Identity authentication method, device and system
An identity verification method and identity verification technology, applied in computer security devices, digital data authentication, instruments, etc., can solve problems such as low security, achieve high privacy, improve security, and improve reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment will be described from the perspective of an identity verification device. The identity verification device may be integrated into a network device, such as a terminal or a server. The terminal may include a mobile phone, a tablet computer, a notebook computer or a personal computer (PC, Personal Computer) and other equipment.
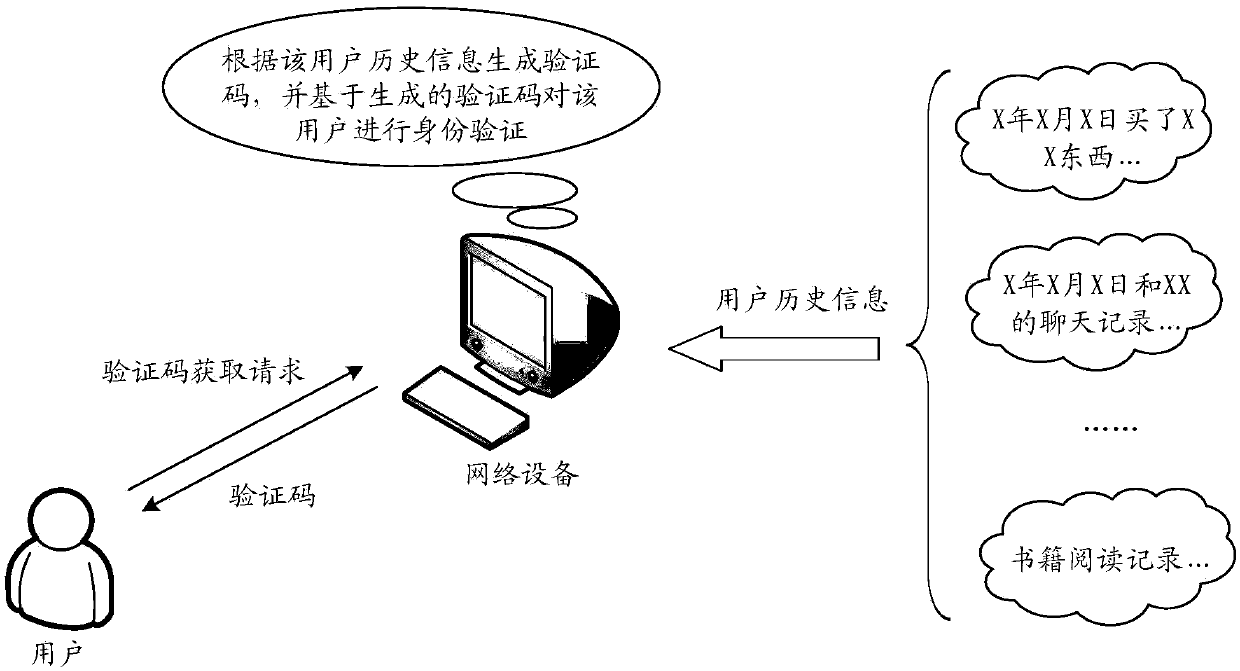
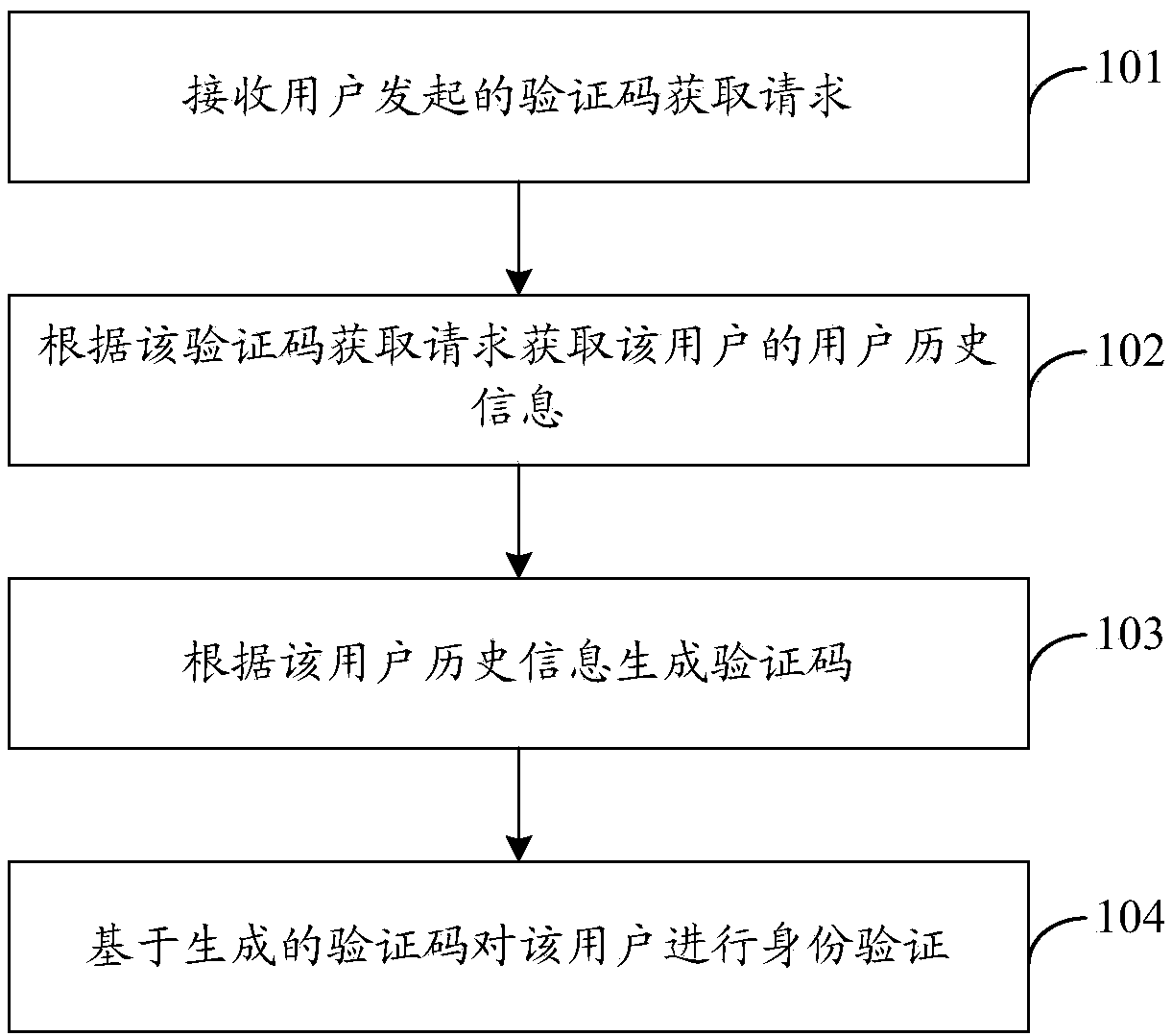
[0032] An identity verification method, comprising: receiving a verification code acquisition request initiated by a user, obtaining user history information of the user according to the verification code acquisition request, generating a verification code according to the user history information, and identifying the user based on the generated verification code verify.
[0033] Such as Figure 1b As shown, the specific process of the authentication method can be as follows:
[0034] 101. Receive a verification code acquisition request initiated by a user.
[0035] For example, a verification code acquisition request triggere...
Embodiment 2
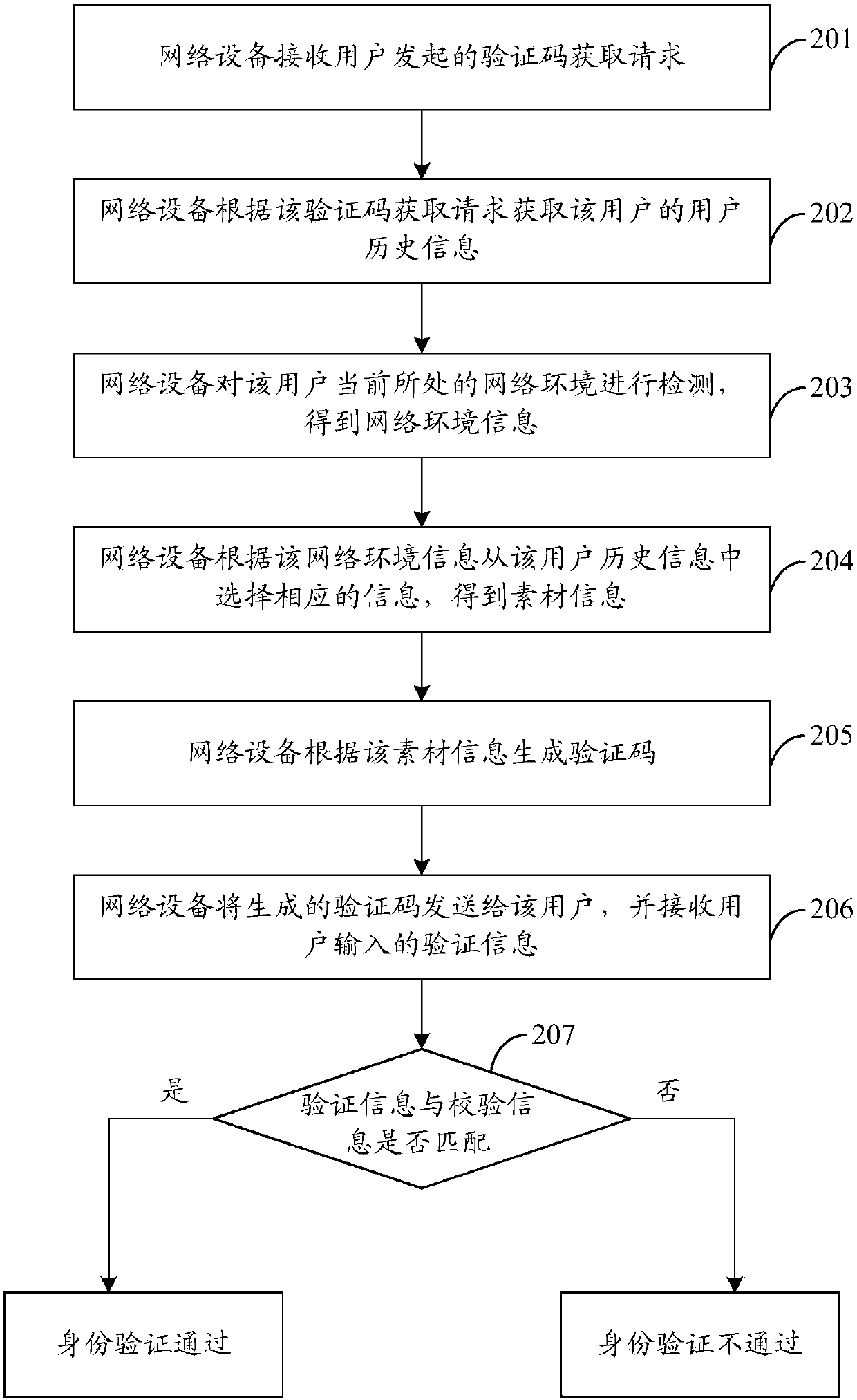
[0068] According to the method described in Embodiment 1, an example will be given below for further detailed description.
[0069] In this embodiment, description will be made by taking the identity verification device integrated in a network device as an example, where the network device may be a terminal or a server.
[0070] Such as figure 2 As shown, an authentication method, the specific process can be as follows:
[0071] 201. The network device receives a verification code acquisition request initiated by a user.
[0072] For example, if the network device is a terminal, at this time, the terminal may receive a verification code acquisition request triggered by a user. Wherein, there may be various ways of triggering, for example, may include clicking, sliding, touching and / or pressing and the like.
[0073] For another example, if the network device is a network-side device such as a server, at this time, the server may receive a verification code acquisition requ...
Embodiment 3
[0106] In order to better implement the above solutions, the embodiment of the present invention also provides an identity verification device, such as Figure 3a As shown, the identity verification device may include a receiving unit 301, an acquiring unit 302, a generating unit 303 and a verifying unit 304, as follows:
[0107] (1) receiving unit 301;
[0108] The receiving unit 301 is configured to receive a verification code acquisition request initiated by a user.
[0109] For example, the receiving unit 301 may be specifically configured to receive a verification code acquisition request triggered by the user by clicking or sliding a preset trigger interface, or may also receive a verification code acquisition request sent by the user through other devices, and so on.
[0110] (2) acquisition unit 302;
[0111] The acquiring unit 302 is configured to acquire the user history information of the user according to the verification code acquisition request.
[0112] For e...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap