Face recognition algorithm evaluation method suitable for public security combats
A face recognition and evaluation method technology, applied in character and pattern recognition, computing, computer parts and other directions, can solve the problems of simplified test difficulty, high algorithm performance, and inability to test algorithm characteristics, and achieve scientific and feasible evaluation results. The effect of high reliability and good practical operability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in detail below with reference to the drawings and specific embodiments. This embodiment is implemented on the premise of the technical solution of the present invention, and provides detailed implementation and specific operation procedures, but the protection scope of the present invention is not limited to the following embodiments.
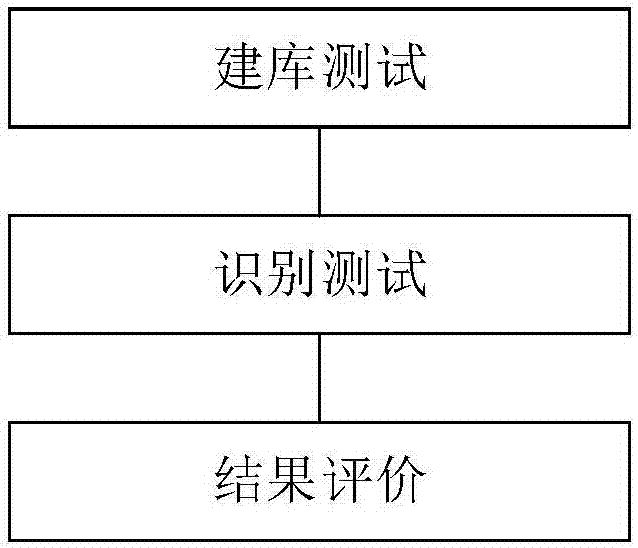
[0057] A face recognition algorithm evaluation method suitable for public security actual combat, such as figure 1 Shown, including:
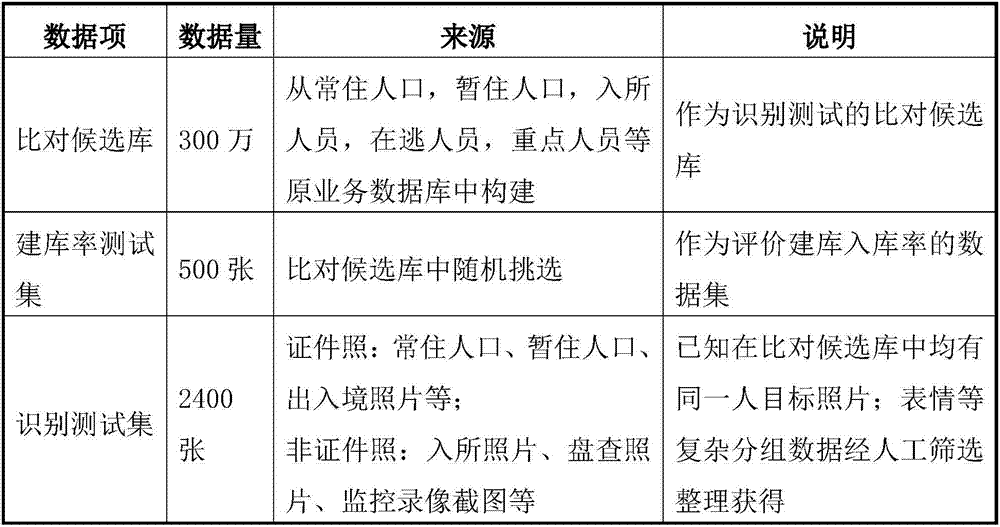
[0058] Library building test: Input the sample picture database, build a portrait library by the program equipped with the algorithm to be tested, and collect the library building speed and storage rate of the program;
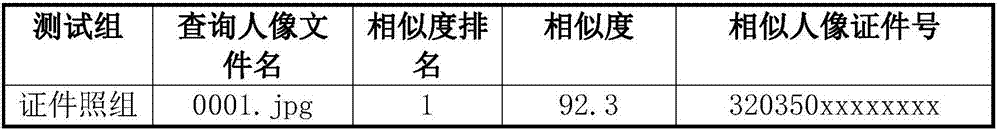
[0059] Recognition test: input multiple pictures to be recognized, and the program selects the closest set number of pictures for each picture to be recognized from the portrait library created by the program, that is, a 1:N test method is adopted;
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com