Industrial control protocol honey pot with self-learning function oriented to industrial internet and application
An industrial Internet and industrial control protocol technology, applied in the field of network security, can solve the problems of complex attacks on industrial control systems, and achieve the effect of improving deception and enhancing capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention provides a honeypot with a self-learning function oriented to the industrial Internet. In order to enable people in the relevant technical field to better understand the technical solution of the present invention, and to make the purpose and characteristics of the present invention more understandable, The present invention is explained as follows.
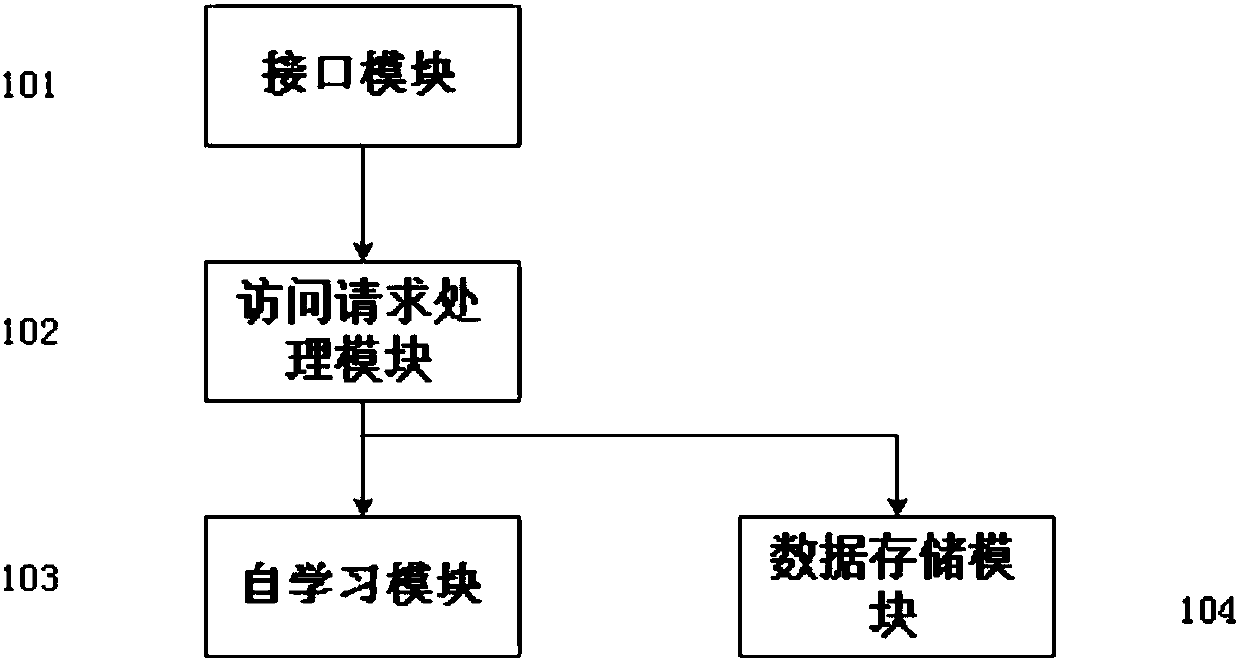
[0022] There are two deployment scenarios for the present invention. One solution is local deployment, where honeynet resources are deployed on a local computer to facilitate the testing and improvement of honeynet programs; Scanning and detection of industrial control environment for subsequent data analysis. After deploying the environment, simulate the communication of the industrial control protocol, construct a deceptive industrial control network environment, and put it in the honeynet host to attract intrusion and collect receipts. like figure 1 shown, including:
[0023] The interface modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com