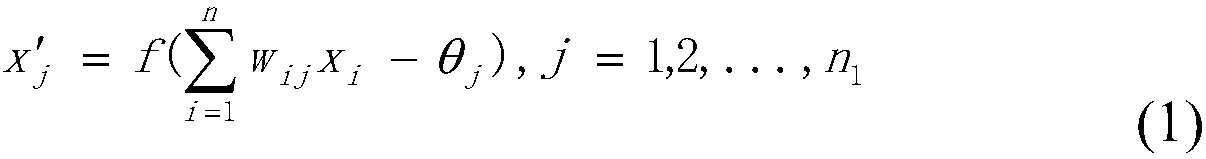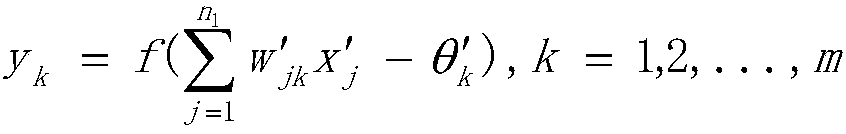Identification method of crank call
A technology of harassing calls and identification methods, applied in the field of communication big data, can solve problems such as the flood of harassing calls and life troubles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
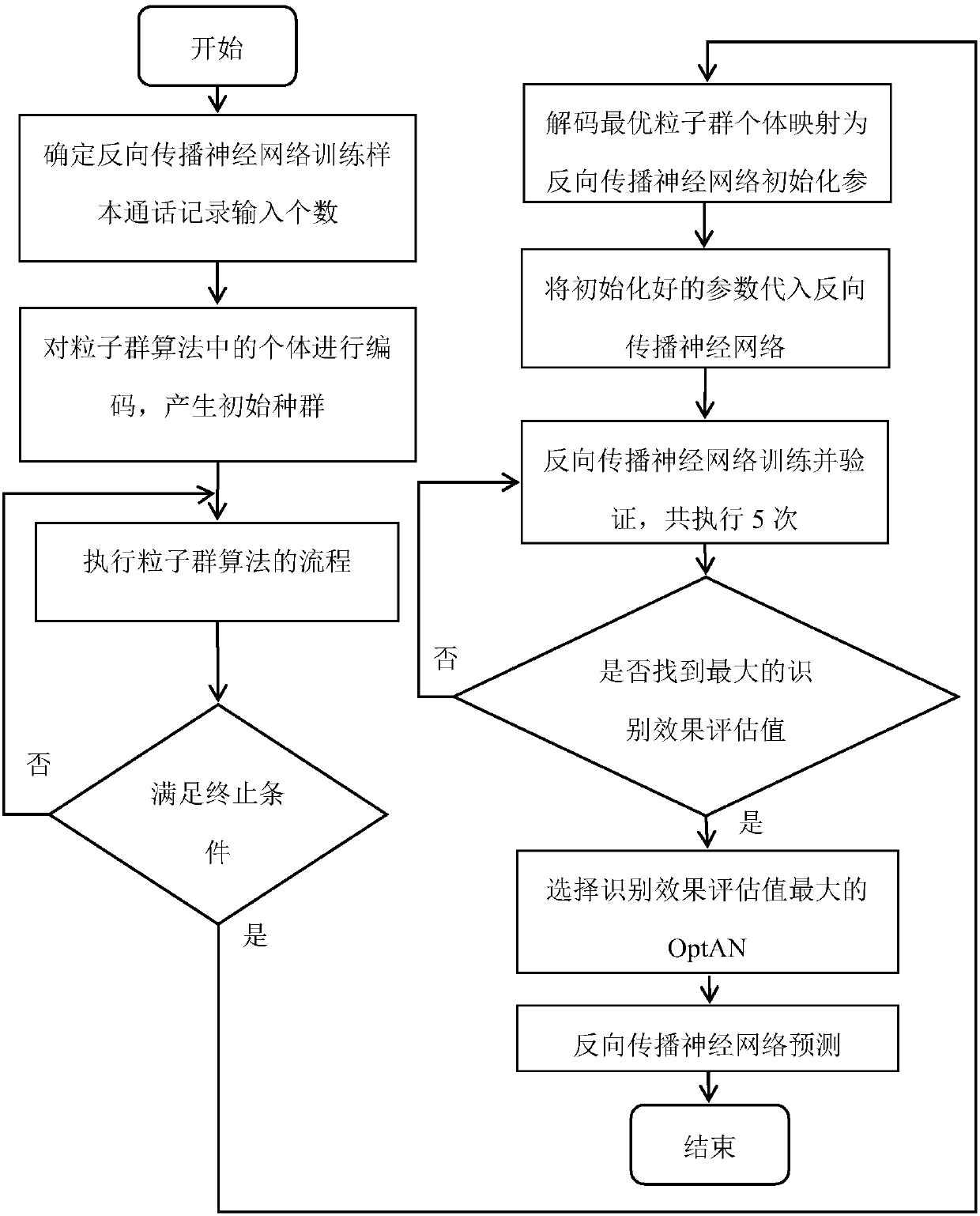
[0065] The specific implementation manner of the present invention is described in conjunction with the description of the accompanying drawings. In order to prove the superiority of the present invention, the present invention performs experimental simulation recognition on call records. The concrete implementation example implementation steps of a kind of harassing call identification method of the present invention are as follows:
[0066] S1. Perform data processing on the acquired original call record data, including data noise reduction, abnormal data identification and repair, and normalization. After 7 consecutive days of call record data are used as training samples and test samples.
[0067] S2. Establish a harassing call identification model based on the backpropagation neural network:
[0068]
[0069] where x 1 ,x 2 ,..,x n is the input variable, n=13 is the number of input layer nodes, n 1 =8 is the number of hidden layer nodes, w ij (0≤w ij ≤1, i=1,2,…,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com