A kind of SDN-based video surveillance network security control method and system
A network security and video surveillance technology, applied in the field of network communication, can solve problems such as complex configuration, high professional requirements, and inability to achieve precise protection, so as to reduce maintenance costs, improve real-time performance, and avoid professional effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] Embodiment 1, adding monitoring equipment, setting the access control list from the monitoring equipment to the management server.
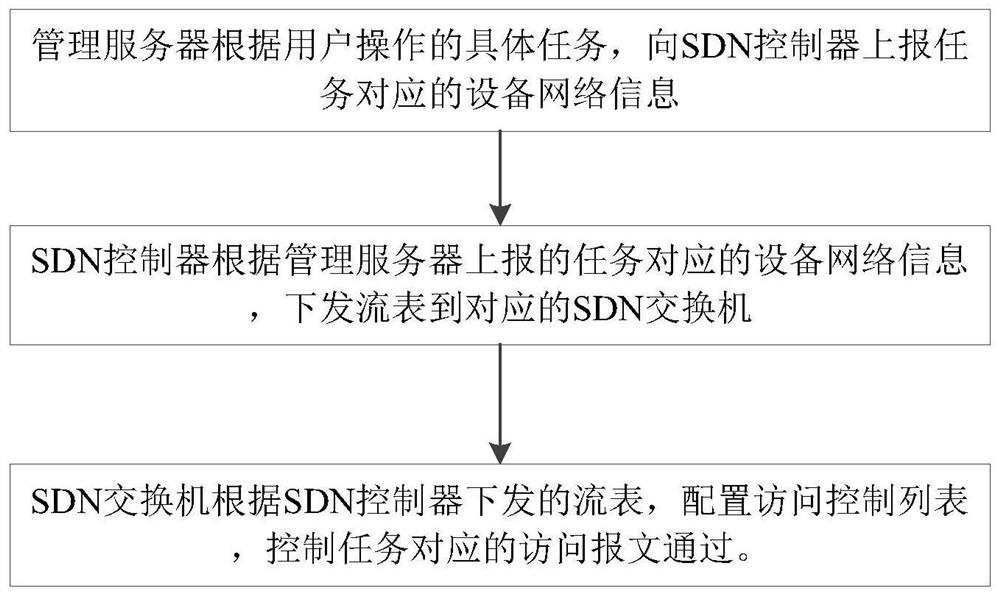
[0044]In this embodiment, the specific task of the user operation is to add a monitoring device. Usually, the user connects to the video management server on the management client and adds monitoring devices such as IPC, NVR or business client PC. Before adding the monitoring device, the SDN switch The access control list is configured so that all monitoring device registration packets cannot be sent to the VM, which can be understood as the initial configuration. After the user executes adding monitoring equipment, this embodiment includes the following steps:
[0045] The management server reports its own network information to the SDN controller according to the operation tasks of adding monitoring equipment by the user;
[0046] According to the self-network information reported by the management server, the SDN controller sends a flo...
Embodiment 2
[0053] Embodiment 2, adding monitoring equipment, setting the access control list from the management server to the monitoring equipment.
[0054] In this embodiment, the specific task of the user operation is to add monitoring equipment. Usually, the user connects to the video management server on the management client and adds monitoring equipment such as IPC, NVR or business client PC. Before adding equipment, the SDN switch The access control list is configured to block all packets sent to the device except the management client, which can be understood as the initial configuration. After the user executes adding equipment, this embodiment includes the following steps:
[0055] The management server reports its own network information to the SDN controller according to the operation tasks of adding monitoring equipment by the user;
[0056] According to the self-network information reported by the management server, the SDN controller issues a flow table to notify the SDN...
Embodiment 3
[0060] Embodiment 3, adding the business client area, setting the access control list that the business client sends to the management server.
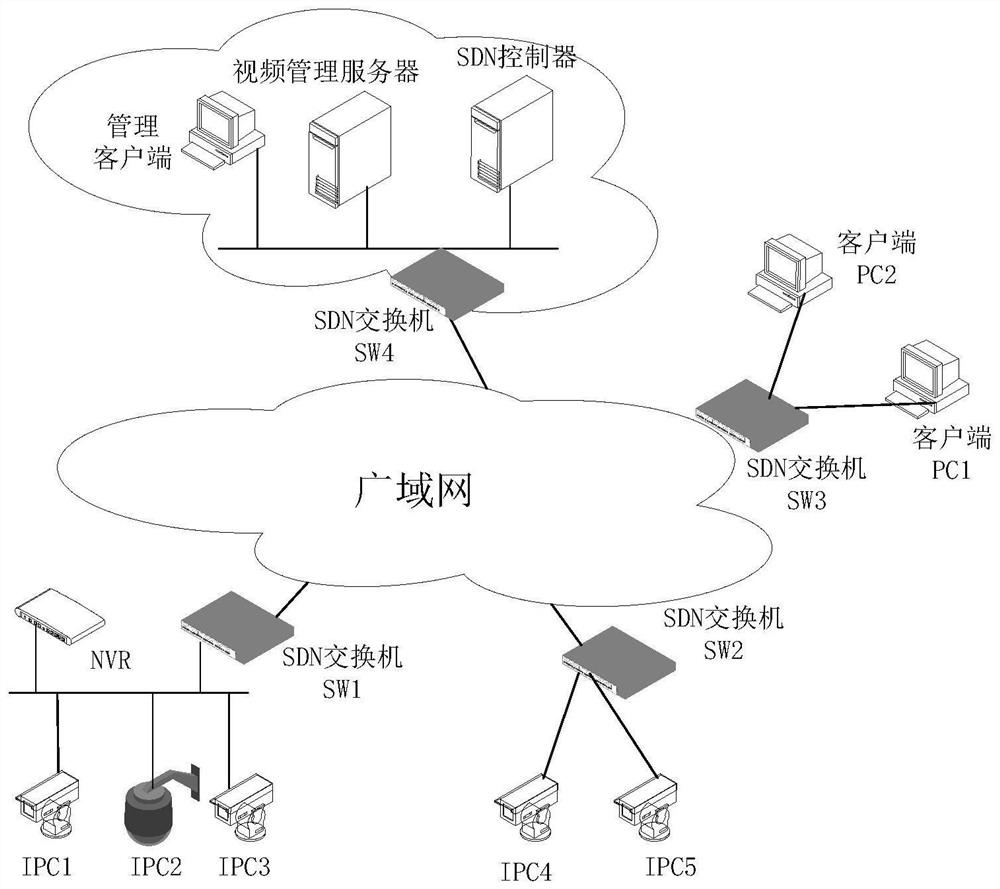
[0061] In this embodiment, the specific task of the user operation is to add the SDN switch corresponding to the service client, and the service client is in figure 1 In the middle are PC1 and PC2, which are clients in the network for users to view video surveillance. They all access the video surveillance network through an SDN switch. It is necessary to set the access control list on the SDN switch that the business client accesses to the video surveillance network. On the video management server, the operation can be performed by adding the area where the business client is located. This embodiment includes the following steps:
[0062] The management server reports the area information of the business client to the SDN controller according to the area where the business client is added by the user;
[0063] The SDN controller fin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com