Credit card fraud prevention verification method and apparatus
A verification method and input verification technology, applied in the field of network information security, can solve the problems of not reaching the interaction between the anchor and the audience, and the audience being unable to obtain gifts, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
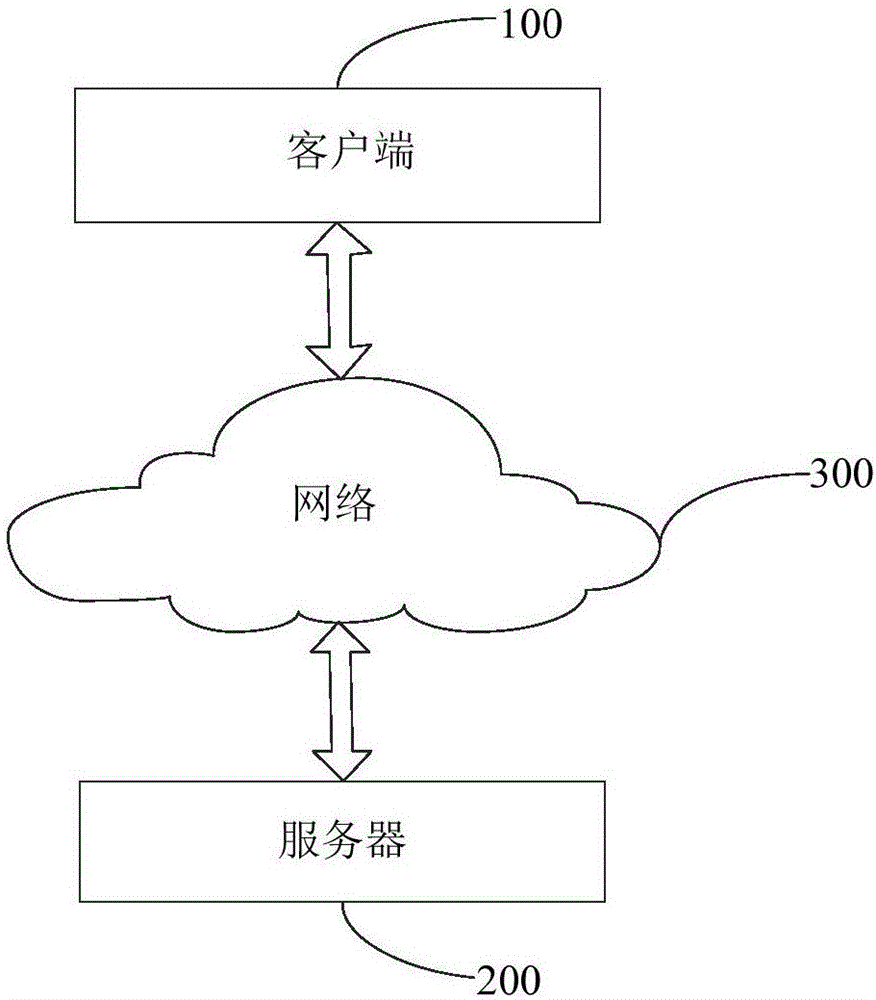
[0083] Please refer to Figure 4 , Figure 4 It is a schematic flow chart of the verification method for preventing brushing provided by a preferred embodiment of the present invention. The method is applied to the client 100 and the server 200 communicating with each other, and the specific process of the method is as follows:
[0084] Step S410, the server 200 receives the operation of receiving the gift from the client 100.
[0085]In the live broadcast platform, when performing an interactive activity, the client 100 will display an interactive activity interface, for example, there will be a treasure chest pattern and / or a control to remind the audience to grab a gift. When the viewer clicks on such a pattern or a control, the logic of receiving the gift by the client 100 will be triggered. Now the client 100 will send a response protocol to the server 200, informing the server 200 that there is an operation to receive the gift on the client 100.
[0086] Step S420, t...
no. 2 example
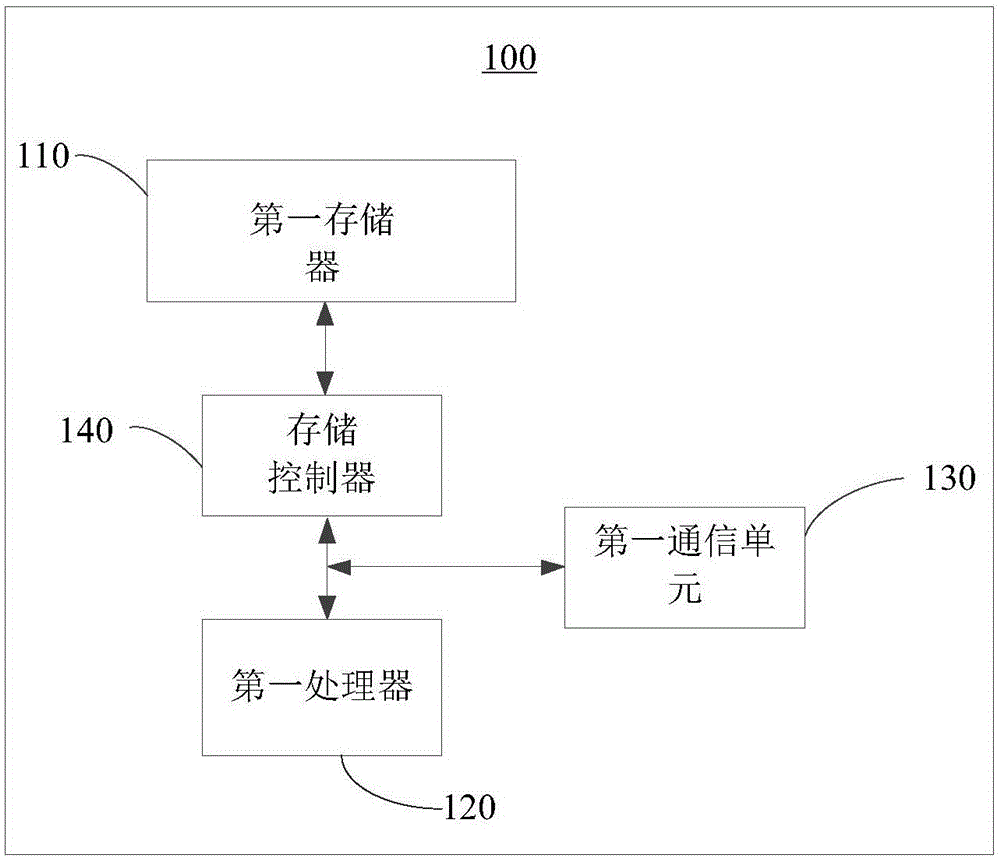
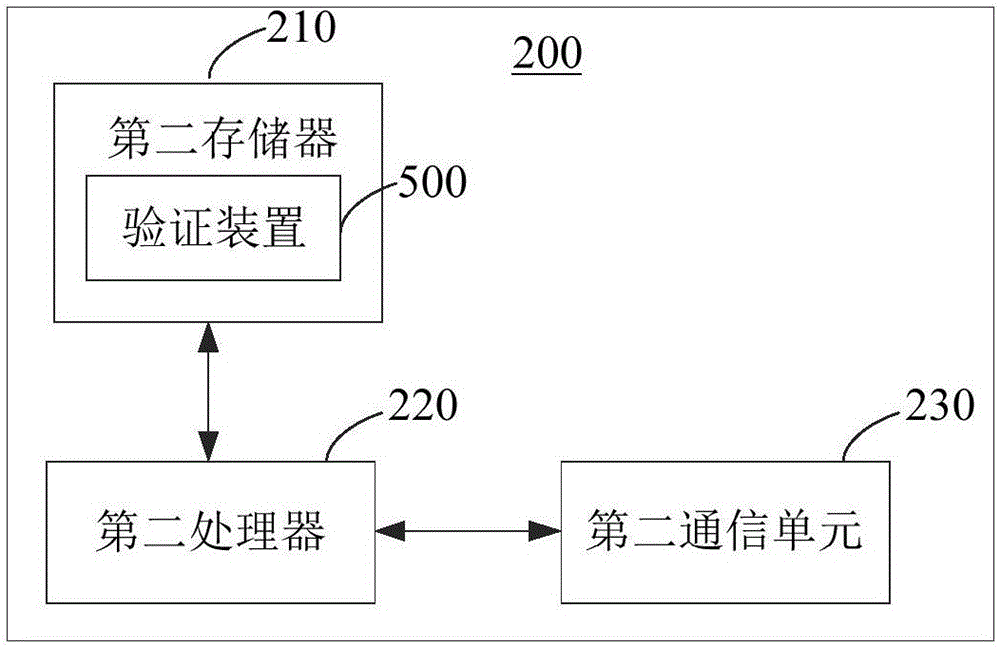
[0150] Please refer to Figure 8 , Figure 8 It is a functional block diagram of the verification device 500 for preventing being swiped provided by the preferred embodiment of the present invention. The verification device 500 is applied to the server 200, and the verification device 500 for preventing being brushed includes a receiving module 510, a recording module 520, a judgment module 530 and a verification module 540.
[0151] The receiving module 510 is configured to receive the operation of receiving the gift from the client 100.
[0152] The receiving module 510 is used to execute Figure 5 For step S410 in , please refer to step S410 for the specific description, and will not repeat it here.
[0153] The record module 520 is used to obtain the number of times the client 100 receives gifts.
[0154] The recording module 520 is used to execute Figure 5 For step S420 in , please refer to step S420 for the specific description, and will not repeat it here.
[015...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com