Global characteristic visulization and local characteristic combined malicious code classification method
A malicious code and local feature technology, applied in the field of malicious code classification, can solve the problems of lack of intermediate layer abstraction, overall texture change, image instability, etc., to achieve a model fault tolerance rate, small texture gray level difference, and improve classification accuracy rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in detail below with reference to the accompanying drawings and examples.
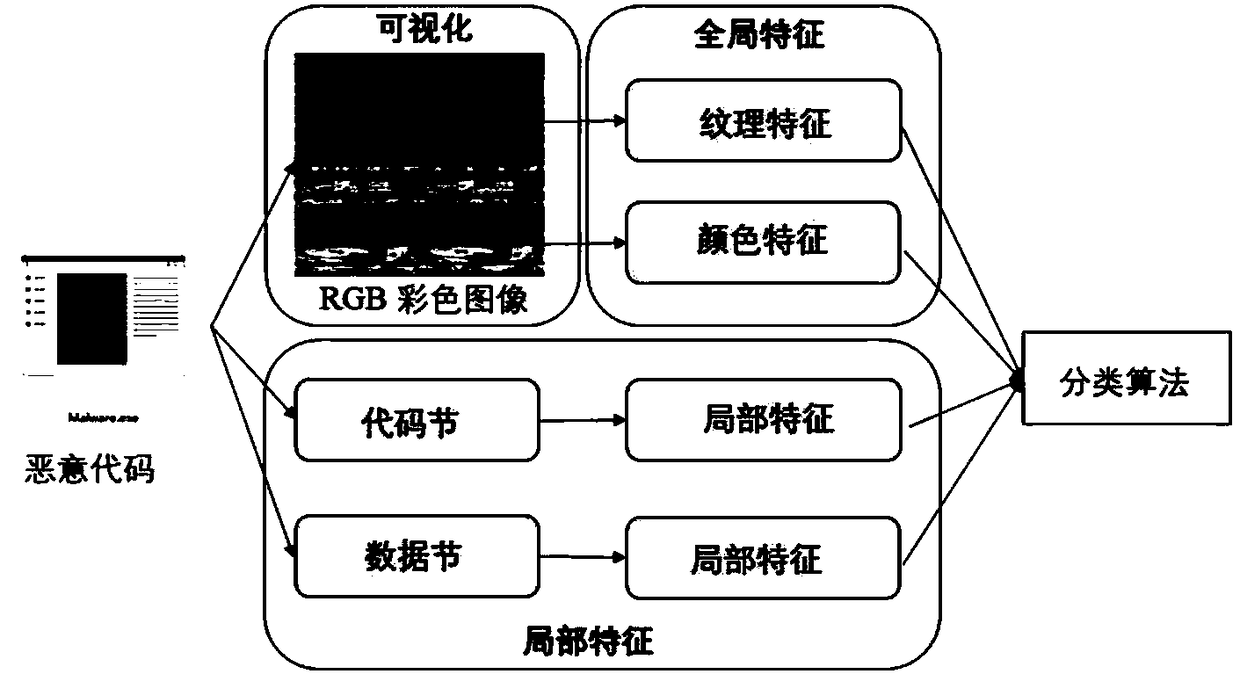
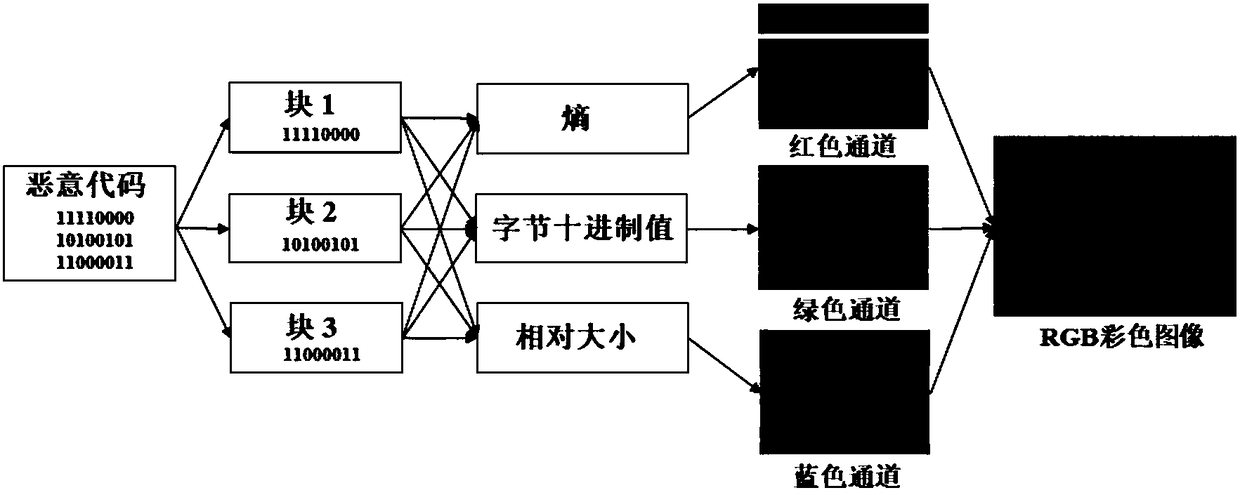
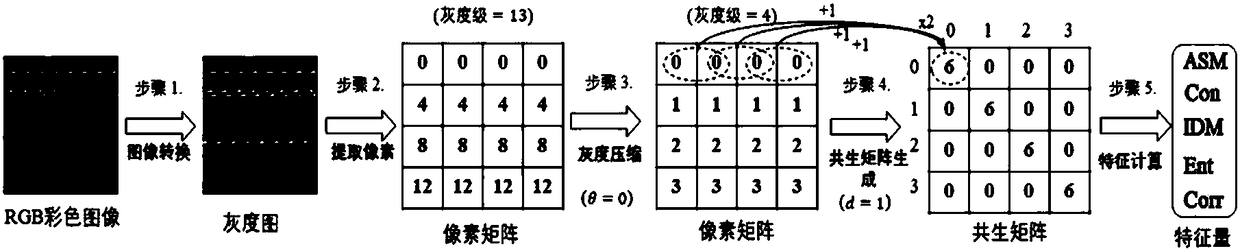
[0049] The present invention provides a malicious code classification method combining global feature visualization and local features. The basic idea is: divide the malicious code binary file into blocks, calculate three feature values for each block, and fill a corresponding feature value for each block. color channel, thereby visualizing the malicious code binary file into an RGB color image; the three eigenvalues include the eigenvalues that reflect the overall characteristics and internal characteristics of the block; then, extract the global characteristics of the RGB color image, and simultaneously extract the Extract local features in the area; combine the extracted global features and local features to classify malicious code families.
[0050] It can be seen that the present invention realizes the classification of malicious code families b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com