Data verification via the device's independent processor
A technology of processors and electronic equipment, applied in data processing applications, digital data protection, instruments, etc., can solve problems such as surge
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
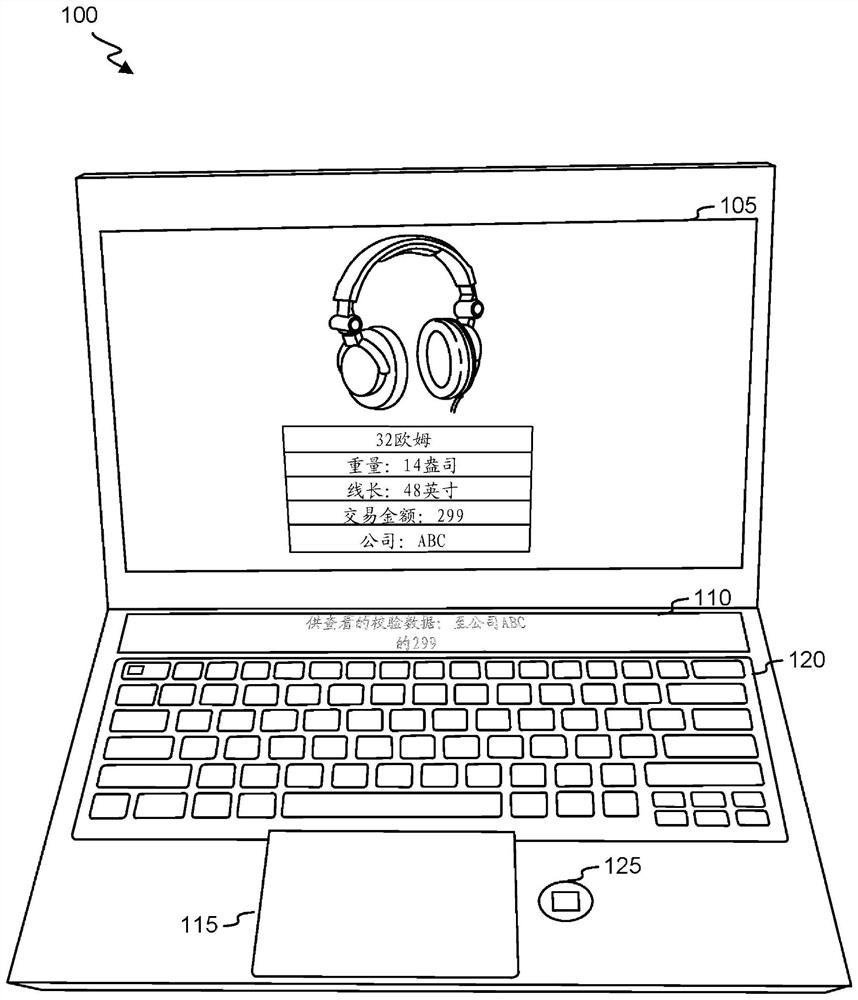
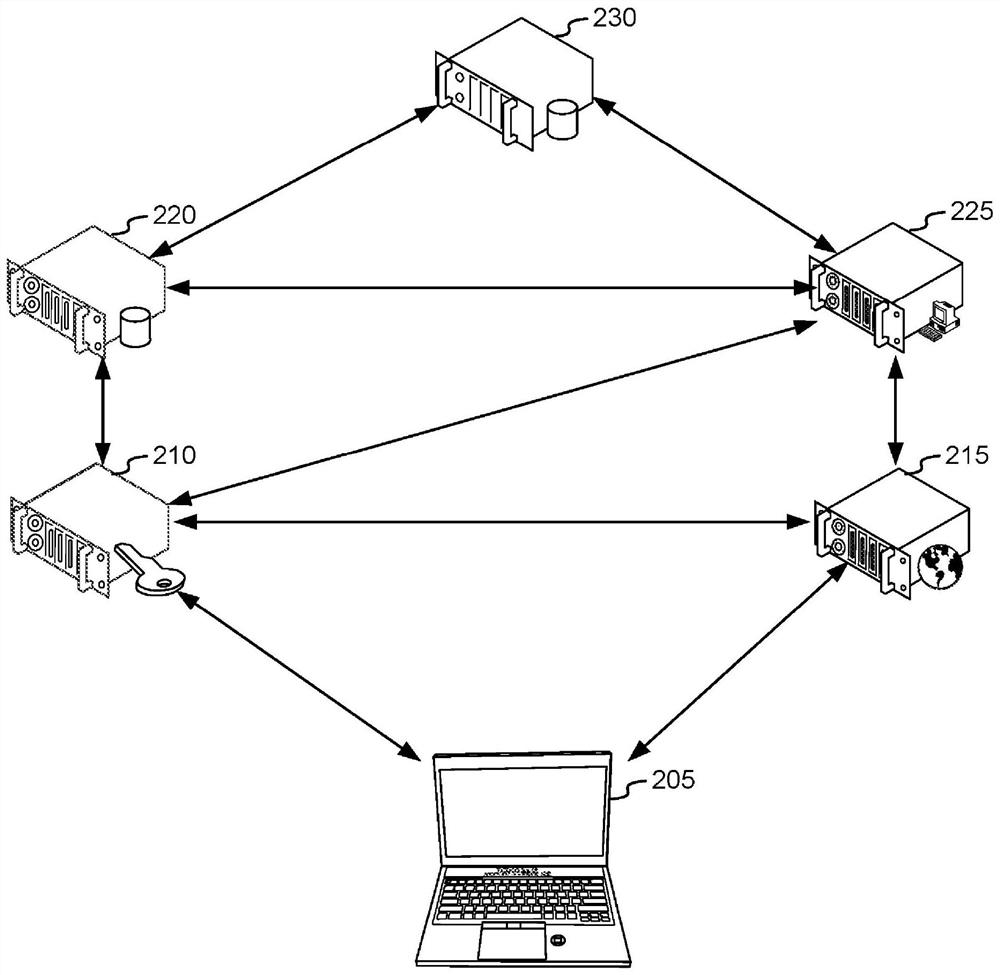
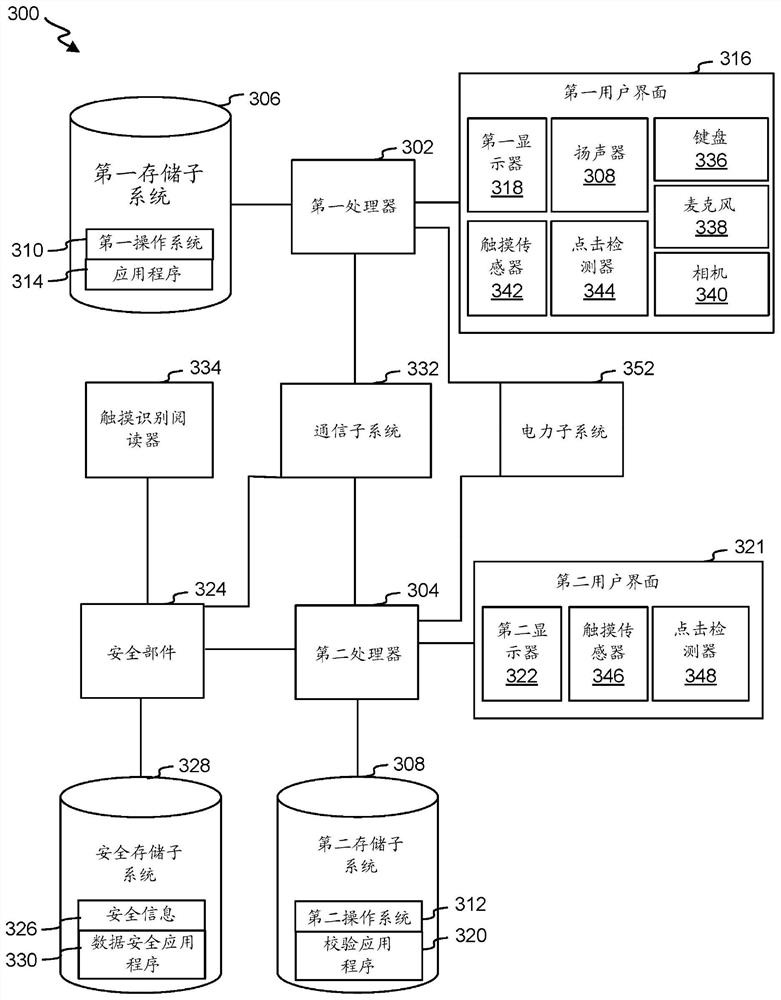
[0011] In some embodiments, the physical architecture can be configured such that a first (eg, primary) operating system is executable by a first processor of the device, and a separate secure operating system is executable by a second processor of the device. The first processor may control output of first data to a first display of the device, and the second processor may control output of second data to a second display of the device. In some cases, the first display may be configured such that presentation at the first display may not be controlled, initiated, and / or modified by the second processor, and / or the second processor may be configured such that presentation at the second display The presentation of may not be controlled, initiated and / or modified by the first processor. Thus, in some implementations, a display, eg, the second display, may only be controlled by a corresponding processor, eg, the second processor. The first data and the second data may relate to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com