Dynamic encryption system based on all-prime-number library
A dynamic encryption, prime number technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
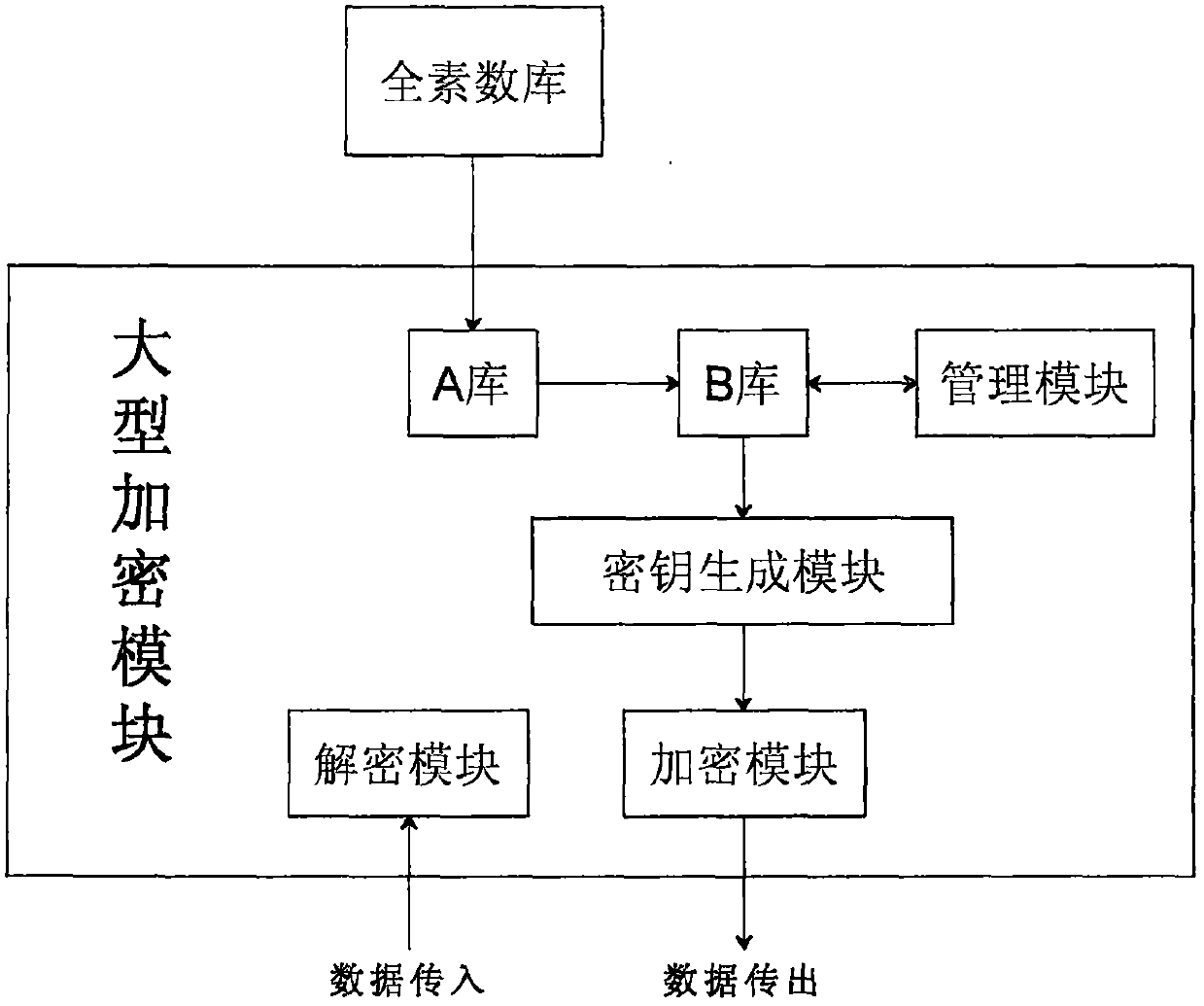
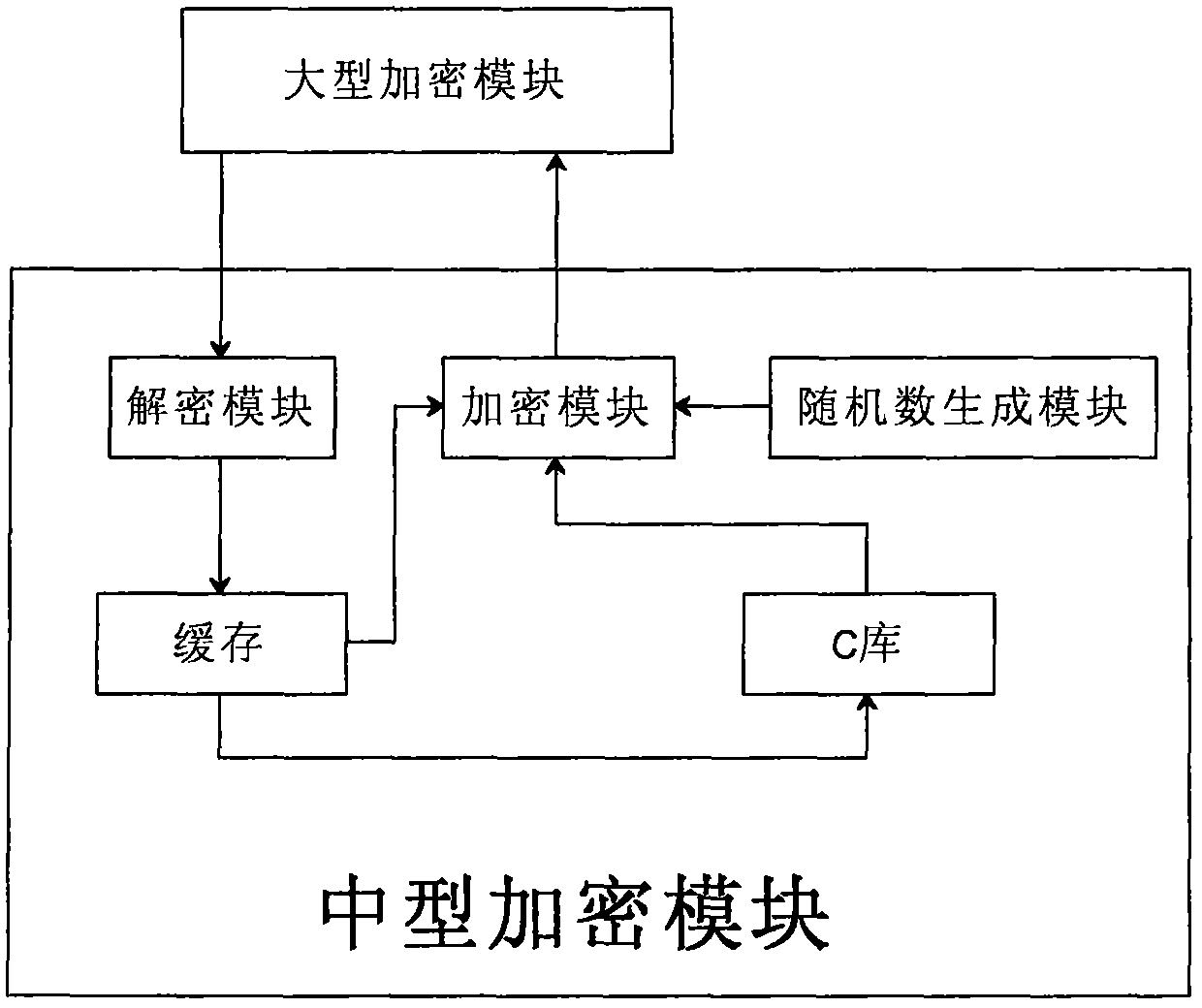
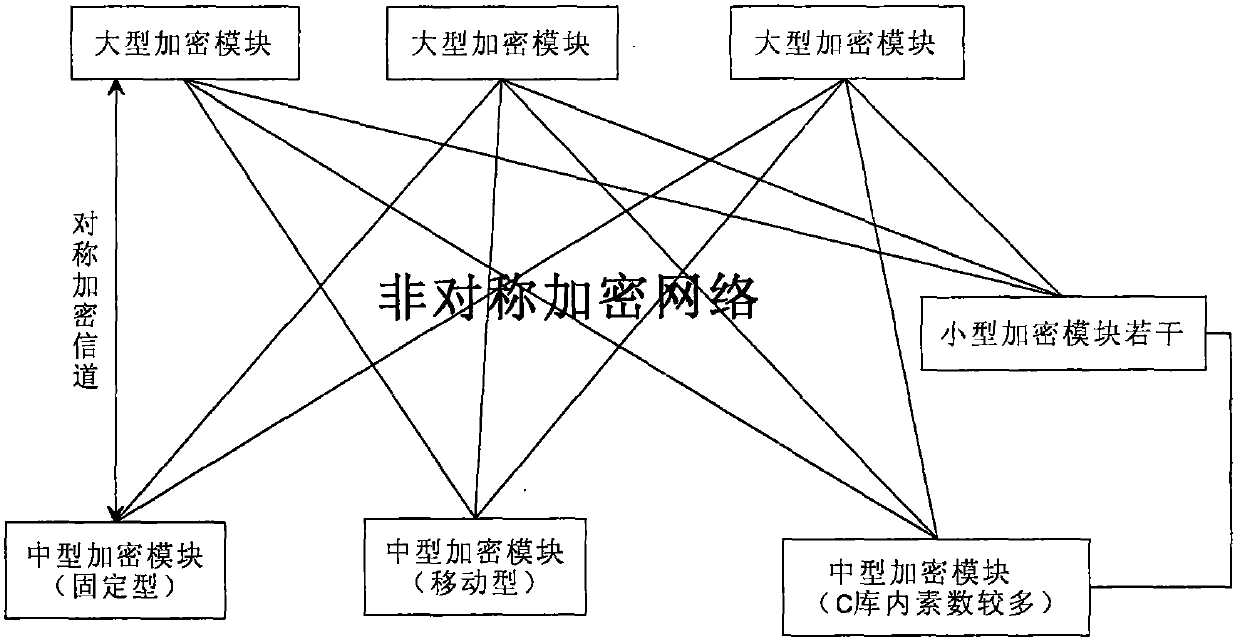
[0038] The large encryption module stores a complete full prime number library. If a special prime number is needed during use, the full prime number library is first screened into a special prime number library. When in use, it is divided into two libraries, one is called standard prime number library A, which is used for backup; the other is called residual prime number library B, which is officially used prime number library. When using for the first time, copy B 1 Library = A library, and B 1 The library is added to the B library, that is, the B library = B 1 Library. Every time a prime number is used, a prime number is randomly selected from the B library and the used prime number is deleted. System real-time record B 1 The remaining prime numbers in the library. When B 1 When the remaining primes in the library are less than the specified ratio k%, the second copy B 2 Library = A library, and B 2 The library is added to the B library, that is, the B library = B 1 Library...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com