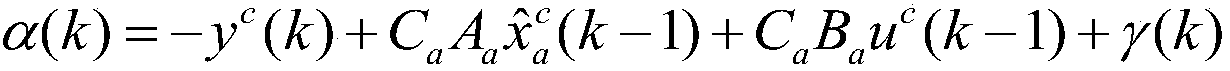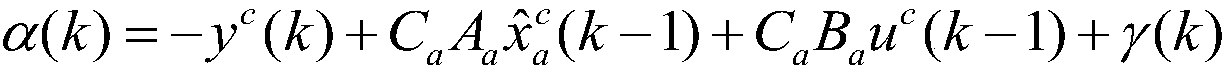False data injection attack method based on imprecise mathematical model
A mathematical model and injection attack technology, which is applied to instruments, adaptive control, control/regulation systems, etc., can solve problems such as it is difficult for attackers to establish mathematical models
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be described in detail below with reference to the accompanying drawings and examples.
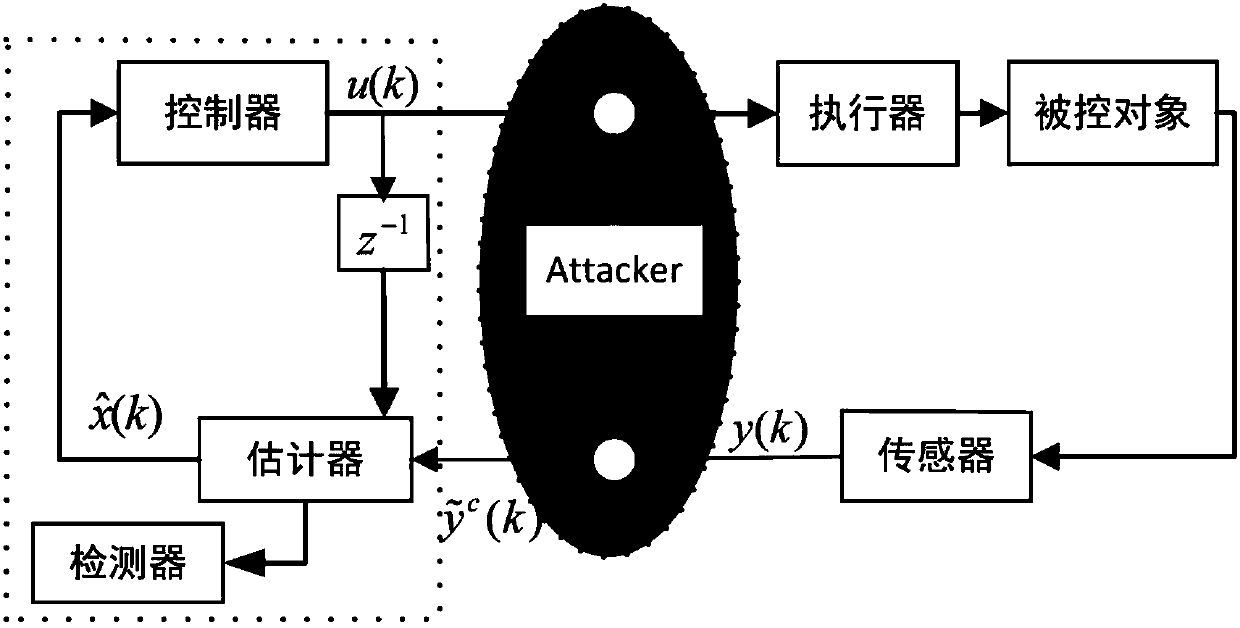
[0017] The invention provides a false data injection attack method based on an imprecise mathematical model. The design principle of the method is: from the perspective of the attacker, design a false data attack sequence according to the identified imprecise mathematical model, aiming at destroying the control system. performance without being detected by the detector.
[0018] First of all, it needs to be explained that the controlled object model in the present invention is a linear discrete time-invariant system
[0019]
[0020] where x(k)∈R n is the state vector, u(k)∈R m is the input vector, y(k)∈R q is the output vector, ω(k) and υ(k) are independent Gaussian white noise with zero mean covariance Q and R respectively, n, m, q represent the dimensions of the state vector, input vector, and output vector, respectively, A, B, C are the model pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com