Starting method, and method and device for generating kernel image
A kernel image and kernel technology, applied in the booting method and device, and the field of booting the kernel, can solve problems such as the inability to effectively guarantee the security of the kernel and the vulnerability of the kernel to attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
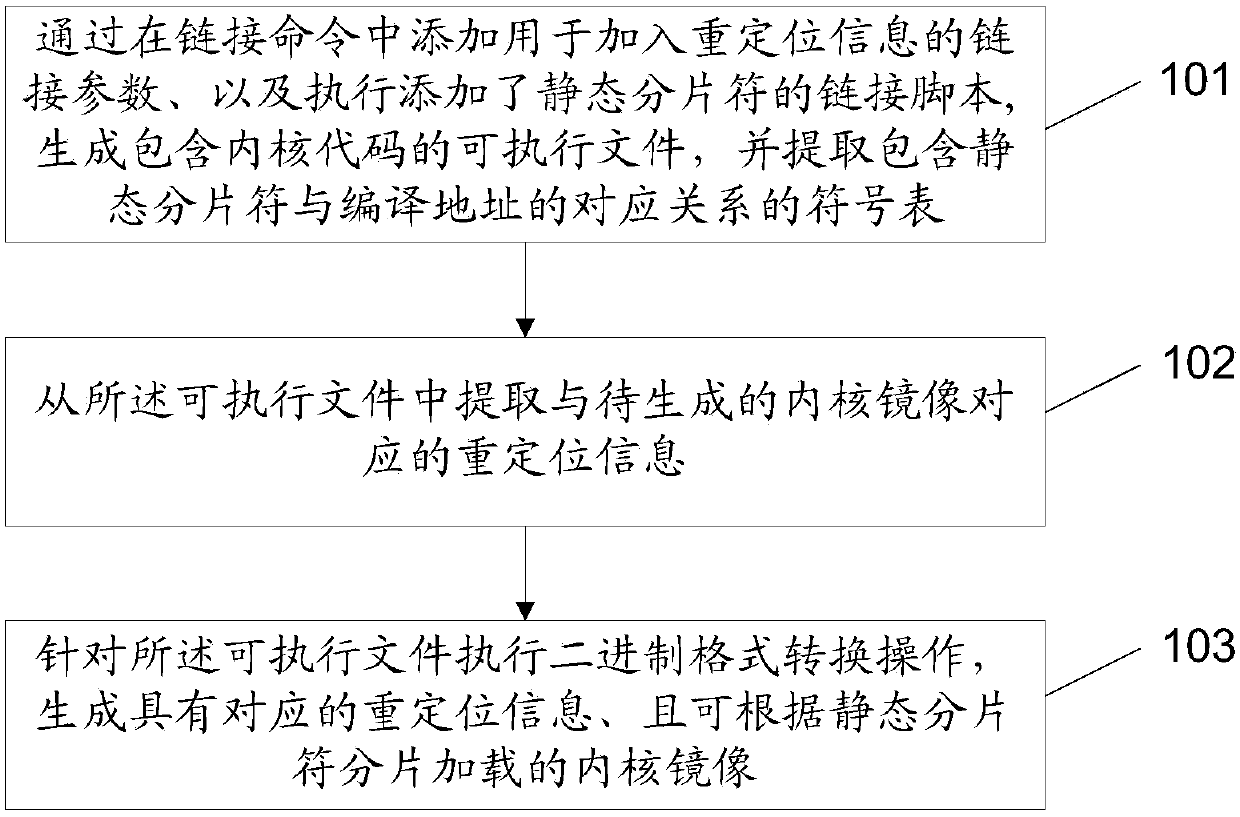
[0188] In this embodiment, the size of each sub-area in the kernel loading space is dynamically adjusted during the process of copying kernel image fragments. Specifically include steps 301-1 to 301-7 as shown below, combined below Figure 5 for further clarification.
[0189] Step 301-1. Determine the number of kernel image segments and the start and end identifiers of each kernel image segment.
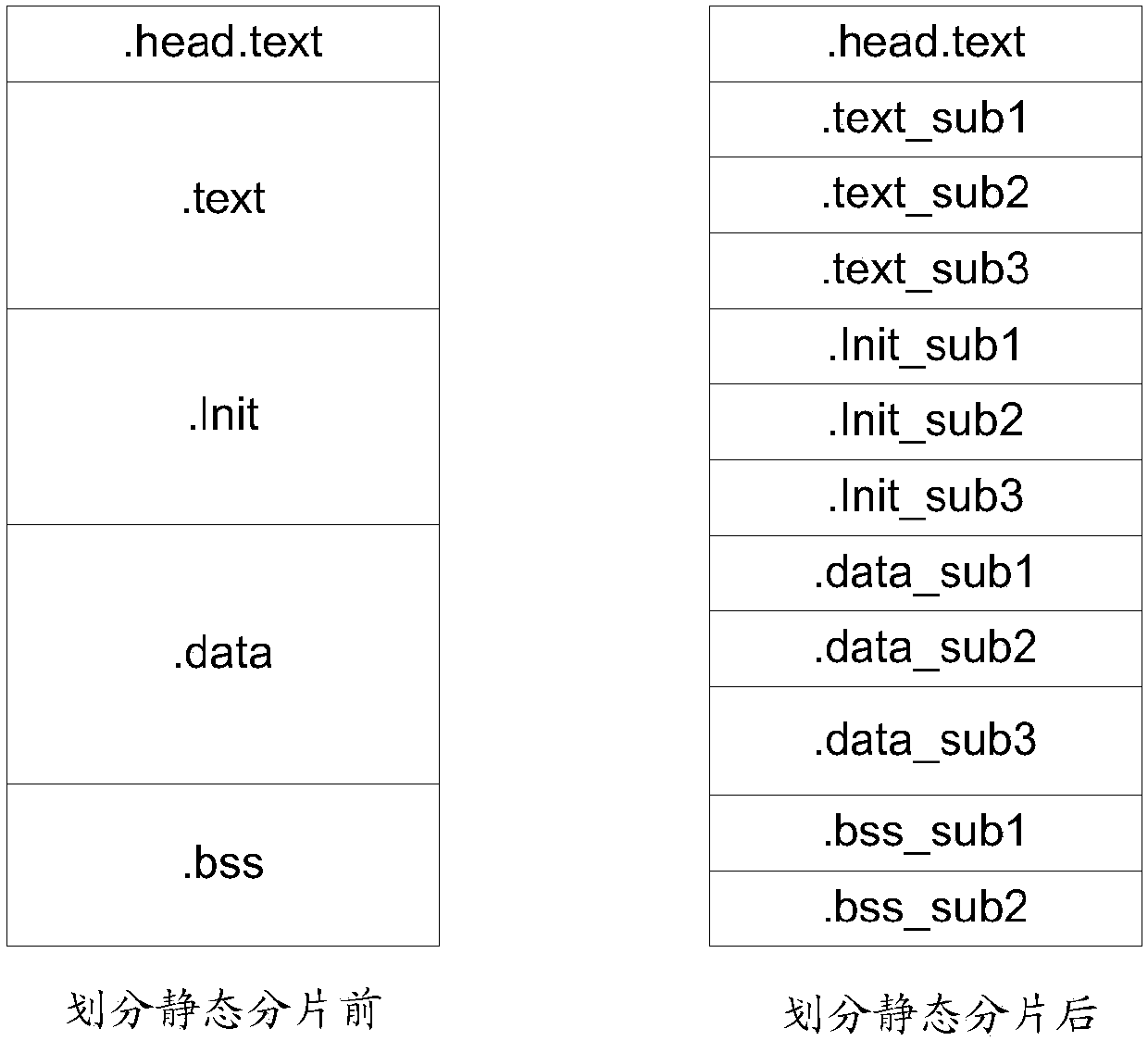
[0190] For the embodiment that obtains the kernel image fragmentation according to the static fragmentation only, this step can determine the kernel image fragmentation according to the static fragmentation, that is: the number of static fragmentation and the start and end fragmentation of each static fragmentation .
[0191] As mentioned earlier, there are different ways to add static fragments to the link script used to control the generation of kernel images. For example, you can add a pair for each static fragment to identify the start and end The static fragment of the addre...
Embodiment approach 2
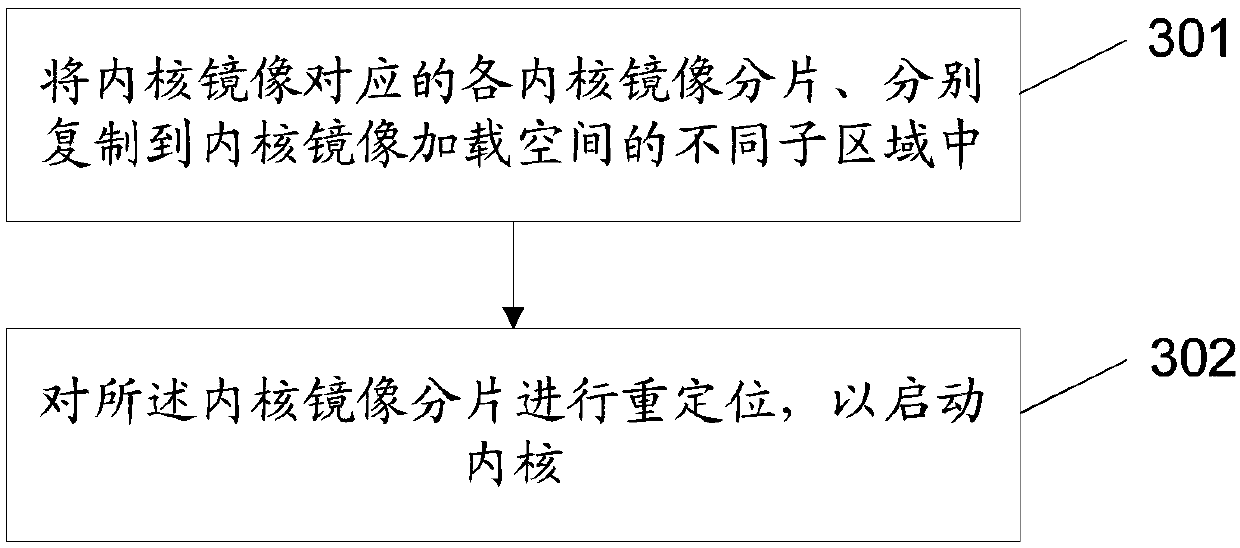
[0212] In this embodiment, each kernel image segment corresponding to the kernel image segment is copied to different sub-areas that have been evenly divided in advance. The specific implementation can be as follows: determine the number of kernel image fragments and the start and end fragment symbols of each kernel image fragment; divide the kernel image loading space into a corresponding number of sub-regions according to the number of kernel image fragments ; Randomly copy the code and / or data contained in different kernel image fragments to different sub-regions of the division according to the corresponding start and end fragments. Wherein, when dividing a corresponding number of sub-regions, different strategies may be adopted, for example, uniform division may be used.
[0213] During specific implementation, the kernel image fragments can be selected sequentially according to the order in the kernel image, and the code and / or data contained in it can be copied to diffe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com