler defense strategy selection method for Web server
A server and crawler technology, applied in the field of network information security, can solve the problems of server resource consumption, Web server difficulty, accidental injury to users, etc., to achieve the effect of improving effectiveness and wide application value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
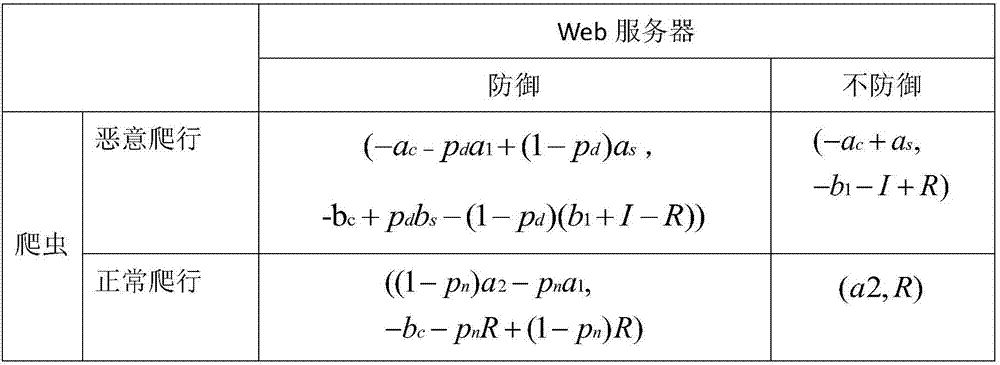
[0029] The main technologies involved in the three steps of the invention are described in detail below, including the formalization and calculation of benefits and costs, the game’s profit matrix, the strategy selection method based on incomplete information dynamic games, and the strategy selection method based on incomplete information. The strategy selection method under the game.
[0030] 1. Formalization and calculation of benefits and costs
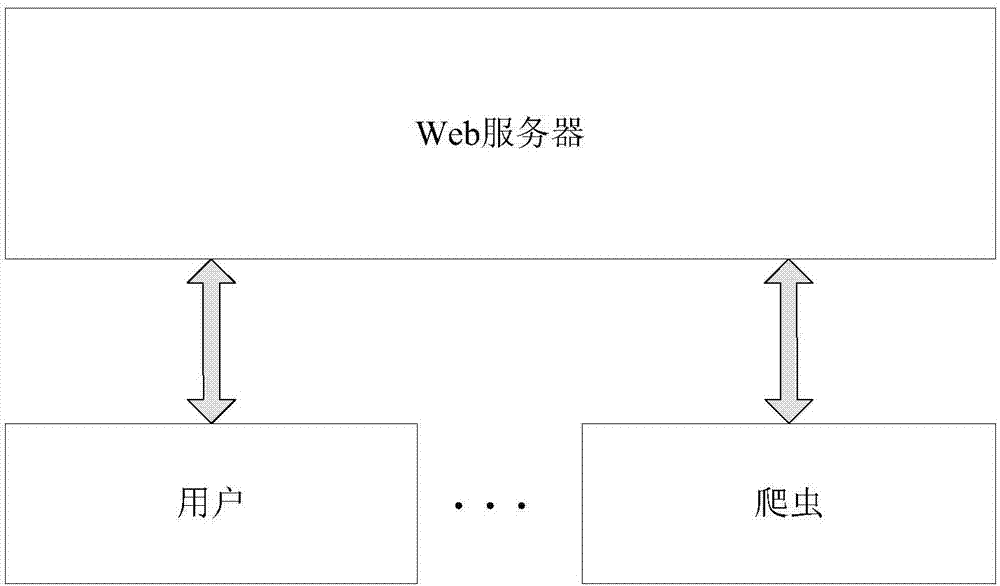
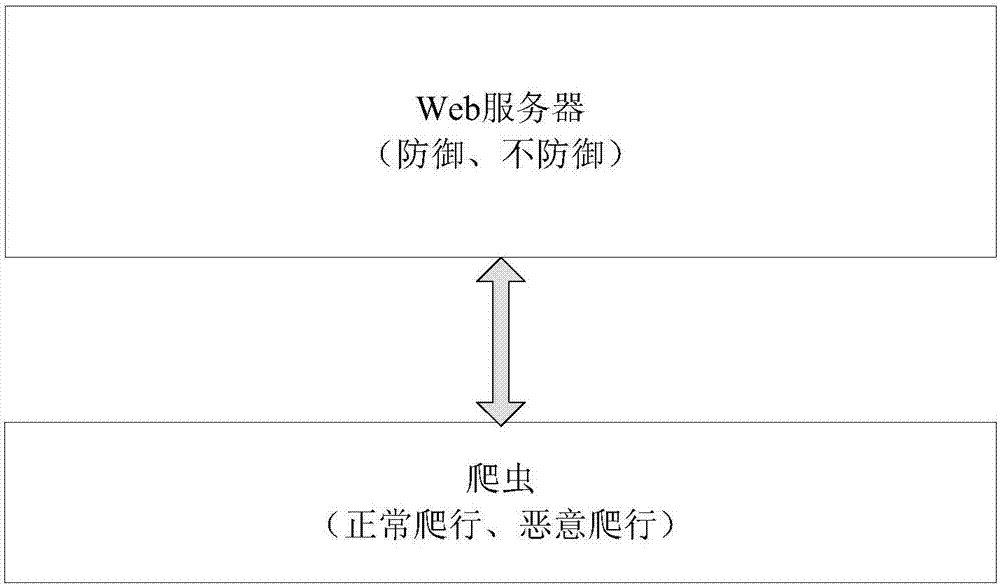
[0031] The benefits and costs are calculated separately for the web server and the crawler. For a web server, the strategies it can adopt include defensive and non-defensive, while for crawlers, its strategies include normal crawling and malicious crawling. Under different strategies, the price they pay and the benefits they get are related to many different factors, and the calculation needs to be calculated separately according to the strategy.
[0032] (1) Web server
[0033] When the web server chooses a defense strategy, it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com