Application access method, device, server and computer storage medium
A technology of application access and access request, applied in computer security devices, calculations, instruments, etc., can solve problems such as code redundancy accumulation, heavy repetitive workload, and inconvenient maintenance, so as to reduce development costs, improve development efficiency, and reduce development costs. The effect of edition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
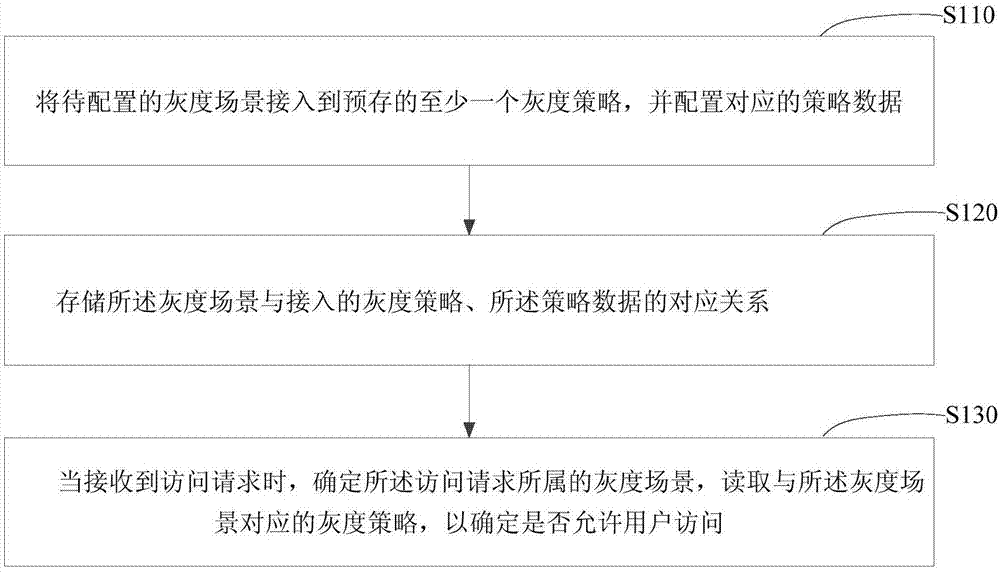
[0051] figure 1 It is a flow chart of an application access method in Embodiment 1 of the present invention. This embodiment is applicable to the case of accessing applications in grayscale scenarios. The method can be executed by an application access device, and specifically includes the following steps:
[0052] S110. Connect the to-be-configured grayscale scene to at least one prestored grayscale policy, and configure corresponding policy data.
[0053]Among them, the grayscale scene may be a business scene that is only opened or configured for some users when performing a certain operation, displaying a certain application, or using a certain function, rather than for all users. Exemplarily, a website or a client needs to display a new function to some specific users, or only specified users are required to use the new function, which is a grayscale scenario. The grayscale strategy is a method used in the implementation of grayscale scenarios. Specifically, it can be how...
Embodiment 2
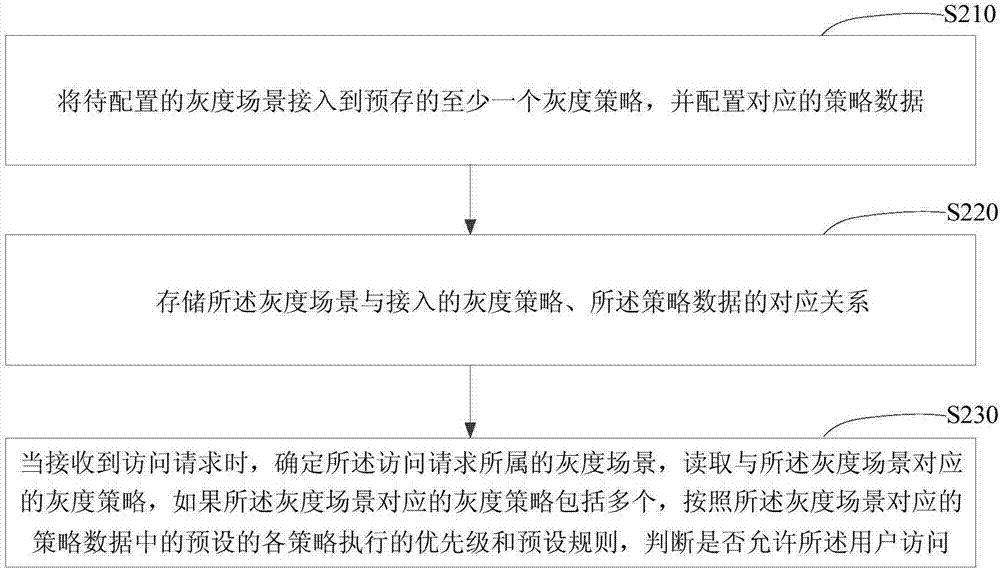
[0075] figure 2 It is a flowchart of an application access method in Embodiment 2 of the present invention. On the basis of the above-mentioned embodiments, this embodiment provides an application access method when the gray-scale policy corresponding to the gray-scale scene includes multiple policies. In an implementation manner, the application access method includes:
[0076] S210. Connect the grayscale scene to be configured to at least one prestored grayscale strategy, and configure corresponding strategy data;
[0077] S220. Store the corresponding relationship between the grayscale scene, the accessed grayscale policy, and the policy data;
[0078] S230. When an access request is received, determine the grayscale scene to which the access request belongs, and read the grayscale policy corresponding to the grayscale scene. If the grayscale policy corresponding to the grayscale scene includes multiple policies, According to the policy execution priority and judgment ru...
Embodiment 3
[0087] This embodiment provides an application access device, Figure 4 It is a schematic structural diagram of an application access device in Embodiment 3 of the present invention, and the device includes:
[0088] A strategy configuration module 410, configured to connect the grayscale scene to be configured to at least one prestored grayscale strategy, and configure corresponding strategy data;
[0089] A storage module 420, configured to store the corresponding relationship between the grayscale scene, the accessed grayscale policy, and the policy data;
[0090] The access determination module 430 is configured to determine the grayscale scene to which the access request belongs when receiving an access request, and read the grayscale policy corresponding to the grayscale scene to determine whether the user is allowed to access;
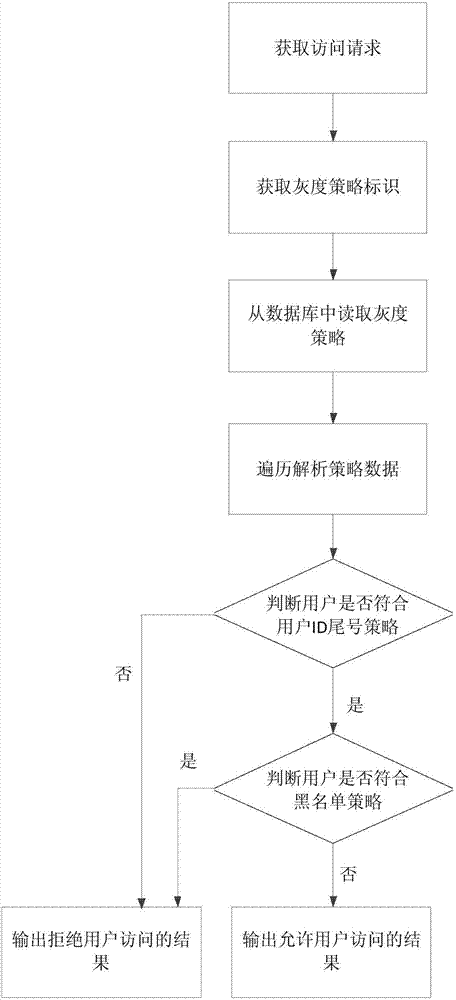
[0091] Wherein, the pre-stored gray scale policy includes: at least one of user ID preset digit number policy, white list policy, black list p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com