Network attack detection method and device, terminal equipment and computer storage medium
A network attack and detection method technology, applied in the field of network security, can solve problems such as low compatibility, and achieve the effect of improving compatibility and facilitating the judgment process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
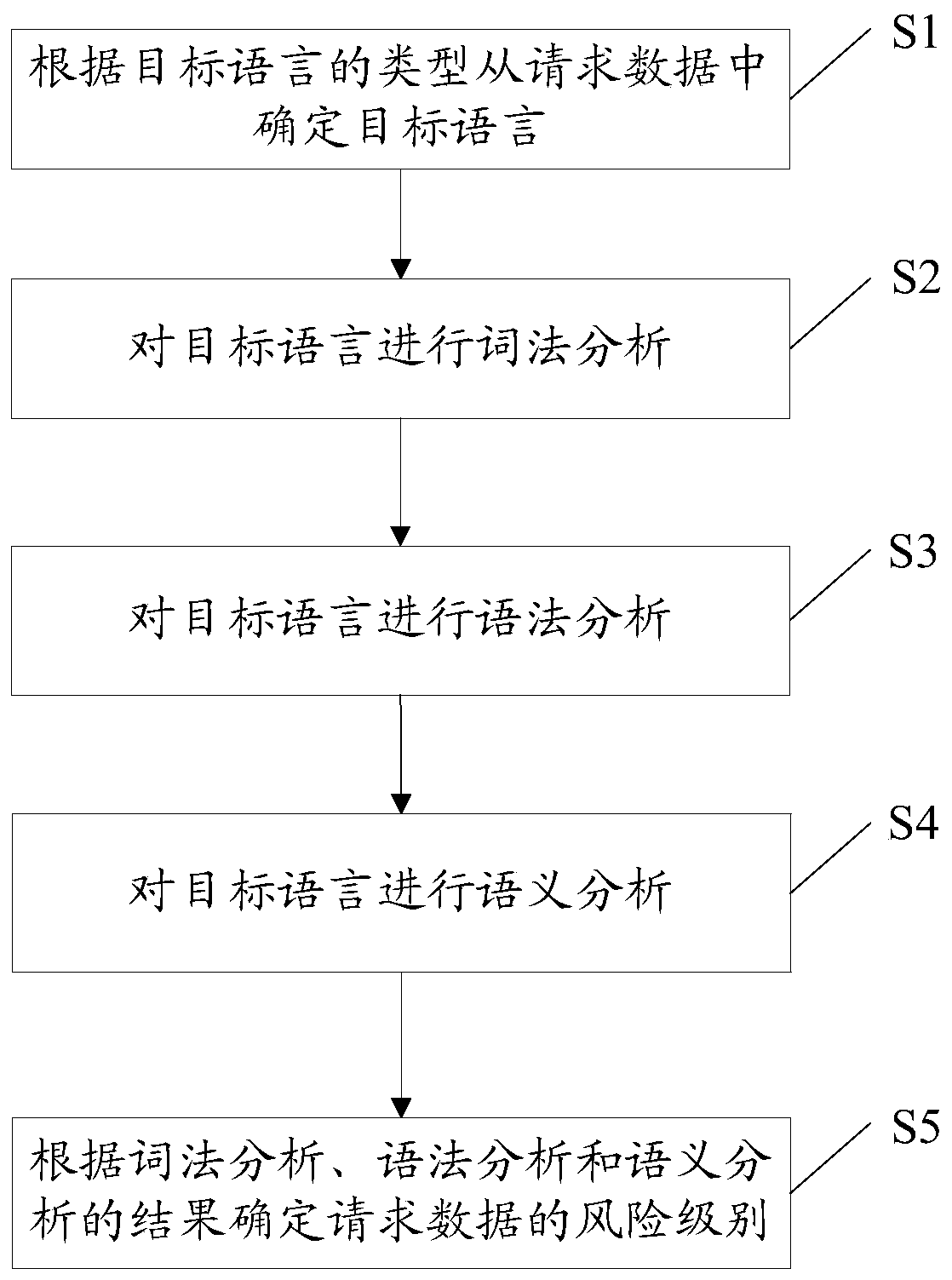
[0156] figure 1 It is a flow chart of the method for detecting a network attack according to Embodiment 1 of the method of the present invention. see figure 1 , in this embodiment, the method includes:
[0157] S1: Determine the target language from the request data according to the type of the target language.
[0158] S2: Perform lexical analysis on the target language.
[0159] S3: Perform grammatical analysis on the target language.
[0160] S4: Perform semantic analysis on the target language.
[0161] S5: Determine the risk level of the requested data according to the results of the lexical analysis, syntax analysis, and semantic analysis.
[0162] Aiming at the problems in the prior art, the present invention proposes a detection method applicable to different types of network attacks (such as SQL injection attacks, XSS attacks and PHP (Hypertext Preprocessor, a general open source scripting language) code injection attacks, etc.).
[0163] Among them, SQL injecti...
Embodiment approach 2
[0174] The method provided in this embodiment includes all the content in method embodiment 1, and details are not repeated here. In this implementation manner, the method further includes: extracting the payload data (payload) from the request data. Specifically, a specified header parameter or request body is parsed from the request data; and the header parameter or request body is decoded to obtain the payload data.
[0175] Wherein, the header parameters include a combination of one or more of the following: Request URL parameters, Referer parameters, cookie parameters and User-Agent parameters.
[0176] Taking the HTTP (HyperText Transfer Protocol, hypertext transfer protocol) protocol as an example, the HTTP header usually includes a general header, a request header, a response header, and an entity header. Each header consists of three parts: domain name, colon (:) and domain value. Among these headers, some header parameters may contain malicious attack information e...
Embodiment approach 3
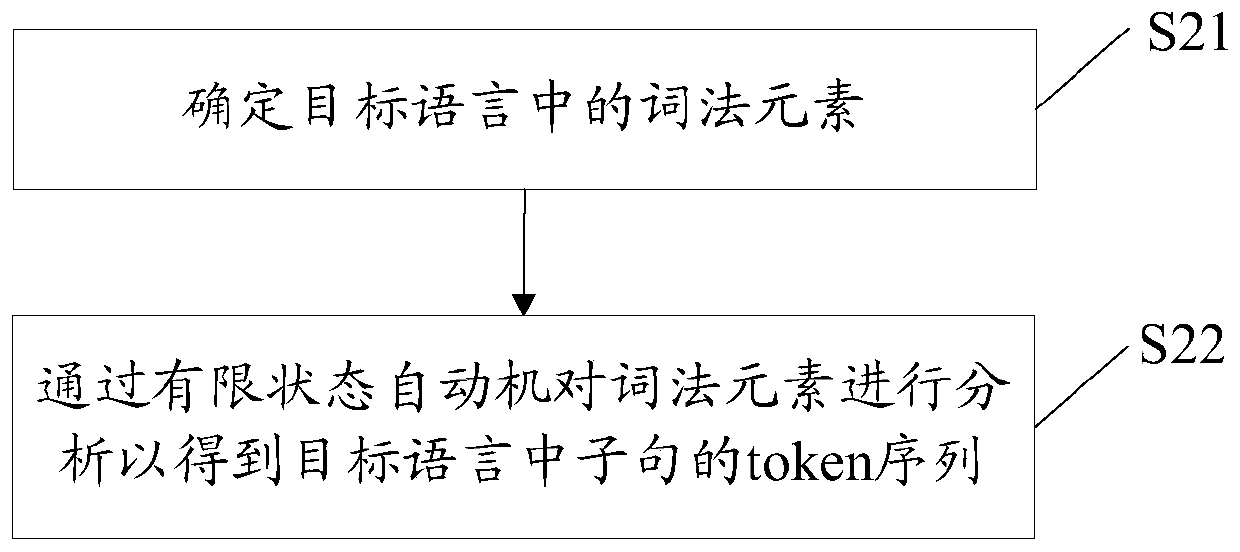
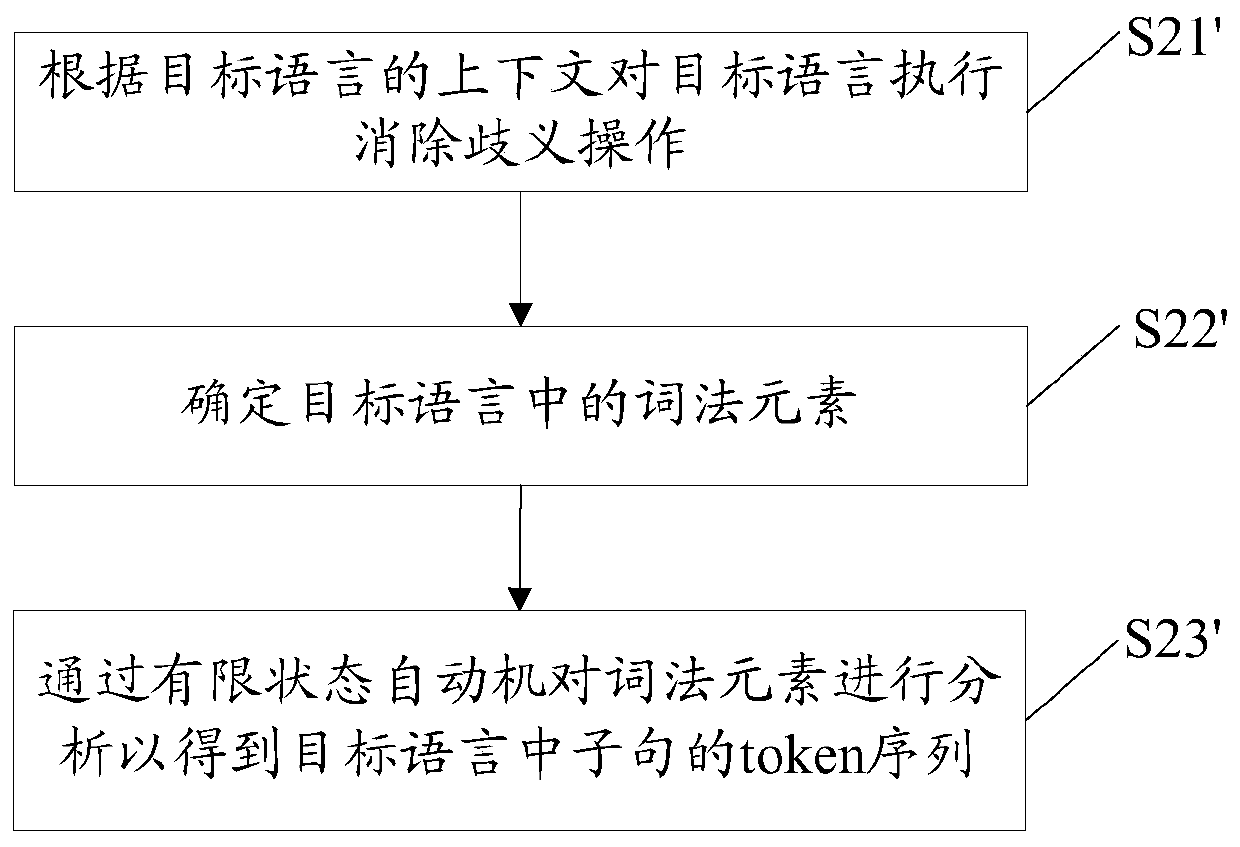
[0187] The method provided in this implementation manner includes all the content in the method implementation manner 1 or the method implementation manner 2, and details are not repeated here. Such as figure 2 As shown, in this embodiment, processing S2 is realized in the following manner:
[0188] S21: Determine the lexical elements in the target language.
[0189] S22: Analyze the lexical elements by using a finite state automaton to obtain a token sequence of clauses in the target language.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com