System and method of obfuscation through binary and memory diversity
A binary file, binary code technology, applied in the field of systems and methods for obfuscation through binary and memory diversity, can solve problems such as increasing manufacturing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
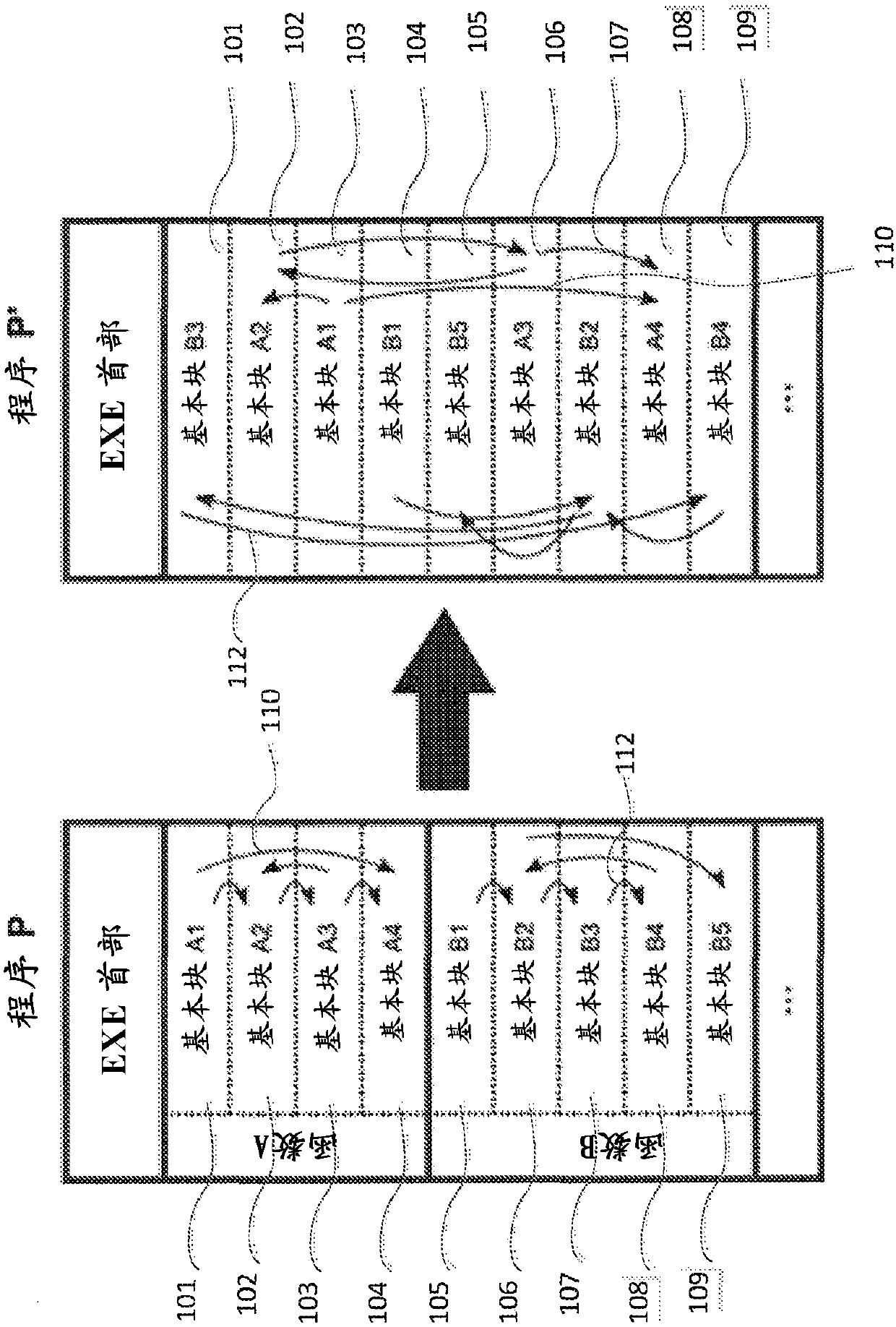
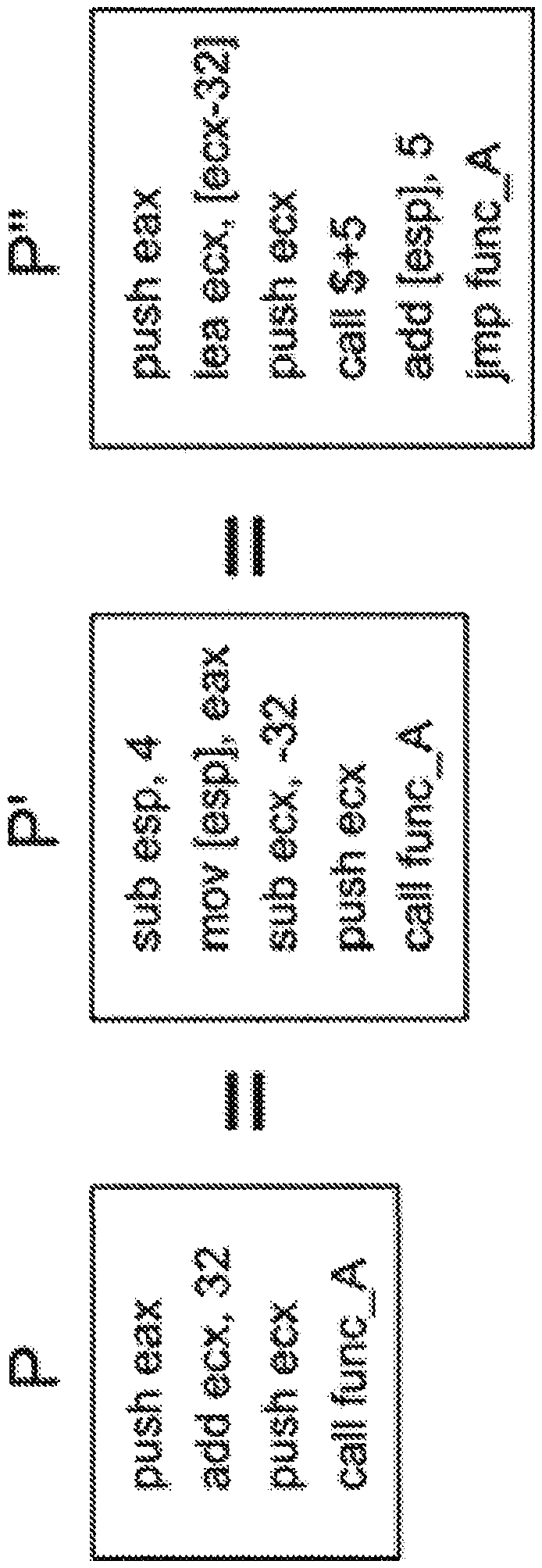
[0032] The systems and methods of the present disclosure can create a security layer for an OS by randomizing kernel code locations and memory locations. For example, nearly 80% of recent code execution exploits in the Linux kernel are sensitive to pointers and code addresses in the kernel. Unpredictable code locations and pointer changes can seriously hamper the productivity of exploit authors. If an attacker can figure out how to exploit a vulnerability, the usefulness of the OS will be very limited.
[0033] When using the systems or methods of the present disclosure, each successive instance of an OS (next router, cloud virtual machine, etc.) can have a completely different and random organization. Assuming that the Linux kernel has over 37,000 files and 15 million lines of code, there are enough building blocks to create trillions of combinations to create kernel diversity according to this disclosure.
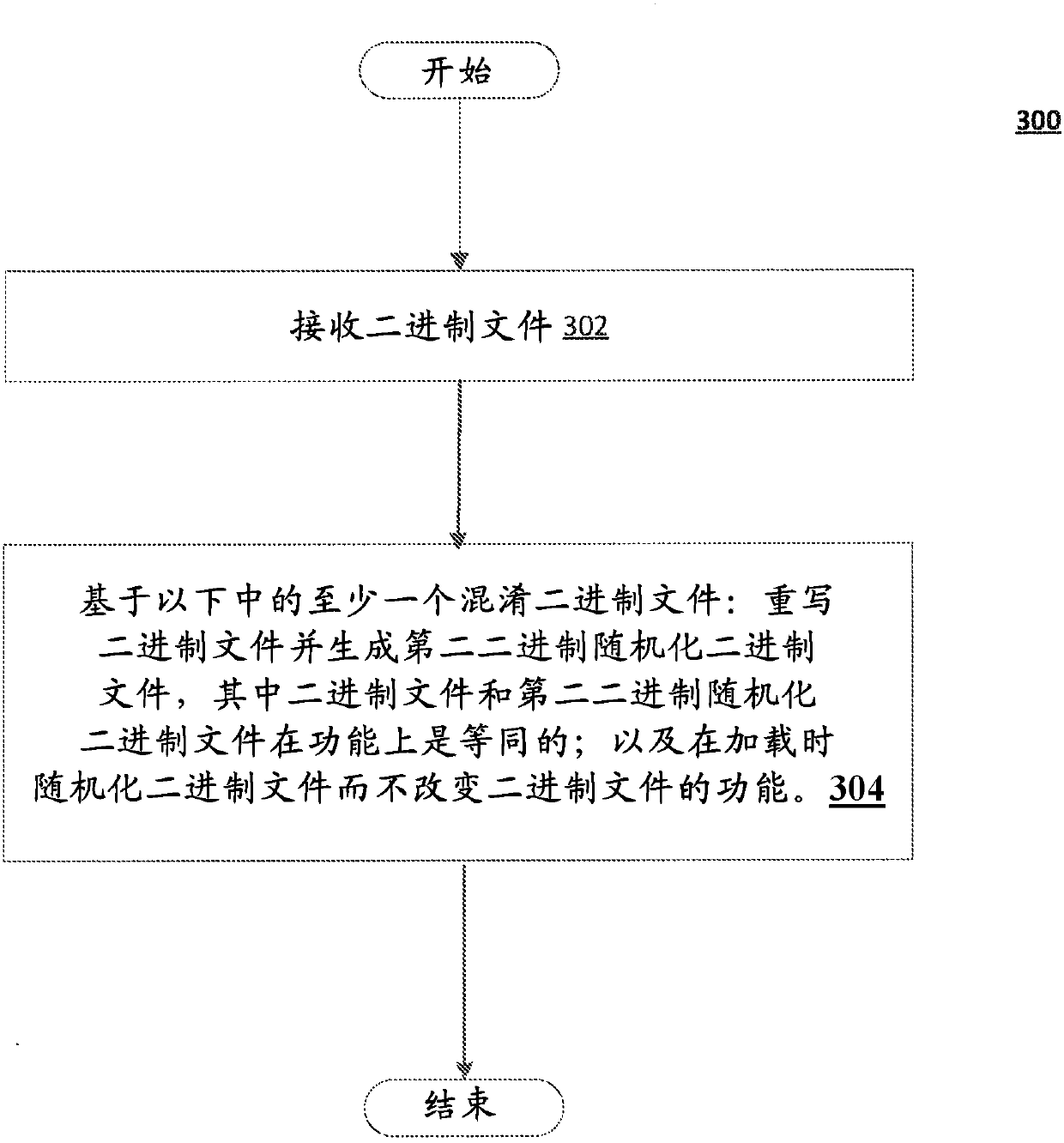
[0034] The systems and methods of the present disclosure may inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com