Malicious user identification method based on som neural network in cognitive radio
A cognitive radio and neural network technology, applied in network planning, wireless communication, electrical components, etc., can solve problems such as data loss and the impact on the accuracy of judgment results, and achieve the effect of broad development space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
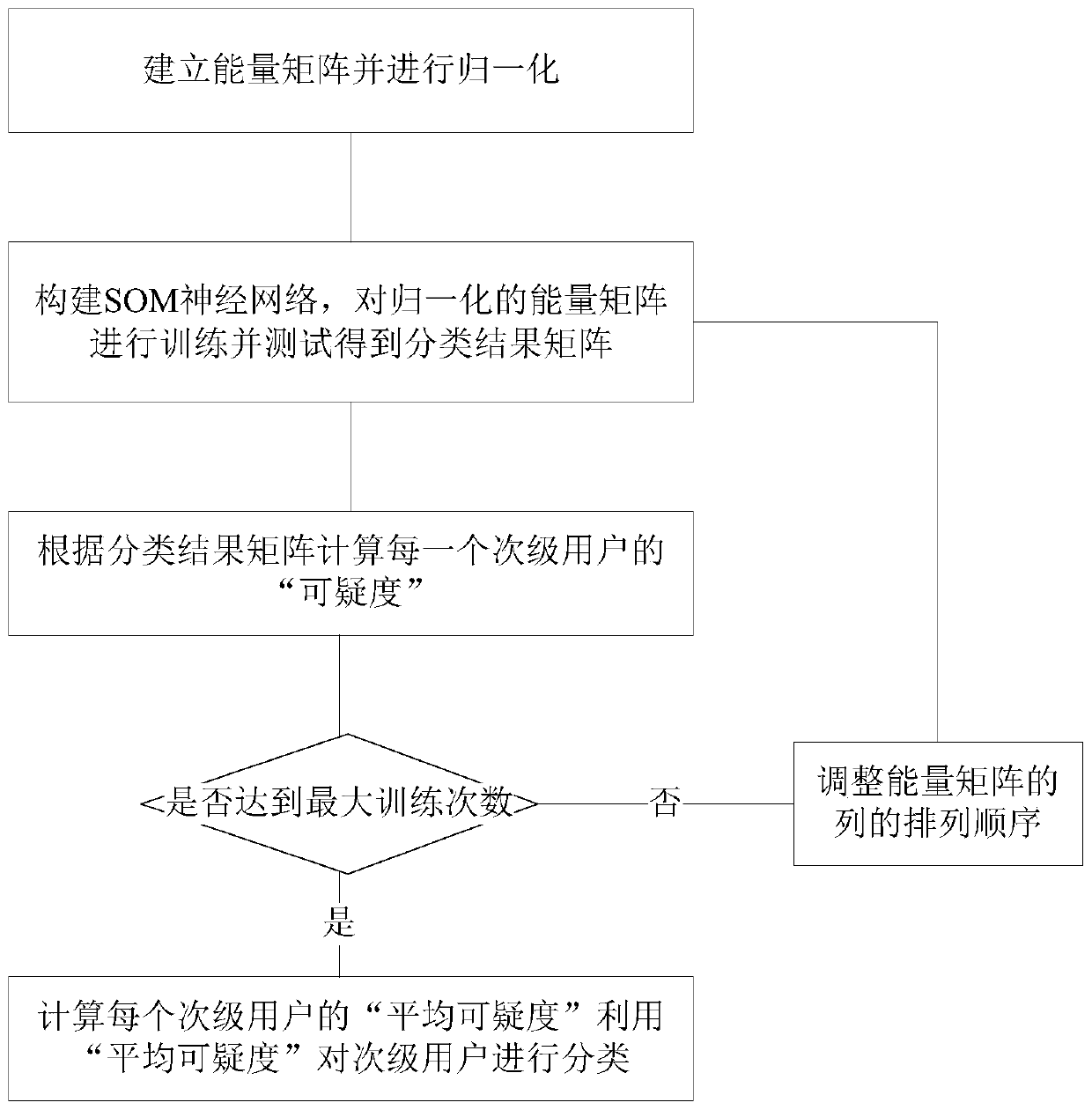
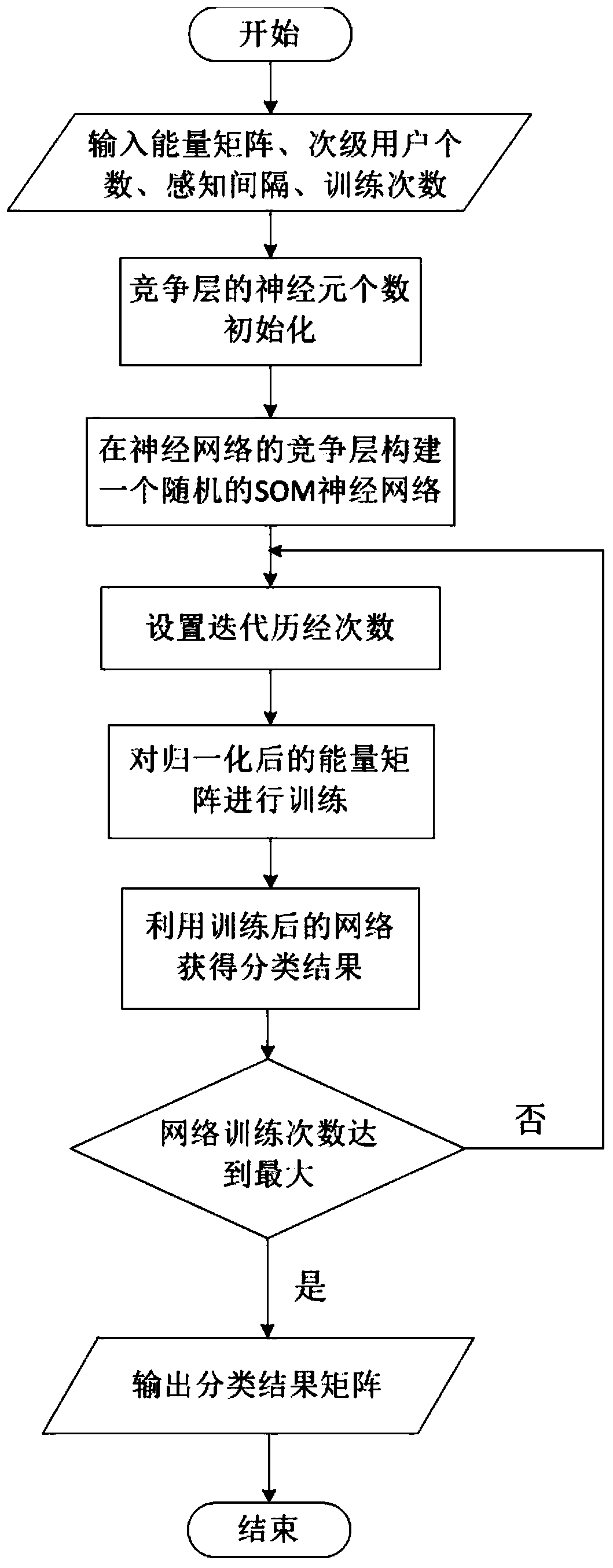
[0038] Below in conjunction with specific embodiment, further set forth the present invention, should be understood that these embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention, after having read the present invention, those skilled in the art will understand various equivalent forms of the present invention The modifications all fall within the scope defined by the requirements of this application.
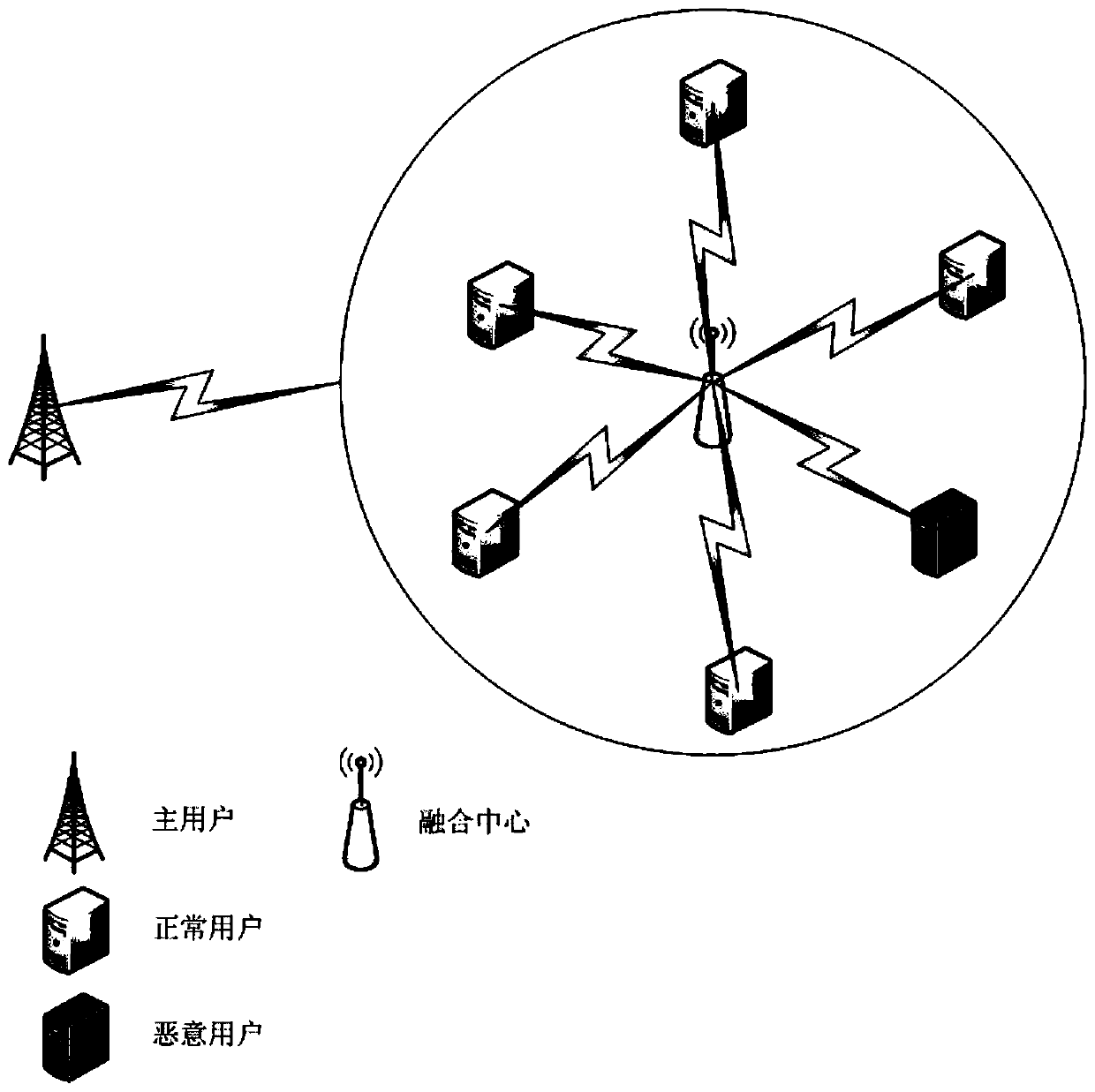
[0039] figure 1 A central cooperative spectrum sensing model is shown, which includes a primary user, a fusion center and J secondary users, and these secondary users include several malicious users. In this model, the secondary users are independent from each other, and all local sensing signals are sent to the fusion center for decision simultaneously. Assume that each secondary user samples N times and adopts energy detection. Taking the jth user as an example, the statistics of its energy value can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com