Service data packet encapsulating method and device
A technology for data packets and services, which is applied in network data management, secure communication devices, digital transmission systems, etc., and can solve problems such as high network overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
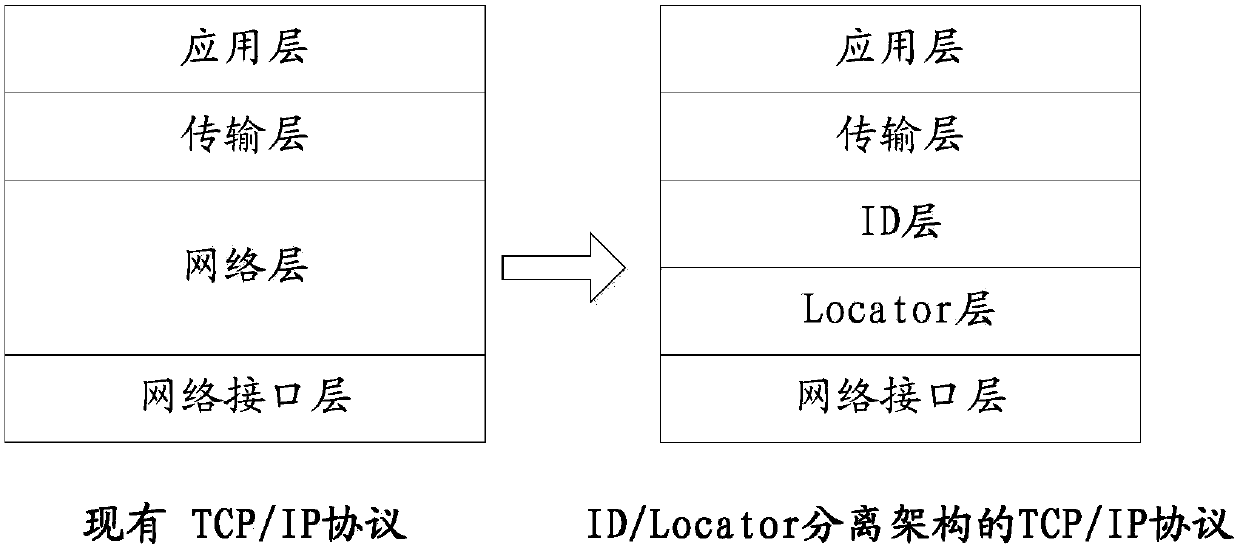
[0092] TCP / IP protocol (Transmission Control Protocol / Internet Protocol, Transmission Control Protocol / Internet Internet Protocol), is the most basic communication protocol of the Internet. Such as figure 1 As shown, the TCP / IP protocol is mainly composed of four layers, which are application layer, transport layer, network layer and network interface layer from top to bottom. due to figure 1 In the shown TCP / IP protocol architecture, the IP address at the network layer assumes the dual roles of communication device identity and location identification, and this dual role limits the mobility, security, and multi-platform accessibility of communication devices. In view of the above, those skilled in the art have proposed such as figure 1 The TCP / IP protocol of the shown ID ((identification, identity mark) and Locator (location mark). Wherein, the TCP / IP protocol includes five layers, which are respectively application layer, transport layer, ID layer from top to bottom layer...
Embodiment 2
[0117] In practical applications, the destination communication device can adopt the TCP / IP communication protocol with ID / Locator separation architecture, or the TCP / IP communication protocol with ID / Locator non-separation architecture (that is, the traditional TCP / IP four-layer communication protocol) , and for the destination communication device using the ID / Locator separation architecture and the destination communication device without the ID / Locator separation architecture, the source communication device obtains the destination ID and the destination Locator in different ways, so the source communication device before encapsulating the data packet , it is necessary to first determine the TCP / IP communication protocol architecture adopted by the destination communication device.
[0118] In the embodiment of the present invention, such as Figure 6 As shown, the following methods can be used to obtain the communication protocol architecture of the destination communicat...
Embodiment 3
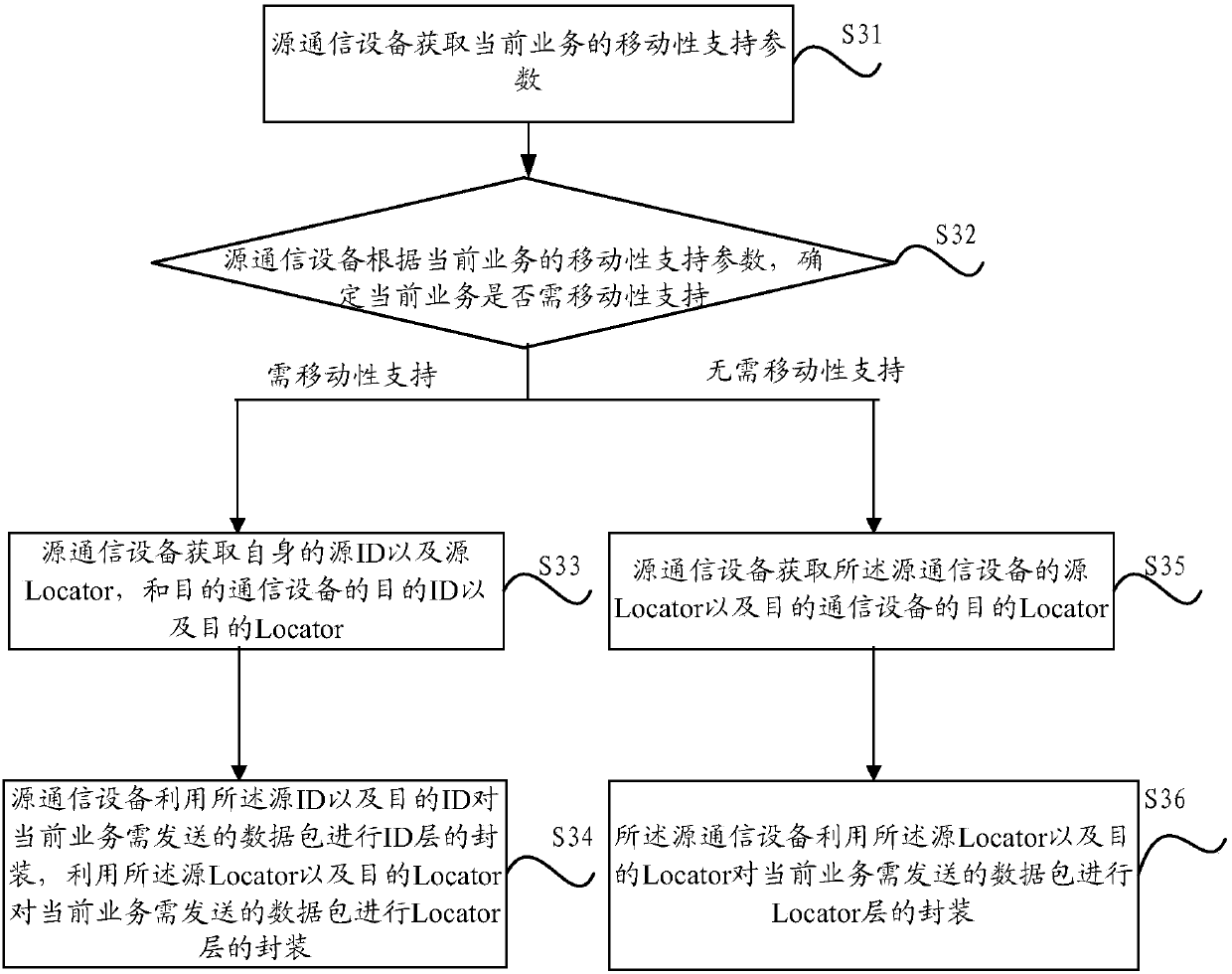
[0143] If using any one of the three implementations provided in Embodiment 2, the source communication device determines that the destination communication device adopts the TCP / IP communication protocol of the ID / Locator separation architecture; The data packets to be sent are encapsulated at the application layer and the transport layer, and then steps S31 and S32 in Embodiment 1 are used to determine whether the current service needs mobility support;
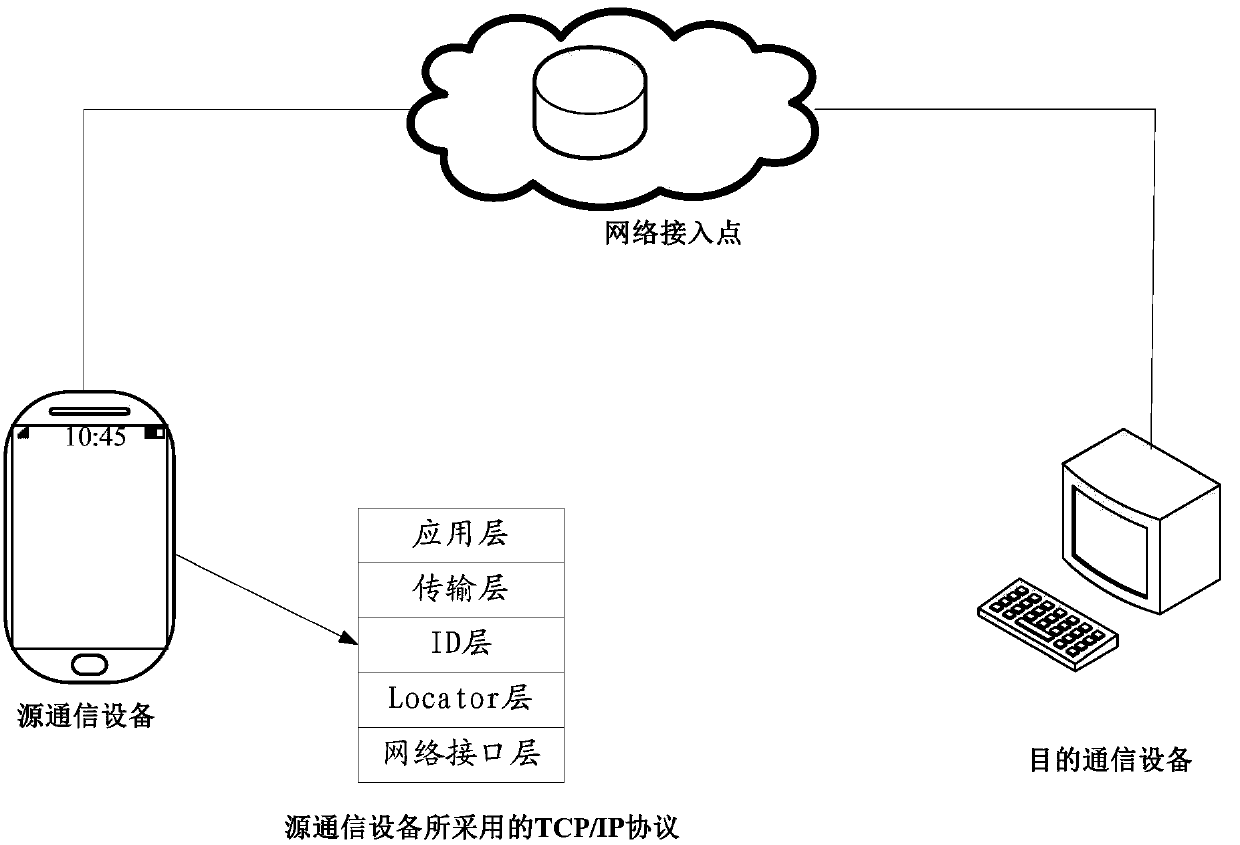
[0144] 1. If the source communication device determines the current service and needs mobility support, its application scenarios can be found in Figure 7 , Step S33 in Embodiment 1: the source communication device acquires the source ID and source Locator of the source communication device, and the destination ID and destination Locator of the destination communication device, as follows:
[0145] The source communication device selects two IP addresses from a preset address pool as the source ID and source Locator respec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com