Key protection method and system in open environment
A key protection and key technology, applied in the field of information security, to achieve the effect of network and automation, wide popularity and cost saving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
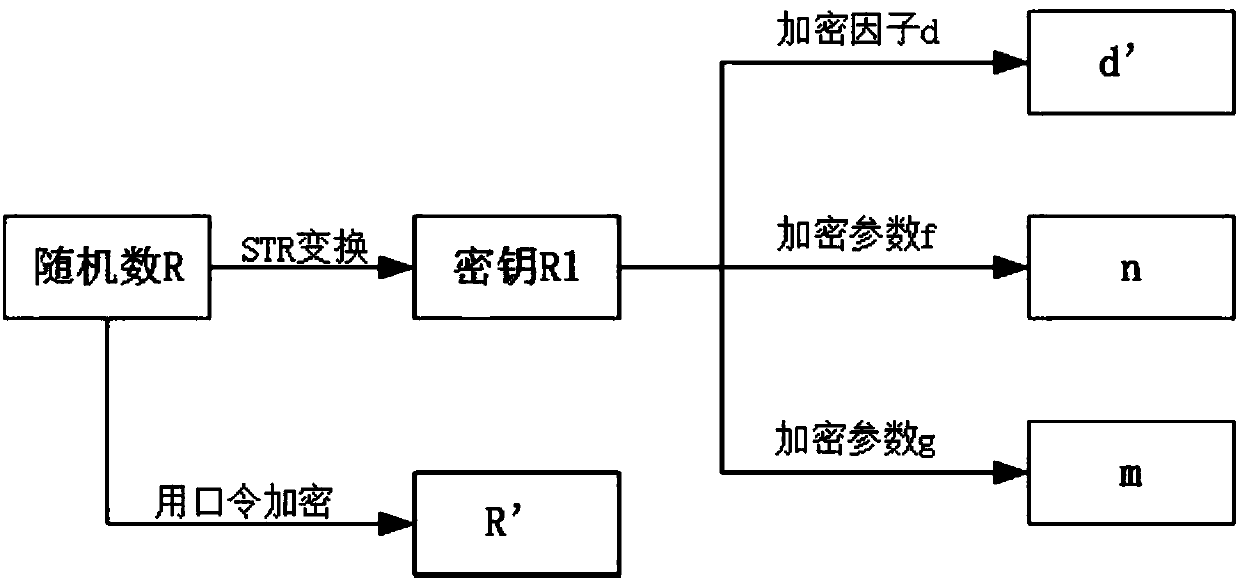
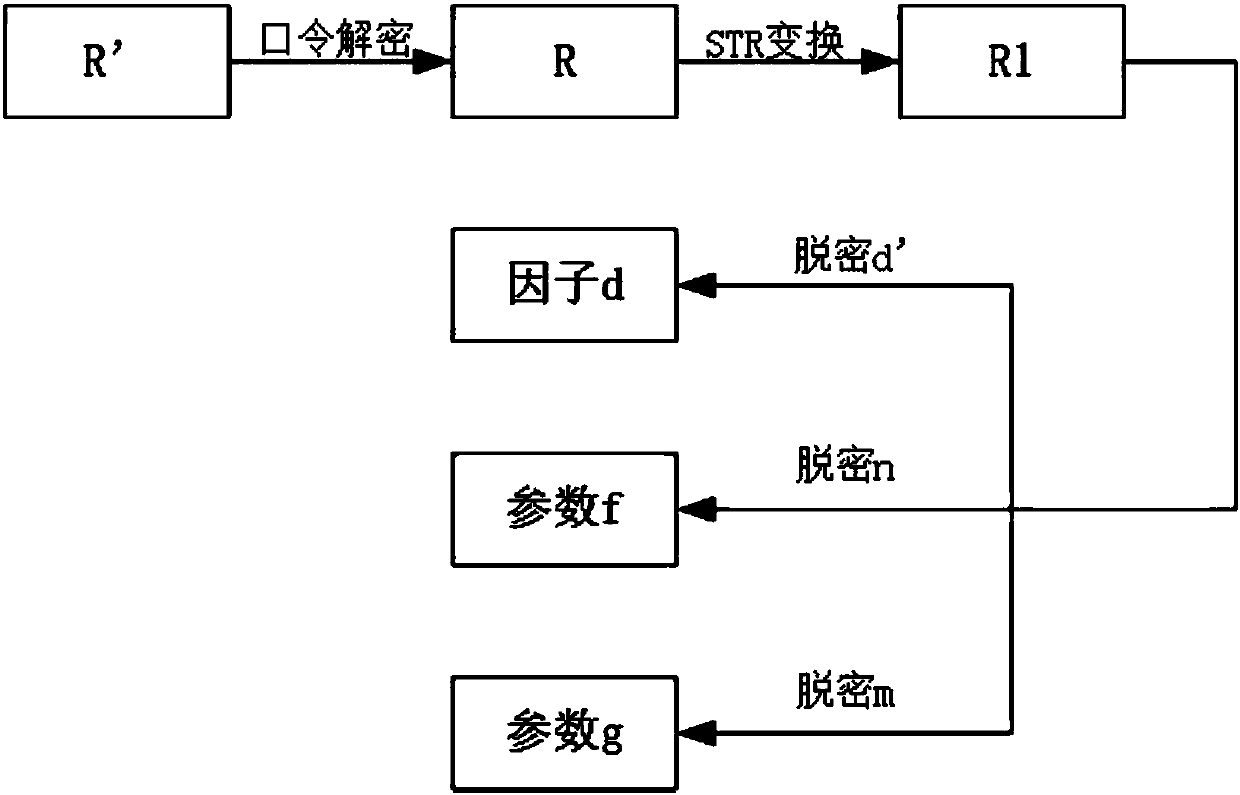
[0050] The key protection system involves two parts, the client and the key center. The client submits a key application, stores the key factor, and uses the key factor to perform related cryptographic operations; the key center is mainly responsible for key production and Decentralization of keys. In the following, we will introduce how to protect the key in the whole life cycle of the key according to the three parts of key application and distribution, key storage and key use.
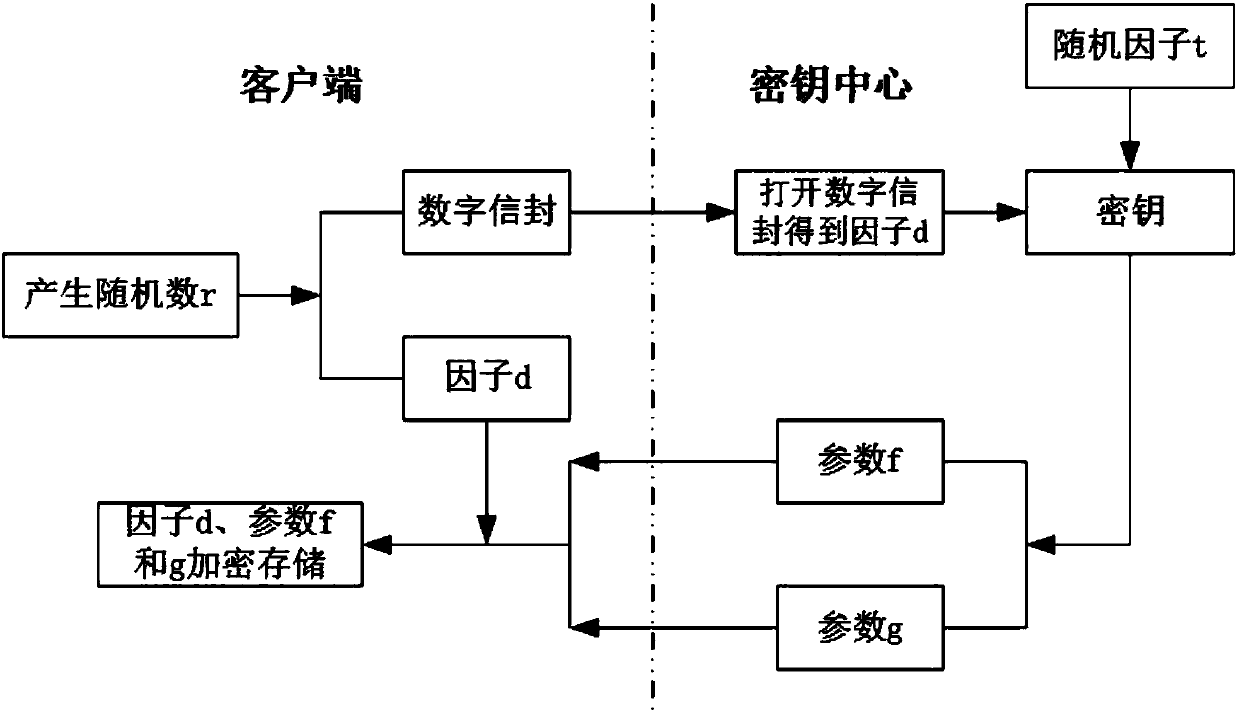
[0051] The protection of the key application and distribution process is divided into the following steps, such as figure 1 Shown: (1) The client generates a random number, calculates the factor d and encrypts the random number with the public key of the key center to generate a digital envelope; (2) sends the digital envelope and user ID to the key center, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com