Data collection method and apparatus, terminal device and storage medium
A data collection and database technology, applied in the computer field, can solve the problems of low data security, reduce the risk of leakage, avoid decryption, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
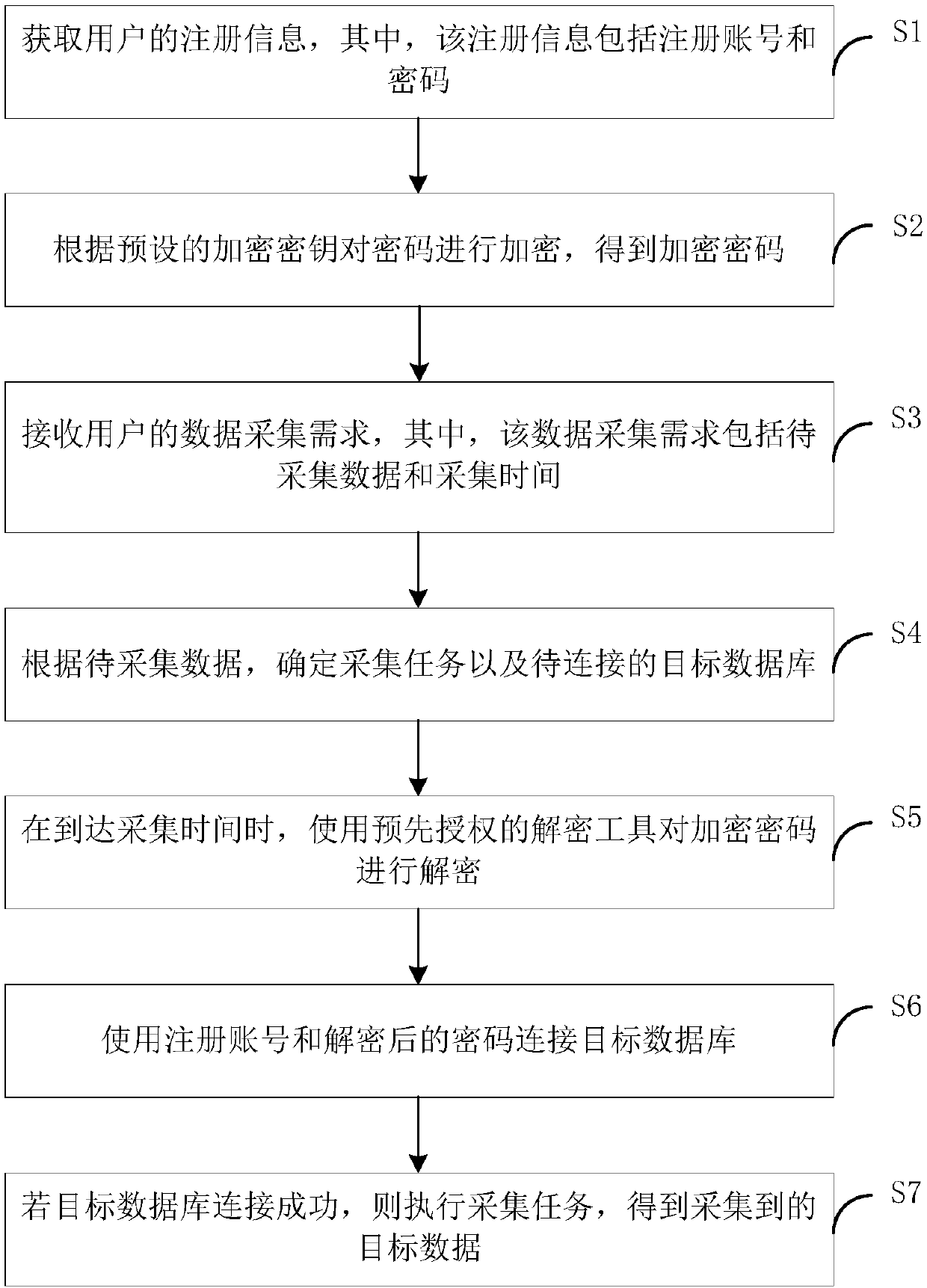
[0033] see figure 1 , figure 1 The implementation flow of the data collection method provided by the embodiment of the present invention is shown. The data collection method is applied in the data collection systems of various enterprises and institutions to prevent passwords from being illegally stolen during data collection and improve data security. like figure 1 As shown, the data collection method includes steps S1 to S7, detailed as follows:
[0034] S1: Obtain the registration information of the user, where the registration information includes a registration account number and a password.
[0035] In the embodiment of the present invention, the registration information may specifically be the information included in the employee account issued by the enterprise or institution, or the information filled in when an individual who has passed the review of the data collection system administrator applies for an account registration.
[0036] The registration informatio...
Embodiment 2
[0126] Corresponding to the data collection method in embodiment 1, Image 6 A data collection device corresponding to the data collection method provided in Embodiment 1 is shown. For convenience of description, only parts related to the embodiment of the present invention are shown.
[0127] like Image 6 As shown, the data collection device includes an information acquisition module 60 , a password encryption module 61 , a demand customization module 62 , a task determination module 63 , a password decryption module 64 , a database connection module 65 and a data collection module 66 . Among them, an information acquisition module 60 , a password encryption module 61 , a demand customization module 62 , a task determination module 63 , a password decryption module 64 , a database connection module 65 and a data collection module 66 . The detailed description of each functional module is as follows:
[0128] An information acquisition module 60, configured to acquire user ...
Embodiment 3
[0154] This embodiment provides a computer-readable storage medium, and a computer program is stored on the computer-readable storage medium, and when the computer program is executed by the processor, the data acquisition method in Embodiment 1 is realized, or, the computer program is executed by the processor Realize the functions of each module / unit in the data acquisition device in Embodiment 2 at the same time, in order to avoid repetition, no more details are given here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com