Malicious traffic detection method, system and apparatus, and computer readable storage medium
A detection method and malicious traffic technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems of unstable detection and classification results, low accuracy of cluster analysis, dependence, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
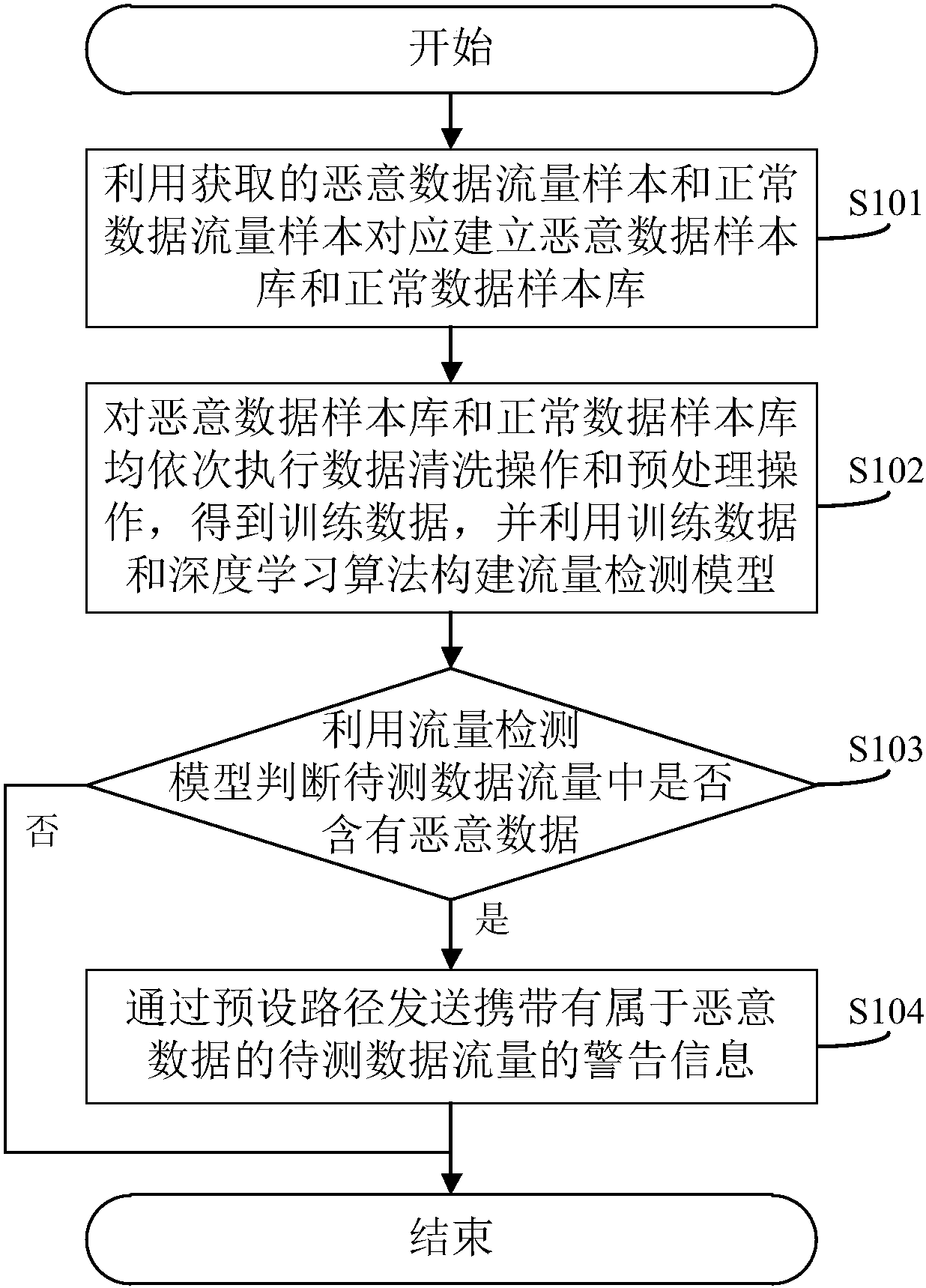
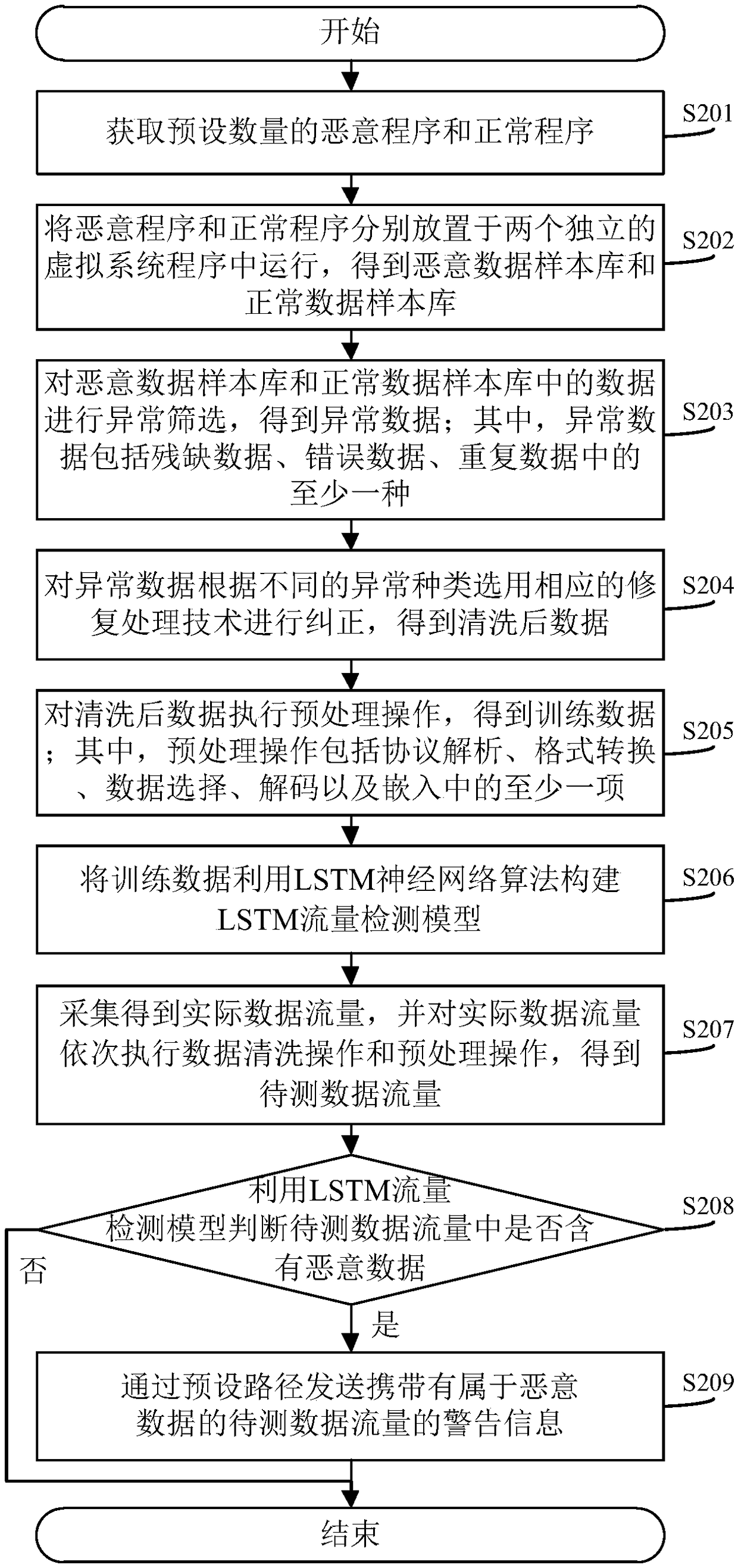
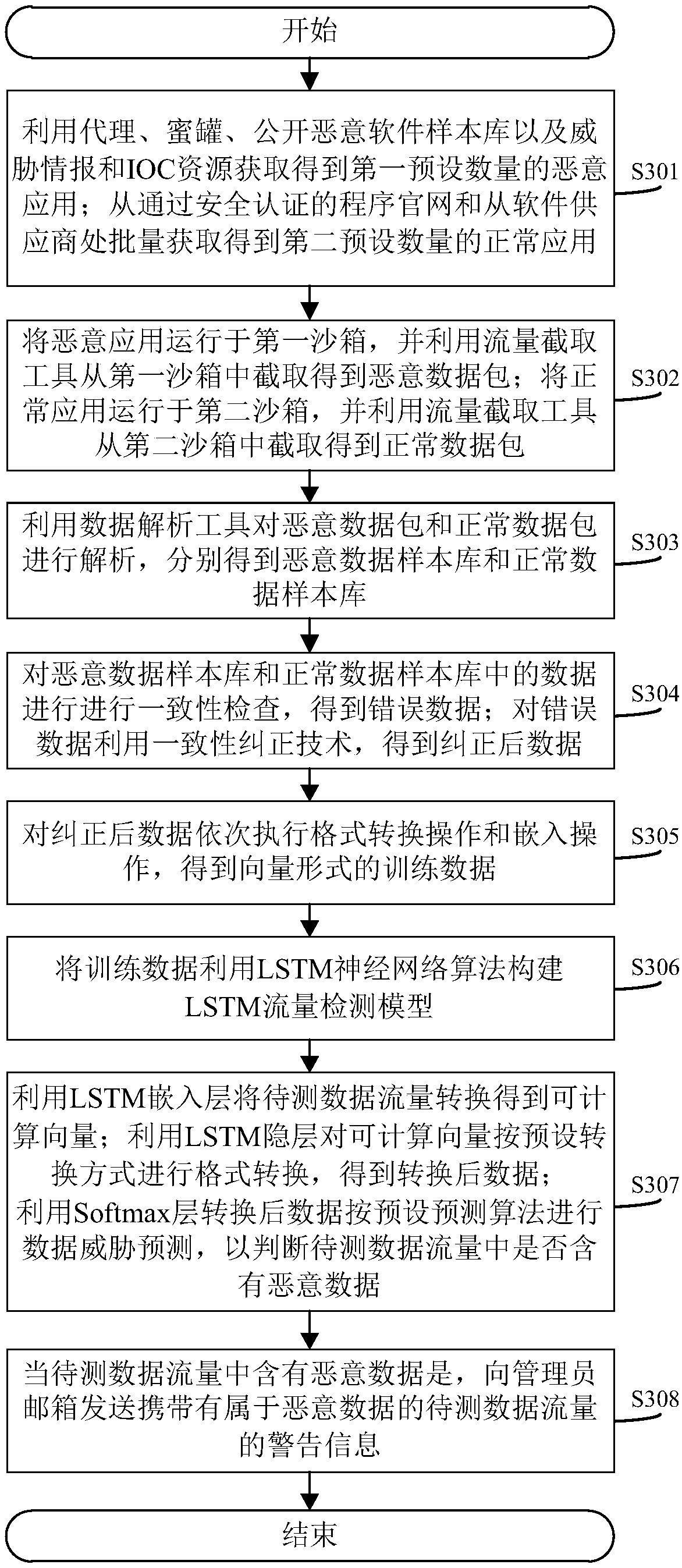
[0090] The core of this application is to provide a method, system, device, and computer-readable storage medium for detecting malicious traffic. The corresponding data sample database is established from the obtained malicious data traffic sample and the normal data traffic sample, and the data sample database is used Data traffic with different threat levels is trained in combination with deep learning algorithms to obtain a traffic detection model with significant classification effect, which can be used to better judge whether the actual data traffic to be tested contains malicious traffic. Take full advantage of the automatic learning features of deep learning algorithms, and perform feature learning and training from the normal and malicious data sample library provided, without consuming valuable human resources to complete the feature information extraction operation, significantly improving work efficiency and increasing malicious traffic The accuracy of discrimination ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com