Virtual machine security monitoring method and system
A security monitoring and virtual machine technology, applied in the field of security protection of cloud platforms, can solve problems such as high performance overhead, and achieve the effect of ensuring security isolation, unification of security and efficiency, and expanding available memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
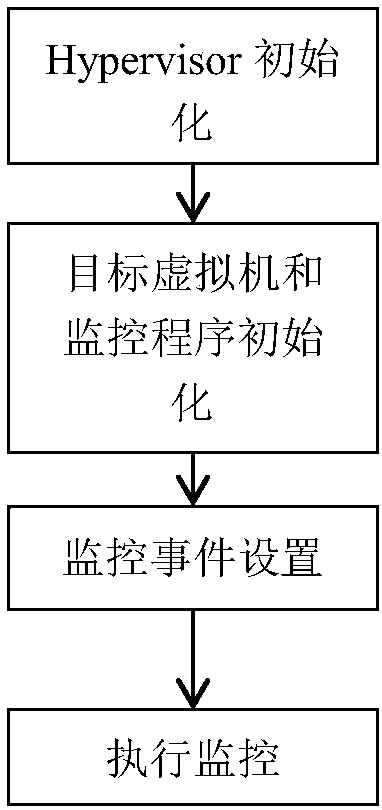
[0029] Such as figure 1 As shown, the virtual machine security monitoring method of the present invention includes the following steps:
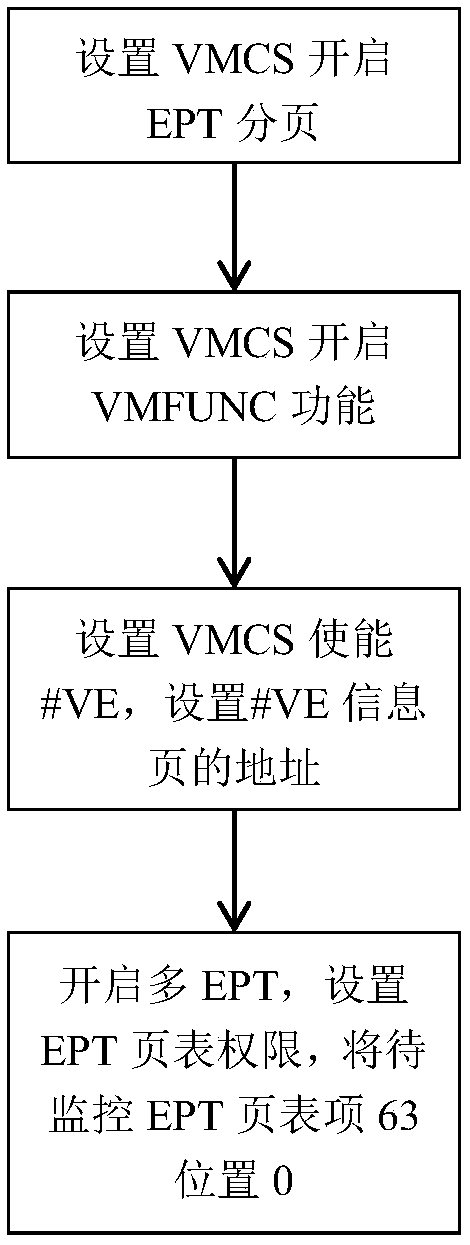
[0030] 1. To initialize the hypervisor, configure the EPT, #VE and VMFUNC functional environments provided by the hardware during the hypervisor initialization;
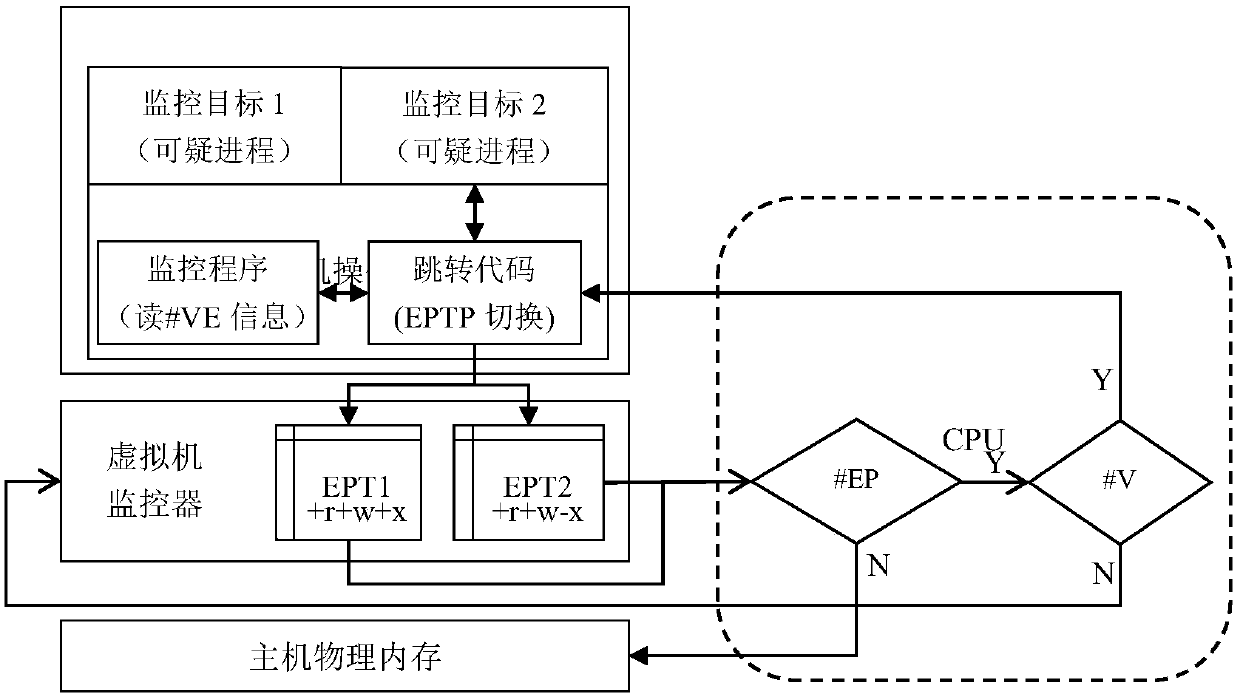
[0031] 2. Use multiple EPT page tables to achieve security isolation between the monitoring program and the monitoring target. By setting the permissions of the EPT page table items of the target to be monitored, and loading the jump code when the virtual machine kernel is initialized, the security monitoring inside the virtual machine is realized;
[0032] 3. When the protected EPT page table is written or executed, the #VE exception is triggered. At this time, the execution is transferred to the monitoring program through the jump code, and the monitoring program uses the abnormal information to analyze the abnormal event and make a further response , complete #VE exception hand...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com