A cloud wallet management method and server
A management method and wallet technology, applied in the field of information processing, can solve problems such as potential safety hazards, and achieve the effects of improving security, facilitating unified management, and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
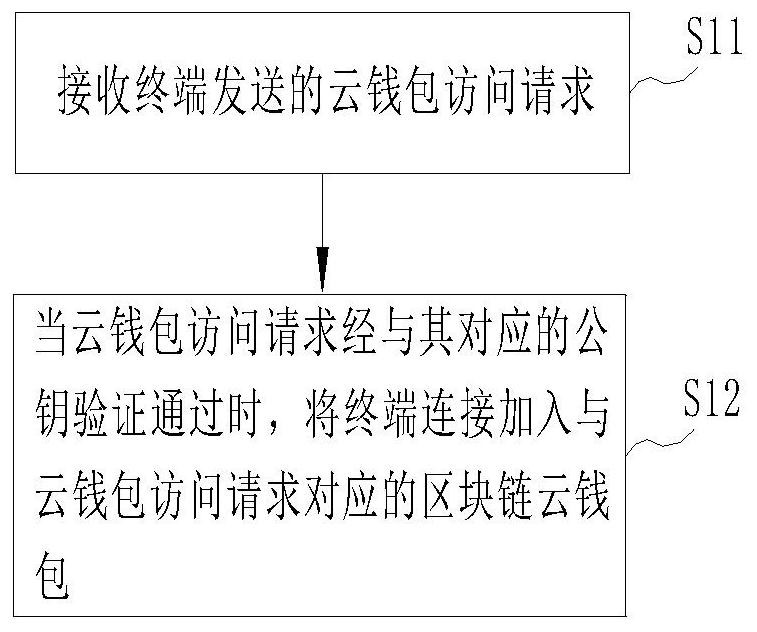
[0036] Embodiment 1 provides a cloud wallet management method, which is applied to a server in the cloud, such as figure 1 As shown, it includes the following steps:
[0037] Step S11: Receive the cloud wallet access request sent by the terminal.
[0038] Step S12: When the cloud wallet access request is verified by the corresponding public key, connect the terminal to the blockchain cloud wallet corresponding to the cloud wallet access request.
[0039] In order to successfully complete the cloud wallet access, the cloud wallet access request sent by the terminal should at least include user information, so that the server can identify the blockchain cloud wallet corresponding to the user. In addition, in order to ensure the safe operation of the cloud wallet, the cloud wallet access request should also include the signature generated by the private key stored in the terminal, so that the server can use the public key corresponding to the user information stored in it to ver...
Embodiment 2
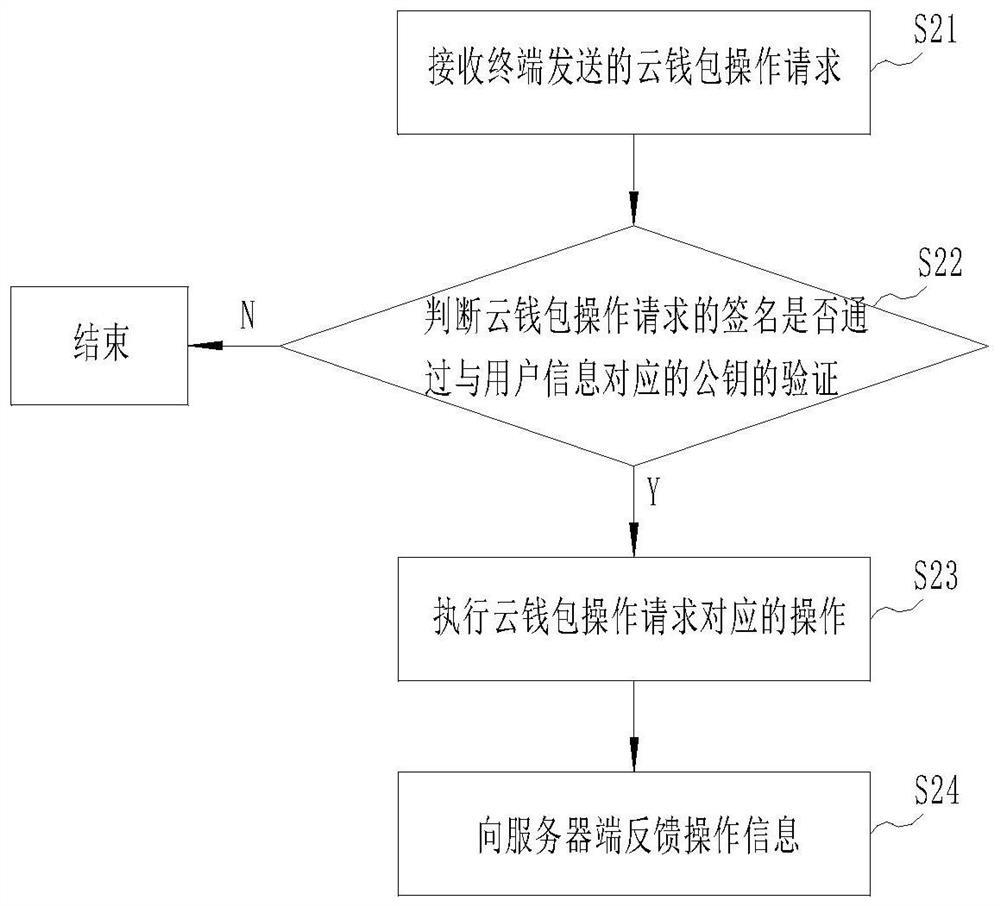
[0042] Embodiment 2 provides a cloud wallet management method, which is applied to a server in the cloud, such as figure 2 As shown, it includes the following steps:
[0043] Step S21: Receive the cloud wallet operation request sent by the terminal. The cloud wallet operation request includes user information and is signed by the private key stored in the terminal.
[0044] Step S22: Determine whether the signature of the cloud wallet operation request has passed the verification of the public key corresponding to the user information.
[0045]Step S23: When the signature of the cloud wallet operation request is verified by the public key corresponding to the user information, perform the operation corresponding to the cloud wallet operation request. When the signature of the cloud wallet operation request fails the verification of the public key corresponding to the user information, just end.
[0046] Step S24: Feedback the operation information to the server. After the...
Embodiment 3
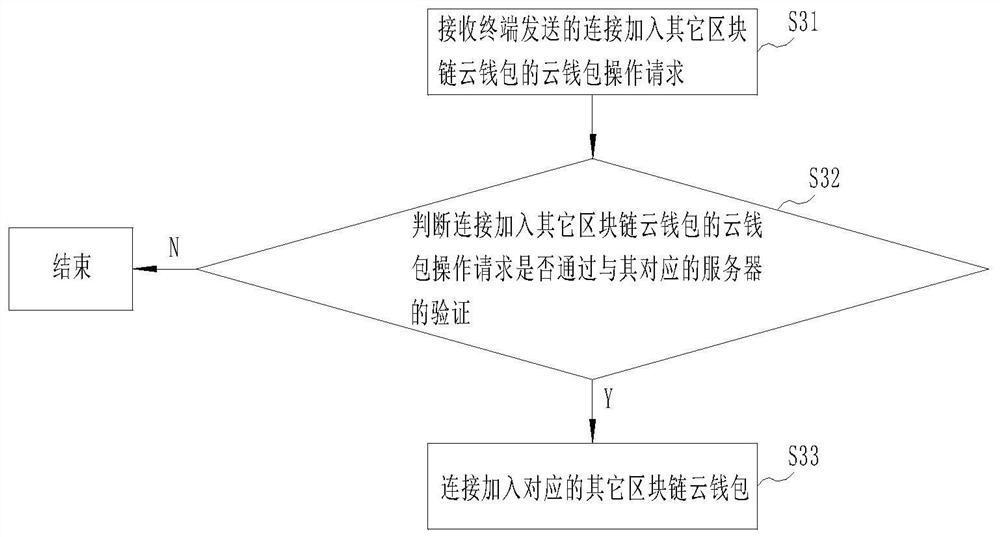
[0049] Embodiment 3 provides a cloud wallet management method, which is applied to a cloud server. The cloud wallet management method provided in embodiment 3 discloses specific methods for connecting and joining other blockchain cloud wallets, such as image 3 As shown, it includes the following steps:
[0050] Step S31: Receive the cloud wallet operation request sent by the terminal to join other blockchain cloud wallets.
[0051] Step S32: Determine whether the cloud wallet operation request to connect to other blockchain cloud wallets passes the verification of the corresponding server. The management operations of other blockchain wallets do not necessarily use the mechanism of public and private key signatures for identity authentication. It can be operated and managed according to the identity authentication mechanism of other blockchain cloud wallets. In other words, mobile terminals can manage blockchain cloud wallets of different manufacturers through remote conne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com