A Mutual Trust Cluster Collaborative Authentication Method for Anonymous Authentication in Vehicle Networks
An anonymous authentication and collaborative verification technology, which is applied in the field of security authentication and privacy protection of vehicle-mounted ad hoc networks, and can solve problems such as large vehicle space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
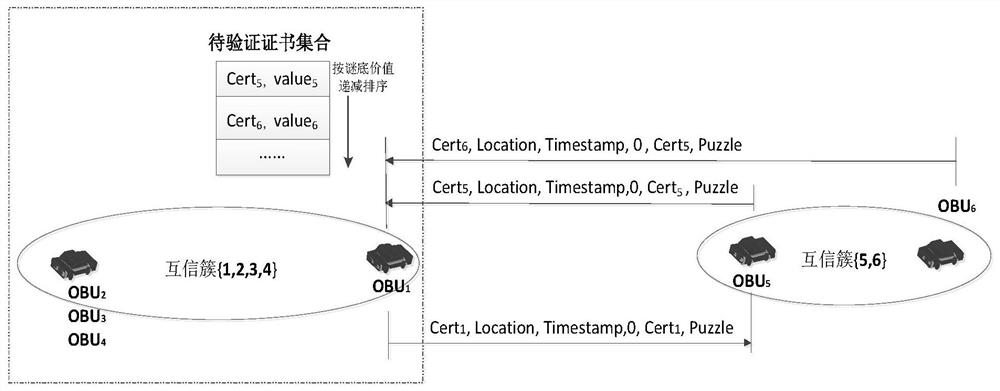
[0047] The present invention is realized in the following ways. First, relevant information is added to the puzzle design according to the real-time driving situation of the vehicle, so as to limit attackers from constructing hash puzzles in advance. Second, in the certificate issuance stage, the mutual trust cluster collaborative verification is used to integrate computing resources between legal vehicles, which improves the efficiency of certificate verification.
[0048] 1. Puzzle Design
[0049] The classic hash puzzle consists of two parts, namely the message and the puzzle. The value of the answer is evaluated by the length of the binary string obtained after hash mapping with all zeros. That is, it is assumed that
[0050]
[0051] Based on the one-way nature of the hash operation, the possibility of using the construction method to generate a puzzle that meets this condition is negligible, that is, it is assumed that the vehicle can only rely on parameter traversal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com